State of the Practice of Computer Security Incident Response Teams ...
State of the Practice of Computer Security Incident Response Teams ...
State of the Practice of Computer Security Incident Response Teams ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
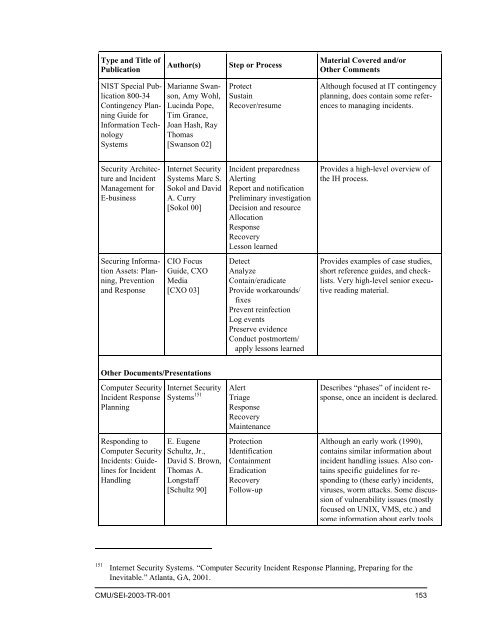
Type and Title <strong>of</strong><br />
Publication<br />
Author(s)<br />
Step or Process<br />
Material Covered and/or<br />
O<strong>the</strong>r Comments<br />
NIST Special Publication<br />
800-34<br />
Contingency Planning<br />
Guide for<br />
Information Technology<br />
Systems<br />
Marianne Swanson,<br />
Amy Wohl,<br />
Lucinda Pope,<br />
Tim Grance,<br />
Joan Hash, Ray<br />
Thomas<br />
[Swanson 02]<br />
Protect<br />
Sustain<br />
Recover/resume<br />
Although focused at IT contingency<br />
planning, does contain some references<br />
to managing incidents.<br />
<strong>Security</strong> Architecture<br />
and <strong>Incident</strong><br />
Management for<br />
E-business<br />
Internet <strong>Security</strong><br />
Systems Marc S.<br />
Sokol and David<br />
A. Curry<br />
[Sokol 00]<br />
<strong>Incident</strong> preparedness<br />
Alerting<br />
Report and notification<br />
Preliminary investigation<br />
Decision and resource<br />
Allocation<br />
<strong>Response</strong><br />
Recovery<br />
Lesson learned<br />
Provides a high-level overview <strong>of</strong><br />
<strong>the</strong> IH process.<br />
Securing Information<br />
Assets: Planning,<br />
Prevention<br />
and <strong>Response</strong><br />
CIO Focus<br />
Guide, CXO<br />
Media<br />
[CXO 03]<br />
Detect<br />
Analyze<br />
Contain/eradicate<br />
Provide workarounds/<br />
fixes<br />
Prevent reinfection<br />
Log events<br />
Preserve evidence<br />
Conduct postmortem/<br />
apply lessons learned<br />
Provides examples <strong>of</strong> case studies,<br />
short reference guides, and checklists.<br />
Very high-level senior executive<br />
reading material.<br />
O<strong>the</strong>r Documents/Presentations<br />
<strong>Computer</strong> <strong>Security</strong><br />
<strong>Incident</strong> <strong>Response</strong><br />
Planning<br />
Responding to<br />
<strong>Computer</strong> <strong>Security</strong><br />
<strong>Incident</strong>s: Guidelines<br />
for <strong>Incident</strong><br />
Handling<br />
Internet <strong>Security</strong><br />
Systems 151<br />
E. Eugene<br />
Schultz, Jr.,<br />
David S. Brown,<br />
Thomas A.<br />
Longstaff<br />
[Schultz 90]<br />
Alert<br />
Triage<br />
<strong>Response</strong><br />
Recovery<br />
Maintenance<br />
Protection<br />
Identification<br />
Containment<br />
Eradication<br />
Recovery<br />
Follow-up<br />
Describes “phases” <strong>of</strong> incident response,<br />
once an incident is declared.<br />
Although an early work (1990),<br />
contains similar information about<br />
incident handling issues. Also contains<br />
specific guidelines for responding<br />
to (<strong>the</strong>se early) incidents,<br />
viruses, worm attacks. Some discussion<br />
<strong>of</strong> vulnerability issues (mostly<br />
focused on UNIX, VMS, etc.) and<br />
some information about early tools<br />
151<br />
Internet <strong>Security</strong> Systems. “<strong>Computer</strong> <strong>Security</strong> <strong>Incident</strong> <strong>Response</strong> Planning, Preparing for <strong>the</strong><br />
Inevitable.” Atlanta, GA, 2001.<br />
CMU/SEI-2003-TR-001 153