Product Manual
Product Manual
Product Manual
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Enable Admin<br />
DES-3526 / DES-3526DC Fast Ethernet Layer 2 Switch<br />
The Enable Admin window is for users who have logged on to the Switch on the normal user level,<br />
and wish to be promoted to the administrator level. After logging on to the Switch, users will have<br />
only user level privileges. To gain access to administrator level privileges, the user will open this<br />
window and will have to enter an authentication password. Possible authentication methods for this<br />
function include TACACS/XTACACS/TACACS+/RADIUS, user defined server groups, local enable<br />
(local account on the Switch), or no authentication (none). Because XTACACS and TACACS do not<br />
support the enable function, the user must create a special account on the server host, which has the<br />
username "enable", and a password configured by the administrator that will support the "enable"<br />
function. This function becomes inoperable when the authentication policy is disabled.<br />
To view the following window, click Security Management > Access Authentication Control ><br />
Enable Admin:<br />
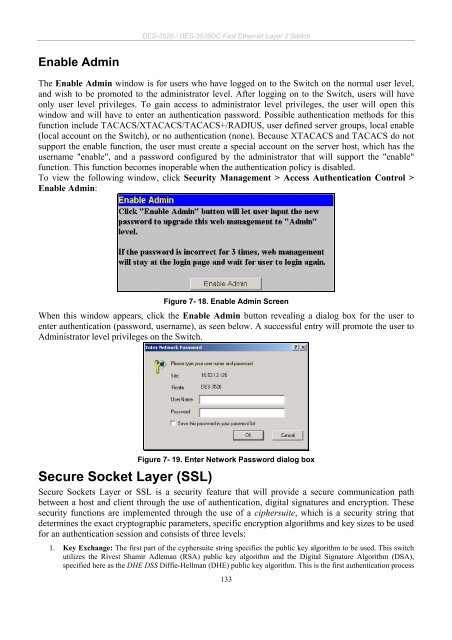
Figure 7- 18. Enable Admin Screen<br />
When this window appears, click the Enable Admin button revealing a dialog box for the user to<br />
enter authentication (password, username), as seen below. A successful entry will promote the user to<br />
Administrator level privileges on the Switch.<br />
Figure 7- 19. Enter Network Password dialog box<br />
Secure Socket Layer (SSL)<br />
Secure Sockets Layer or SSL is a security feature that will provide a secure communication path<br />
between a host and client through the use of authentication, digital signatures and encryption. These<br />
security functions are implemented through the use of a ciphersuite, which is a security string that<br />
determines the exact cryptographic parameters, specific encryption algorithms and key sizes to be used<br />
for an authentication session and consists of three levels:<br />
1. Key Exchange: The first part of the cyphersuite string specifies the public key algorithm to be used. This switch<br />
utilizes the Rivest Shamir Adleman (RSA) public key algorithm and the Digital Signature Algorithm (DSA),<br />
specified here as the DHE DSS Diffie-Hellman (DHE) public key algorithm. This is the first authentication process<br />
133