Enabling Processes
Enabling Processes
Enabling Processes
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
CHAPTER 5<br />
COBIT 5 PROCESS REFERENCE GUIDE CONTENTS<br />
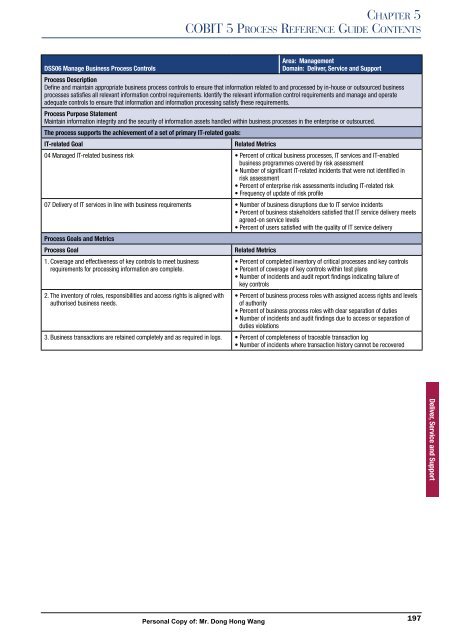
Area: Management<br />
DSS06 Manage Business Process Controls<br />
Domain: Deliver, Service and Support<br />
Process Description<br />
Define and maintain appropriate business process controls to ensure that information related to and processed by in-house or outsourced business<br />
processes satisfies all relevant information control requirements. Identify the relevant information control requirements and manage and operate<br />
adequate controls to ensure that information and information processing satisfy these requirements.<br />
Process Purpose Statement<br />
Maintain information integrity and the security of information assets handled within business processes in the enterprise or outsourced.<br />
The process supports the achievement of a set of primary IT-related goals:<br />
IT-related Goal Related Metrics<br />
04 Managed IT-related business risk � ������� �� �������� �������� ���������� �� �������� ��� ����������<br />
business programmes covered by risk assessment<br />
� ������ �� ����������� ���������� ��������� ���� ���� ��� ���������� ��<br />
risk assessment<br />
� ������� �� ���������� ���� ����������� ��������� ���������� ����<br />
� ��������� �� ������ �� ���� �������<br />
07 Delivery of IT services in line with business requirements � ������ �� �������� ����������� ��� �� �� ������� ���������<br />
� ������� �� �������� ������������ ��������� ���� �� ������� �������� �����<br />
agreed-on service levels<br />
� ������� �� ����� ��������� ���� ��� ������� �� �� ������� ��������<br />
Process Goals and Metrics<br />
Process Goal Related Metrics<br />
1. Coverage and effectiveness of key controls to meet business<br />
requirements for processing information are complete.<br />
2. The inventory of roles, responsibilities and access rights is aligned with<br />
authorised business needs.<br />
� ������� �� ��������� ��������� �� �������� ��������� ��� ��� ��������<br />
� ������� �� �������� �� ��� �������� ������ ���� �����<br />
� ������ �� ��������� ��� ����� ������ �������� ���������� ������� ��<br />
key controls<br />
� ������� �� �������� ������� ����� ���� �������� ������ ������ ��� ������<br />
of authority<br />
� ������� �� �������� ������� ����� ���� ����� ���������� �� ������<br />
� ������ �� ��������� ��� ����� �������� ��� �� ������ �� ���������� ��<br />
duties violations<br />
3. Business transactions are retained completely and as required in logs. � ������� �� ������������ �� ��������� ����������� ���<br />
� ������ �� ��������� ����� ����������� ������� ������ �� ���������<br />
Personal Copy of: Mr. Dong Hong Wang<br />
197<br />
Deliver, Service and Support