You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
B) DNS hijacking<br />
The DNS protocol is destined to resolve a host name, for example www.thehackademy.net into an IP<br />
address, in order to establish a direct communication with the server in question. The DNS protocol's<br />
format is as follows:<br />
The standard host name resolution procedure is the following one:<br />
1) The client sends a DNS request to the name server in order to resolve the name www.serv.com<br />
into its IP address.<br />
2) The DNS server quizzes the serv.com domain DNS in order to determine the IP <strong>of</strong> machine www.<br />
3) The DNS server sends back the IP address associated to www.serv.com to the client through a<br />
DNS answer.<br />
The principle <strong>of</strong> DNS hijacking will therefore be to hijack a DNS response to replace the server IP to<br />
which the victim wishes to connect with the hacker's. He will then be able to freely emulate a site to<br />
recover information (access codes, ...) or simply forward the connection to the server so as to spy on<br />
the communication.<br />
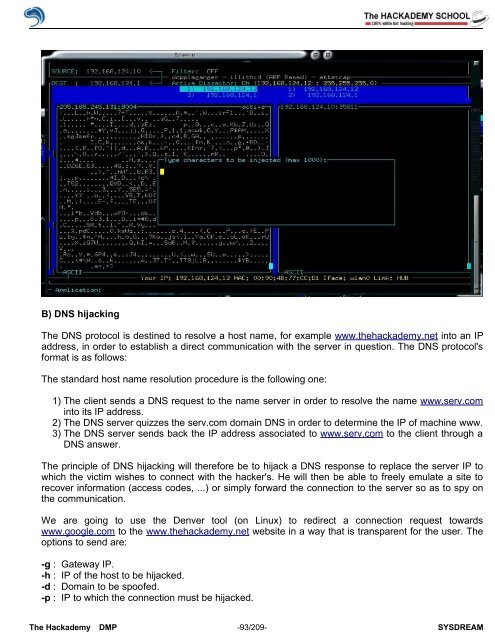
We are going to use the Denver tool (on Linux) to redirect a connection request towards<br />
www.google.com to the www.thehackademy.net website in a way that is transparent for the user. The<br />
options to send are:<br />
-g : Gateway IP.<br />
-h : IP <strong>of</strong> the host to be hijacked.<br />
-d : Domain to be spo<strong>of</strong>ed.<br />
-p : IP to which the connection must be hijacked.<br />
The <strong>Hack</strong>ademy DMP -93/209- SYSDREAM