USAF ILA Handbook - ACC Practice Center - Defense Acquisition ...
USAF ILA Handbook - ACC Practice Center - Defense Acquisition ...
USAF ILA Handbook - ACC Practice Center - Defense Acquisition ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
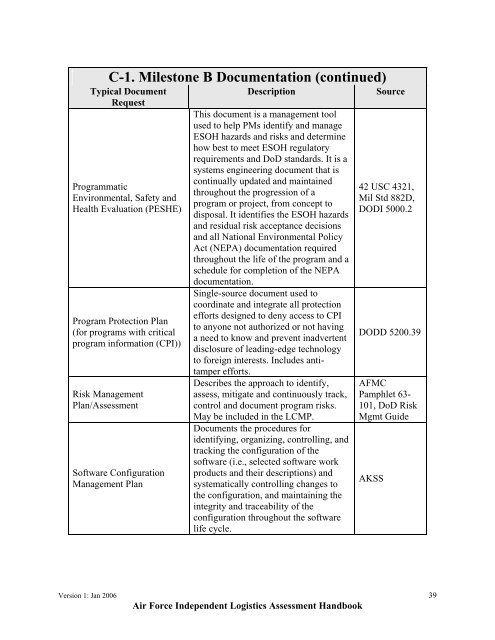
C-1. Milestone B Documentation (continued)<br />
Typical Document<br />
Request<br />
Programmatic<br />
Environmental, Safety and<br />
Health Evaluation (PESHE)<br />
Program Protection Plan<br />
(for programs with critical<br />
program information (CPI))<br />
Risk Management<br />
Plan/Assessment<br />
Software Configuration<br />
Management Plan<br />
Description<br />
This document is a management tool<br />
used to help PMs identify and manage<br />
ESOH hazards and risks and determine<br />
how best to meet ESOH regulatory<br />
requirements and DoD standards. It is a<br />
systems engineering document that is<br />
continually updated and maintained<br />
throughout the progression of a<br />
program or project, from concept to<br />
disposal. It identifies the ESOH hazards<br />
and residual risk acceptance decisions<br />
and all National Environmental Policy<br />
Act (NEPA) documentation required<br />
throughout the life of the program and a<br />
schedule for completion of the NEPA<br />
documentation.<br />
Single-source document used to<br />
coordinate and integrate all protection<br />
efforts designed to deny access to CPI<br />
to anyone not authorized or not having<br />
a need to know and prevent inadvertent<br />
disclosure of leading-edge technology<br />
to foreign interests. Includes antitamper<br />
efforts.<br />
Describes the approach to identify,<br />
assess, mitigate and continuously track,<br />
control and document program risks.<br />
May be included in the LCMP.<br />
Documents the procedures for<br />
identifying, organizing, controlling, and<br />
tracking the configuration of the<br />
software (i.e., selected software work<br />
products and their descriptions) and<br />
systematically controlling changes to<br />
the configuration, and maintaining the<br />
integrity and traceability of the<br />
configuration throughout the software<br />
life cycle.<br />
Source<br />
42 USC 4321,<br />
Mil Std 882D,<br />
DODI 5000.2<br />
DODD 5200.39<br />
AFMC<br />
Pamphlet 63-<br />
101, DoD Risk<br />
Mgmt Guide<br />
AKSS<br />
Version 1: Jan 2006 39<br />
Air Force Independent Logistics Assessment <strong>Handbook</strong>