PRE-DRIVE C2X Deliverable D0.3 Final report_20100929.pdf
PRE-DRIVE C2X Deliverable D0.3 Final report_20100929.pdf
PRE-DRIVE C2X Deliverable D0.3 Final report_20100929.pdf
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
<strong>Final</strong> Report <strong>PRE</strong>-<strong>DRIVE</strong> <strong>C2X</strong> 29.9.2010<br />
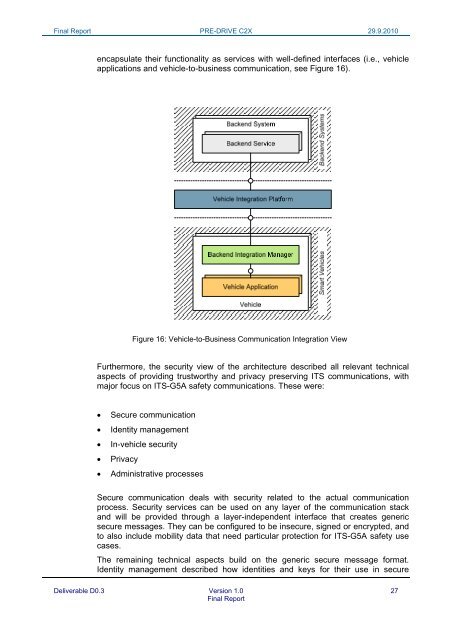
encapsulate their functionality as services with well-defined interfaces (i.e., vehicle<br />
applications and vehicle-to-business communication, see Figure 16).<br />
Figure 16: Vehicle-to-Business Communication Integration View<br />
Furthermore, the security view of the architecture described all relevant technical<br />
aspects of providing trustworthy and privacy preserving ITS communications, with<br />
major focus on ITS-G5A safety communications. These were:<br />
<br />
<br />
<br />
<br />
<br />
Secure communication<br />
Identity management<br />
In-vehicle security<br />
Privacy<br />
Administrative processes<br />
Secure communication deals with security related to the actual communication<br />
process. Security services can be used on any layer of the communication stack<br />
and will be provided through a layer-independent interface that creates generic<br />
secure messages. They can be configured to be insecure, signed or encrypted, and<br />
to also include mobility data that need particular protection for ITS-G5A safety use<br />
cases.<br />
The remaining technical aspects build on the generic secure message format.<br />
Identity management described how identities and keys for their use in secure<br />
<strong>Deliverable</strong> <strong>D0.3</strong> Version 1.0 27<br />
<strong>Final</strong> Report