- Page 1 and 2:
Cisco IOS Wide-Area NetworkingConfi
- Page 4 and 5:
Documentation ConventionsAbout Cisc
- Page 6 and 7:
Documentation OrganizationAbout Cis
- Page 8 and 9:
Documentation OrganizationAbout Cis
- Page 10 and 11:
Documentation OrganizationAbout Cis
- Page 12 and 13:
Documentation OrganizationAbout Cis
- Page 14 and 15:
Additional Resources and Documentat
- Page 16 and 17:
Using the CLIUsing the Command-Line
- Page 18 and 19:
Using the CLIUsing the Command-Line
- Page 20 and 21:
Using the CLIUsing the Command-Line
- Page 22 and 23:
Using the CLIUsing the Command-Line
- Page 24 and 25:
Using the CLIUsing the Command-Line
- Page 26 and 27:
Saving Changes to a ConfigurationUs
- Page 28 and 29:
Additional InformationUsing the Com
- Page 31 and 32:
Configuring Frame RelayFeature Hist
- Page 33 and 34:
Configuring Frame RelayFrame Relay
- Page 35 and 36:
Configuring Frame RelayConfiguring
- Page 37 and 38:
Configuring Frame RelayConfiguring
- Page 39 and 40:
Configuring Frame RelayConfiguring
- Page 41 and 42:
Configuring Frame RelayConfiguring
- Page 43 and 44:
Configuring Frame RelayConfiguring
- Page 45 and 46:
Configuring Frame RelayConfiguring
- Page 47 and 48:
Configuring Frame RelayConfiguring
- Page 49 and 50:
Configuring Frame RelayConfiguring
- Page 51 and 52:
Configuring Frame RelayConfiguring
- Page 53 and 54:
Configuring Frame RelayConfiguring
- Page 55 and 56:
Configuring Frame RelayConfiguring
- Page 57 and 58:
Configuring Frame RelayCustomizing
- Page 59 and 60:
Configuring Frame RelayCustomizing
- Page 61 and 62:
Configuring Frame RelayCustomizing
- Page 63 and 64:
Configuring Frame RelayCustomizing
- Page 65 and 66:
Configuring Frame RelayCustomizing
- Page 67 and 68:
Configuring Frame RelayCustomizing
- Page 69 and 70:
Configuring Frame RelayCustomizing
- Page 71 and 72:
Configuring Frame RelayCustomizing
- Page 73 and 74:
Configuring Frame RelayCustomizing
- Page 75 and 76:
Configuring Frame RelayCustomizing
- Page 77 and 78:
Configuring Frame RelayCustomizing
- Page 79 and 80:
Configuring Frame RelayCustomizing
- Page 81 and 82:
Configuring Frame RelayFrame Relay
- Page 83 and 84:
Configuring Frame RelayFrame Relay
- Page 85 and 86:
Configuring Frame RelayFrame Relay
- Page 87 and 88:
Configuring Frame RelayFrame Relay
- Page 89 and 90:
Configuring Frame RelayFrame Relay
- Page 91 and 92:
Configuring Frame RelayFrame Relay
- Page 93 and 94:
Configuring Frame RelayFrame Relay
- Page 95 and 96:
Configuring Frame RelayFrame Relay
- Page 97 and 98:
Configuring Frame RelayFrame Relay
- Page 99 and 100:
Configuring Frame RelayFrame Relay
- Page 101 and 102:
Configuring Frame RelayFrame Relay
- Page 103 and 104:
Configuring Frame RelayFrame Relay
- Page 105 and 106:
Configuring Frame RelayFrame Relay
- Page 107 and 108:
Adaptive Frame Relay Traffic Shapin
- Page 109 and 110:
Adaptive Frame Relay Traffic Shapin
- Page 111 and 112:
Adaptive Frame Relay Traffic Shapin
- Page 113 and 114:
Adaptive Frame Relay Traffic Shapin
- Page 115 and 116:
Frame Relay 64-Bit CountersFeature
- Page 117 and 118:
Frame Relay 64-Bit CountersSupporte
- Page 119 and 120:
Frame Relay 64-Bit CountersConfigur
- Page 121 and 122:
Frame Relay 64-Bit CountersConfigur
- Page 123 and 124:
Frame Relay MIB EnhancementsFeature
- Page 125 and 126:
• The chapter “Configuring Simp
- Page 127:
Command ReferenceThe following comm
- Page 130 and 131:
Feature OverviewFrame Relay Point-M
- Page 132 and 133:
Supported Standards, MIBs, and RFCs
- Page 134 and 135:
Configuration ExamplesFrame Relay P
- Page 136 and 137:
Command ReferenceFrame Relay Point-
- Page 138 and 139:
How Frame Relay Queueing and Fragme
- Page 140:
• Cisco 2500 series• Cisco 2600
- Page 143 and 144:
Configuring the Shaping Policy Usin
- Page 145 and 146:
The following sample output for the
- Page 147 and 148:
Frame Relay Queueing, Shaping, and
- Page 149 and 150:
Frame Relay PVC Bundles with QoS Su
- Page 151 and 152:
Frame Relay PVC Bundles with QoS Su
- Page 153 and 154:
Frame Relay PVC Bundles with QoS Su
- Page 155 and 156:
Frame Relay PVC Bundles with QoS Su
- Page 157 and 158:
Frame Relay PVC Bundles with QoS Su
- Page 159 and 160:
Frame Relay PVC Bundles with QoS Su
- Page 161 and 162:
Frame Relay PVC Bundles with QoS Su
- Page 163 and 164:
Frame Relay PVC Bundles with QoS Su
- Page 165 and 166:
Frame Relay PVC Bundles with QoS Su
- Page 167 and 168:
Frame Relay PVC Bundles with QoS Su
- Page 169 and 170:
Frame Relay PVC Bundles with QoS Su
- Page 171 and 172:
Frame Relay PVC Bundles with QoS Su
- Page 173 and 174:
Frame Relay Voice-Adaptive Traffic
- Page 175 and 176:
Frame Relay Voice-Adaptive Traffic
- Page 177 and 178:
Frame Relay Voice-Adaptive Traffic
- Page 179 and 180:
Frame Relay Voice-Adaptive Traffic
- Page 181 and 182:
Frame Relay Voice-Adaptive Traffic
- Page 183 and 184:
Frame Relay Voice-Adaptive Traffic
- Page 185 and 186:
Frame Relay Voice-Adaptive Traffic
- Page 187 and 188:
Frame Relay Voice-Adaptive Traffic
- Page 189 and 190:
MQC-Based Frame Relay Traffic Shapi
- Page 191 and 192:
MQC-Based Frame Relay Traffic Shapi
- Page 193 and 194:
MQC-Based Frame Relay Traffic Shapi
- Page 195 and 196:
MQC-Based Frame Relay Traffic Shapi
- Page 197 and 198:
MQC-Based Frame Relay Traffic Shapi
- Page 199 and 200:
MQC-Based Frame Relay Traffic Shapi
- Page 201 and 202:
MQC-Based Frame Relay Traffic Shapi
- Page 203 and 204:
Multilink Frame Relay (FRF.16.1)Fir
- Page 205 and 206:
Multilink Frame Relay (FRF.16.1)Inf
- Page 207 and 208:
Multilink Frame Relay (FRF.16.1)How
- Page 209 and 210:
Multilink Frame Relay (FRF.16.1)How
- Page 211 and 212:
Multilink Frame Relay (FRF.16.1)How
- Page 213 and 214:
Multilink Frame Relay (FRF.16.1)Con
- Page 215 and 216:
Multilink Frame Relay (FRF.16.1)Com
- Page 217 and 218:
Distributed Multilink Frame Relay (
- Page 219 and 220:
Distributed Multilink Frame Relay (
- Page 221 and 222:
Distributed Multilink Frame Relay (
- Page 223 and 224:
Distributed Multilink Frame Relay (
- Page 225 and 226:
Distributed Multilink Frame Relay (
- Page 227 and 228:
Distributed Multilink Frame Relay (
- Page 229 and 230:
Configuring Frame Relay-ATM Interwo
- Page 231 and 232:
Configuring Frame Relay-ATM Interwo
- Page 233 and 234:
Configuring Frame Relay-ATM Interwo
- Page 235 and 236:
Configuring Frame Relay-ATM Interwo
- Page 237 and 238:
Configuring Frame Relay-ATM Interwo
- Page 239 and 240:
Layer 2 Tunnel Protocol Version 3Fi
- Page 241 and 242:
Supported Port Adapters for the Cis
- Page 243 and 244:
• In OAM local emulation mode onl
- Page 245 and 246:
Layer Frame Fragmentation Restricti
- Page 247 and 248:
With ISIS packet fragmentation, ISI
- Page 249 and 250:
• Policing on both Ethernet and A
- Page 251 and 252:
L2TPv3 DecapsulationWhen an L2TPv3
- Page 253 and 254:
• Configuring output access contr
- Page 255 and 256:
Table 3Engine 5 Interfaces Supporte
- Page 257 and 258:
Table 4L2TPv3 Features Supported in
- Page 259 and 260:
Table 4L2TPv3 Features Supported in
- Page 261 and 262:
Frame Relay-Specific Restrictions
- Page 263 and 264:
• FRF.9 process switched payload
- Page 265 and 266:
• Egress queueing is determined a
- Page 267 and 268:
Information About Layer 2 Tunnel Pr
- Page 269 and 270:
Benefits of Using L2TPv3L2TPv3 Simp
- Page 271 and 272:
Static L2TPv3 SessionsTypically, th
- Page 273 and 274:
L2TPv3 Type of Service MarkingKeepa
- Page 275 and 276:
configured with the L2TPv3 Control
- Page 277 and 278:
L2TPv3 Protocol DemultiplexingThe P
- Page 279 and 280:
Supported L2TPv3 PayloadsL2TPv3 sup
- Page 281 and 282:
CIR GuaranteesTo provide committed
- Page 283 and 284:
Table 6Release Support for the ATM
- Page 285 and 286:
Figure 3Protocol Demultiplexing of
- Page 287 and 288:
This task configures a set of timin
- Page 289 and 290:
Table 8Compatibility Matrix for L2T
- Page 291 and 292:
Step 5Step 6Command or Actionpasswo
- Page 293 and 294:
Step 5Step 6Command or Actiondigest
- Page 295 and 296:
Step 6Step 7Command or Actionshow l
- Page 297 and 298:
For simple L2TPv3 signaling configu
- Page 299 and 300:
Step 7Step 8Step 9Step 10Command or
- Page 301 and 302:
Step 3Step 4Command or Actioninterf
- Page 303 and 304:
Step 5Step 6Step 7Step 8Command or
- Page 305 and 306:
Configuring the Xconnect Attachment
- Page 307 and 308:
DETAILED STEPSStep 1Step 2Command o
- Page 309 and 310:
Step 5Step 6Command or Actioncell-p
- Page 311 and 312:
Configuring VC Mode ATM Cell Packin
- Page 313 and 314:
Configuring ATM AAL5 SDU Mode over
- Page 315 and 316:
DETAILED STEPSStep 1Step 2Command o
- Page 317 and 318:
DETAILED STEPSStep 1Step 2Command o
- Page 319 and 320:
DETAILED STEPSStep 1Step 2Command o
- Page 321 and 322:
Configuring Protocol Demultiplexing
- Page 323 and 324:
Step 3Command or Actioninterface ty
- Page 325 and 326:
Step 7Step 8Command or Actionxconne
- Page 327 and 328:
DETAILED STEPSStep 1Step 2enableExa
- Page 329 and 330:
Configuring a Negotiated L2TPv3 Ses
- Page 331 and 332:
Configuring L2TPv3 Control Channel
- Page 333 and 334:
Configuring ATM Single Cell Relay V
- Page 335 and 336:
encapsulation aal5!interface atm 1/
- Page 337 and 338:
Verifying OAM Local Emulation for A
- Page 339 and 340:
Configuring QoS for L2TPv3 on the C
- Page 341 and 342:
encapsulation frame-relayframe-rela
- Page 343 and 344: Note that the sample output policy
- Page 345 and 346: Configuring a QoS Policy for Commit
- Page 347 and 348: !interface Serial0/0.1/1:11encapsul
- Page 349 and 350: Technical AssistanceDescriptionThe
- Page 351 and 352: Table 912.0(24)S112.0(27)S12.0(28)S
- Page 353 and 354: Table 9Feature Information for Laye
- Page 355 and 356: MTU—maximum transmission unit. Ma
- Page 357 and 358: Configuring SMDSSMDS Hardware Requi
- Page 359 and 360: Configuring SMDSEnabling SMDS on th
- Page 361 and 362: Configuring SMDSEnabling SMDS on th
- Page 363 and 364: Configuring SMDSCustomizing Your SM
- Page 365 and 366: Configuring SMDSCustomizing Your SM
- Page 367 and 368: Configuring SMDSSMDS Configuration
- Page 369 and 370: Configuring SMDSSMDS Configuration
- Page 371 and 372: Configuring SMDSSMDS Configuration
- Page 373: Configuring X.25 and LAPB
- Page 376 and 377: LAPB OverviewConfiguring X.25 and L
- Page 378 and 379: LAPB Configuration Task ListConfigu
- Page 380 and 381: X.25 Configuration Task ListConfigu
- Page 382 and 383: X.25 Configuration Task ListConfigu
- Page 384 and 385: X.25 Configuration Task ListConfigu
- Page 386 and 387: X.25 Configuration Task ListConfigu
- Page 388 and 389: Configuring Additional X.25 Interfa
- Page 390 and 391: Configuring Additional X.25 Interfa
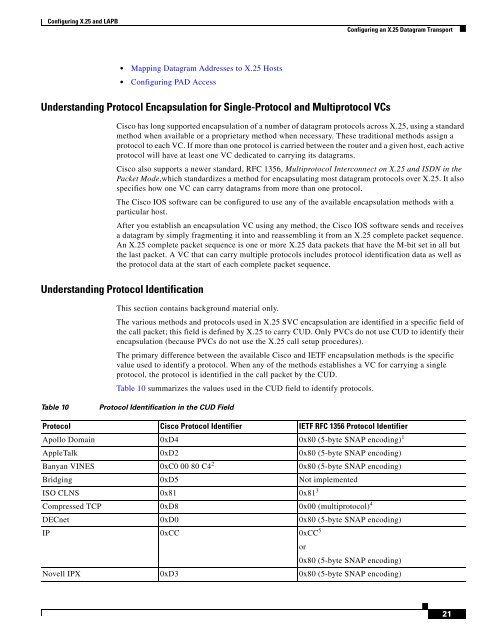
- Page 392 and 393: Configuring an X.25 Datagram Transp
- Page 396 and 397: Configuring an X.25 Datagram Transp
- Page 398 and 399: Configuring an X.25 Datagram Transp
- Page 400 and 401: Configuring Additional X.25 Datagra
- Page 402 and 403: Configuring Additional X.25 Datagra
- Page 404 and 405: Configuring X.25 RoutingConfiguring
- Page 406 and 407: Configuring X.25 RoutingConfiguring
- Page 408 and 409: Configuring Additional X.25 Routing
- Page 410 and 411: Configuring Additional X.25 Routing
- Page 412 and 413: Configuring DNS-Based X.25 RoutingC
- Page 414 and 415: Configuring DNS-Based X.25 RoutingC
- Page 416 and 417: Configuring X.25 over Frame Relay (
- Page 418 and 419: Configuring Priority Queueing or Cu
- Page 420 and 421: Configuring X.25 Closed User Groups
- Page 422 and 423: Configuring X.25 Closed User Groups
- Page 424 and 425: Configuring X.25 Closed User Groups
- Page 426 and 427: Configuring X.25 Closed User Groups
- Page 428 and 429: Configuring DDN or BFE X.25Configur
- Page 430 and 431: Configuring DDN or BFE X.25Configur
- Page 432 and 433: Configuring X.25 Remote Failure Det
- Page 434 and 435: Creating X.29 Access ListsConfiguri
- Page 436 and 437: X.25 and LAPB Configuration Example
- Page 438 and 439: X.25 and LAPB Configuration Example
- Page 440 and 441: X.25 and LAPB Configuration Example
- Page 442 and 443: X.25 and LAPB Configuration Example
- Page 444 and 445:
X.25 and LAPB Configuration Example
- Page 446 and 447:
X.25 and LAPB Configuration Example
- Page 448 and 449:
X.25 and LAPB Configuration Example
- Page 450 and 451:
X.25 and LAPB Configuration Example
- Page 452 and 453:
X.25 and LAPB Configuration Example
- Page 454 and 455:
X.25 and LAPB Configuration Example
- Page 456 and 457:
X.25 and LAPB Configuration Example
- Page 458 and 459:
X.25 and LAPB Configuration Example
- Page 460 and 461:
Feature OverviewTerminal Line Secur
- Page 462 and 463:
Feature OverviewTerminal Line Secur
- Page 464 and 465:
Supported PlatformsTerminal Line Se
- Page 466 and 467:
Configuration TasksTerminal Line Se
- Page 468 and 469:
Command ReferenceTerminal Line Secu
- Page 470 and 471:
GlossaryTerminal Line Security for
- Page 472 and 473:
Supported PlatformsX.25 Annex G Ses
- Page 474 and 475:
Command ReferenceX.25 Annex G Sessi
- Page 476 and 477:
Feature OverviewX.25 Dual Serial Li
- Page 478 and 479:
Supported PlatformsX.25 Dual Serial
- Page 480 and 481:
Configuration TasksX.25 Dual Serial
- Page 482 and 483:
Command ReferenceX.25 Dual Serial L
- Page 484 and 485:
GlossaryX.25 Dual Serial Line Manag
- Page 486 and 487:
Feature OverviewX.25 over TCP Profi
- Page 488 and 489:
Supported PlatformsX.25 over TCP Pr
- Page 490 and 491:
Configuration TasksX.25 over TCP Pr
- Page 492 and 493:
Command ReferenceX.25 over TCP Prof
- Page 494 and 495:
GlossaryX.25 over TCP Profiles10
- Page 496 and 497:
When to Use Record Boundary Preserv
- Page 498 and 499:
Restrictions• X.25 connections wi
- Page 500 and 501:
CommandRouter(config-if)# x25 pvc c
- Page 502 and 503:
successfully completed, the TCP con
- Page 504 and 505:
• PVC Configured to Use RBP for I
- Page 506 and 507:
X.121—ITU-T standard describing a
- Page 508 and 509:
ContentsX.25 Suppression of Securit
- Page 510 and 511:
How to Suppress the X.25 Security S
- Page 512 and 513:
Configuration Example for Suppressi
- Page 514 and 515:
Command ReferenceX.25 Suppression o
- Page 516 and 517:
Information About X.25 Call Confirm
- Page 518 and 519:
How to Configure X.25 Call Confirm
- Page 520 and 521:
Additional ReferencesX.25 Call Conf
- Page 522 and 523:
Command ReferenceX.25 Call Confirm
- Page 524 and 525:
Displaying the Contents of X.25 Pac
- Page 526 and 527:
Command ReferenceX.25 Data Display
- Page 528 and 529:
Information About X.25 Version Conf
- Page 530 and 531:
Information About X.25 Version Conf
- Page 532 and 533:
Information About X.25 Version Conf
- Page 534 and 535:
Information About X.25 Version Conf
- Page 536 and 537:
How to Specify the X.25 VersionX.25
- Page 538 and 539:
Configuration Examples for X.25 Ver
- Page 540 and 541:
Additional ReferencesX.25 Version C
- Page 542 and 543:
Command ReferenceX.25 Version Confi
- Page 544 and 545:
ContentsX.25 Station Type for ISDN
- Page 546 and 547:
How to Configure X.25 Encapsulation
- Page 548 and 549:
Additional ReferencesX.25 Station T
- Page 550 and 551:
Command ReferenceX.25 Station Type
- Page 553 and 554:
Frame Relay-ATM Interworking Suppor
- Page 555 and 556:
X.25 Facility HandlingThis appendix
- Page 557 and 558:
X.25 Facility HandlingX.25 Facility