You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
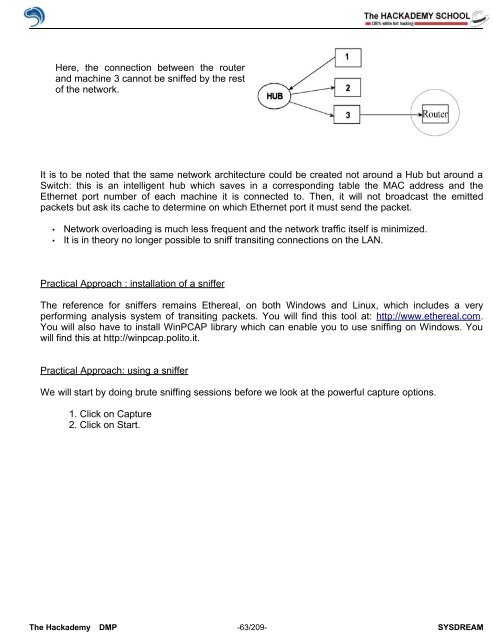
Here, the connection between the router<br />
and machine 3 cannot be sniffed by the rest<br />
<strong>of</strong> the network.<br />
It is to be noted that the same network architecture could be created not around a Hub but around a<br />
Switch: this is an intelligent hub which saves in a corresponding table the MAC address and the<br />
Ethernet port number <strong>of</strong> each machine it is connected to. Then, it will not broadcast the emitted<br />
packets but ask its cache to determine on which Ethernet port it must send the packet.<br />
• Network overloading is much less frequent and the network traffic itself is minimized.<br />
• It is in theory no longer possible to sniff transiting connections on the LAN.<br />
Practical Approach : installation <strong>of</strong> a sniffer<br />
The reference for sniffers remains Ethereal, on both Windows and Linux, which includes a very<br />
performing analysis system <strong>of</strong> transiting packets. You will find this tool at: http://www.ethereal.com.<br />
You will also have to install WinPCAP library which can enable you to use sniffing on Windows. You<br />
will find this at http://winpcap.polito.it.<br />
Practical Approach: using a sniffer<br />
We will start by doing brute sniffing sessions before we look at the powerful capture options.<br />
1. Click on Capture<br />
2. Click on Start.<br />
The <strong>Hack</strong>ademy DMP -63/209- SYSDREAM