Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
How to obtain this file:<br />
1. When WINNT is installed, a copy <strong>of</strong> the password database (SAM file) is created in the<br />
c:\WINNT\repair directory. This copy only contains the passwords by default created during the set<br />
up, meaning only the administrator's password. When the administrator updates the repair disk, the<br />
SAM file is also updated (in this case, the SAM file contains all the accounts). So we could get the<br />
SAM file from the repair file, as this one is not locked by the core. If the repair file does not have the<br />
SAM file, there is still another way <strong>of</strong> obtaining it.<br />
2. The PC has to be booted from a start disk or from another operating system. This way, WINNT is<br />
not executed and so the SAM file is not locked. We can then copy the SAM file onto a disk and<br />
crack it later on.<br />
The Sam file is not the only medium that can allow you to find passwords on a network using NT.<br />
Let us take the L0phtCrack tool, which is the fastest and the most efficient to find NT passwords,<br />
because it does not only use the SAM file to have the password hashing, but also uses the encrypting<br />
vulnerabilities seen previously.<br />
You can find an LC3 evaluation version at: http://www.atstake.com/research/lc3/download.html.<br />
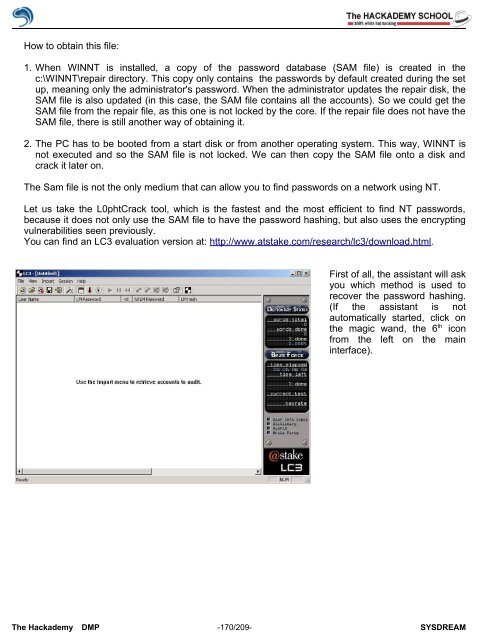
First <strong>of</strong> all, the assistant will ask<br />
you which method is used to<br />
recover the password hashing.<br />
(If the assistant is not<br />
automatically started, click on<br />
the magic wand, the 6 th icon<br />
from the left on the main<br />
interface).<br />
The <strong>Hack</strong>ademy DMP -170/209- SYSDREAM