PXA3xx Boot ROM Reference Manual - Marvell
PXA3xx Boot ROM Reference Manual - Marvell
PXA3xx Boot ROM Reference Manual - Marvell
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
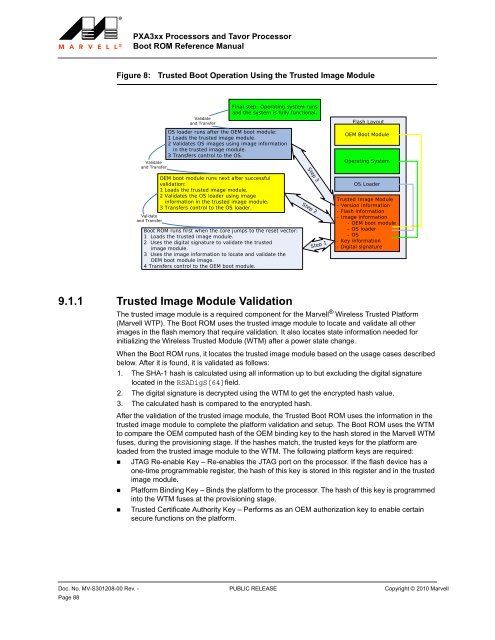
<strong>PXA3xx</strong> Processors and Tavor Processor<strong>Boot</strong> <strong>ROM</strong> <strong>Reference</strong> <strong>Manual</strong>Figure 8:Trusted <strong>Boot</strong> Operation Using the Trusted Image ModuleFinal step: Operating system runsand the system is fully functional.Validateand TransferOS loader runs after the OEM boot module:1 Loads the trusted image module.2 Validates OS images using image informationin the trusted image module.3 Transfers control to the OS.Validateand TransferOEM boot module runs next after successfulvalidation:1 Loads the trusted image module.2 Validates the OS loader using imageinformation in the trusted image module.3 Transfers control to the OS loader.Validateand Transfer<strong>Boot</strong> <strong>ROM</strong> runs first when the core jumps to the reset vector:1 Loads the trusted image module.2 Uses the digital signature to validate the trustedimage module.3 Uses the image information to locate and validate theOEM boot module image.4 Transfers control to the OEM boot module.9.1.1 Trusted Image Module ValidationFlash LayoutOEM <strong>Boot</strong> ModuleOperating SystemOS LoaderTrusted Image Module- Version information- Flash information- Image information- OEM boot module- OS loader- OS- Key information- Digital signatureThe trusted image module is a required component for the <strong>Marvell</strong> ® Wireless Trusted Platform(<strong>Marvell</strong> WTP). The <strong>Boot</strong> <strong>ROM</strong> uses the trusted image module to locate and validate all otherimages in the flash memory that require validation. It also locates state information needed forinitializing the Wireless Trusted Module (WTM) after a power state change.When the <strong>Boot</strong> <strong>ROM</strong> runs, it locates the trusted image module based on the usage cases describedbelow. After it is found, it is validated as follows:1. The SHA-1 hash is calculated using all information up to but excluding the digital signaturelocated in the RSADigS[64]field.2. The digital signature is decrypted using the WTM to get the encrypted hash value.3. The calculated hash is compared to the encrypted hash.After the validation of the trusted image module, the Trusted <strong>Boot</strong> <strong>ROM</strong> uses the information in thetrusted image module to complete the platform validation and setup. The <strong>Boot</strong> <strong>ROM</strong> uses the WTMto compare the OEM computed hash of the OEM binding key to the hash stored in the <strong>Marvell</strong> WTMfuses, during the provisioning stage. If the hashes match, the trusted keys for the platform areloaded from the trusted image module to the WTM. The following platform keys are required:• JTAG Re-enable Key – Re-enables the JTAG port on the processor. If the flash device has aone-time programmable register, the hash of this key is stored in this register and in the trustedimage module.• Platform Binding Key – Binds the platform to the processor. The hash of this key is programmedinto the WTM fuses at the provisioning stage.• Trusted Certificate Authority Key – Performs as an OEM authorization key to enable certainsecure functions on the platform.Step 3Step 2Step 112345678910111213141516171819202122232425262728293031323334353637383940414243444546474849505152535455565758Doc. No. MV-S301208-00 Rev. - PUBLIC RELEASE Copyright © 2010 <strong>Marvell</strong>Page 88