Product Manual
Product Manual
Product Manual
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Click Apply to implement changes made.<br />
DES-3526 / DES-3526DC Fast Ethernet Layer 2 Switch<br />
authentication attempts. Users failing to be authenticated after the set amount of<br />
attempts will be denied access to the Switch and will be locked out of further<br />
authentication attempts. Command line interface users will have to wait 60<br />
seconds before another authentication attempt. Telnet and web users will be<br />
disconnected from the Switch. The user may set the number of attempts from 1 to<br />
255. The default setting is 3.<br />
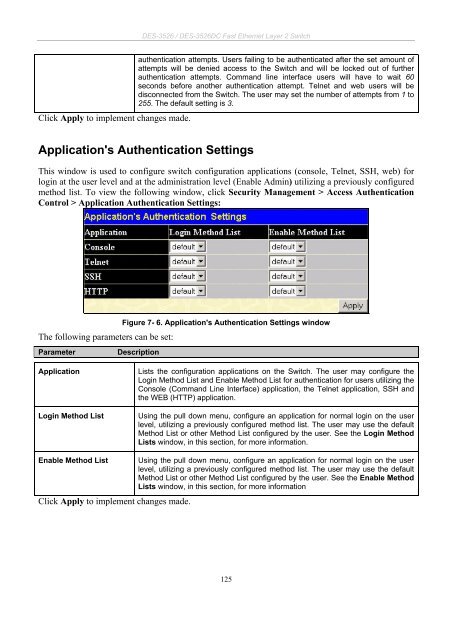
Application's Authentication Settings<br />
This window is used to configure switch configuration applications (console, Telnet, SSH, web) for<br />
login at the user level and at the administration level (Enable Admin) utilizing a previously configured<br />
method list. To view the following window, click Security Management > Access Authentication<br />
Control > Application Authentication Settings:<br />
The following parameters can be set:<br />
Parameter Description<br />
Figure 7- 6. Application's Authentication Settings window<br />
Application Lists the configuration applications on the Switch. The user may configure the<br />
Login Method List and Enable Method List for authentication for users utilizing the<br />
Console (Command Line Interface) application, the Telnet application, SSH and<br />
the WEB (HTTP) application.<br />
Login Method List Using the pull down menu, configure an application for normal login on the user<br />
level, utilizing a previously configured method list. The user may use the default<br />
Method List or other Method List configured by the user. See the Login Method<br />
Lists window, in this section, for more information.<br />
Enable Method List Using the pull down menu, configure an application for normal login on the user<br />
level, utilizing a previously configured method list. The user may use the default<br />
Method List or other Method List configured by the user. See the Enable Method<br />
Lists window, in this section, for more information<br />
Click Apply to implement changes made.<br />
125