Elektronika 2009-11.pdf - Instytut Systemów Elektronicznych
Elektronika 2009-11.pdf - Instytut Systemów Elektronicznych
Elektronika 2009-11.pdf - Instytut Systemów Elektronicznych
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
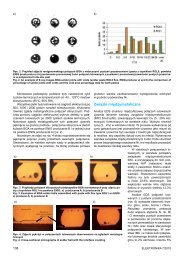
Fig. 2. An example of data groups aggregation into the one group<br />
consisting of three electronic documents and two separated electronic<br />
documents; Merkle tree is used (notation: h(...) - cryptographic<br />
hash function, || - concatenation) (compare with [18])<br />
Rys. 2. Przykład agregacji grup danych za pomocą drzewa Merkla<br />
z jedną grupą składająca się z trzech obiektów danych i dwóch pojedynczych<br />
obiektów danych (oznaczenia: h(...) - kryptograficzna<br />
funkcja skrótu, || - operator konkatenacji) (porównaj [18])<br />
with such properties was called the long-term provable authentic<br />
document). Note that V-SED idea is independent of<br />
the public key cryptography infrastructure, and particularly can<br />
be implemented in very promising environment of Certificateless<br />
Public Key Cryptosystem (CL-PKC).<br />
The implementation of the long-term electronic signature<br />
scheme LT-CESS requires a wide range of new complex services<br />
of TSI (Trusted Services Infrastructure) related to electronic<br />
signatures, documents of V-SED type and signature<br />
verification policies (VP) (see Section 3). Examples of possible<br />
technical solutions for an implementation of a long-term<br />
keeping the probative value of a signed electronic document<br />
(Section 5) are enough to demonstrate the opportunity to build<br />
such components. Theirs complexity depends on a trust level<br />
of the storage managing organization and usually requires the<br />
use of methods presented in Section 5.<br />
References<br />
[1] Act on electronic signature from September 18 th , 2001, Law<br />
Diary - Dz.U. 2001 no 130, pos. 1450 with later amendments (in<br />
Polish).<br />
[2] EU Directive 1999/93/EC of the European Parliament and the<br />
Council of 13 December 1999 on a Community framework for<br />
electronic signatures.<br />
[3] Boldyreva A., Fischlin M., Palacio A., Warinschi B.: A Closer Look<br />
at PKI: Security and Efficiency, Lecture Notes in Computer Science,<br />
Vol. 4450/2007, pp. 458-475, Public Key Cryptography -<br />
PKC 2007, 10th International Conference on Practice and Theory<br />
in Public-Key Cryptography, Beijing, China, April 16-20, 2007.<br />
[4] Shamir A.: Identity-based cryptosystems and signature<br />
schemes, Advances in Cryptology - Crypto’84, LNCS, vol. 196.<br />
pp. 47-53, Springer-Verlag, 1984.<br />
[5] Al-Riyami S., Paterson K.: Certificateless public key cryptography,<br />
Advances in Cryptology - AsiaCrypt, LNCS, vol. 2894, pp.<br />
452-473, Springer-Verlag, 2003.<br />
[6] Harn L., Ren J., Lin Ch.: Design of DL-based certificateless digital<br />
signatures, The Journal of Systems and Software, vol. 82,<br />
pp. 789-793, <strong>2009</strong>.<br />
[7] ETSI TS 101 733 Electronic Signatures and Infrastructures<br />
(ESI); CMS Advanced Electronic Signatures (CAdES), v. 1.7.4,<br />
July 2008.<br />
[8] ETSI TS 101 903 XML Advanced Electronic Signatures<br />
(XAdES), v1.4.1, June <strong>2009</strong>.<br />
[9] ETSI TS 102 778-5 Electronic Signatures and Infrastructures<br />
(ESI); PDF Advanced Electronic Signature Profiles, v. 1.1.1, July<br />
<strong>2009</strong>.<br />
[10] Gentry C., Silverberg A.: Hierarchical ID-based cryptography, in<br />
Y. Zheng, editor, Advances in Cryptology - ASIACRYPT 2002,<br />
Lecture Notes in Computer Science, vol. 2501, pp. 548-566.<br />
Springer-Verlag, 2002.<br />
[11] CWA 14171 General guidelines for electronic signature verification,<br />
May 2004.<br />
[12] Regulation of Ministry Council from August, 7th, 2002 on technical<br />
and organizational requirements for qualified certification<br />
authorities, certification policies for qualified certificates issued<br />
by them, and technical requirements for secure signature creation<br />
and verification devices (Low Diary -Dz.U. 2002 no 128,<br />
pos. 1094).<br />
[13] RFC 5280 Internet X.509 Public Key Infrastructure Certificate<br />
and Certificate Revocation List (CRL) Profile, May 2008.<br />
[14] CWA 15579 E-invoices and digital signatures, July 2006.<br />
[15] RFC 4998 Evidence Record Syntax (ERS), August 2007.<br />
[16] RFC 3161 Time-Stamp Protocol (TSP), August 2001.<br />
[17] ETSI TS 101 861 Time stamping profile, v1.3.1, January 2006.<br />
[18] Goodrich M. T., Tamassia R., Hasic J.: An Efficient Dynamic and<br />
Distributed Cryptographic Accumulator, in Information Security,<br />
5th International Conference, pp. 372-388, Sao Paulo, Brazil,<br />
September 30 - October 2002.<br />
(1) Above problems apply to electronic documents based both upon<br />
a qualified and non-qualified certificate<br />
(2) This requirement is directly related to the certificate electronic signature<br />
scheme CESS used in the PKC infrastructure (explicit certificates),<br />
but can be also applied indirectly in the CL-PKC infrastructure (implicit<br />
certificates).<br />
(3) TimeStampToken is an archive timestamp issued according to RFC<br />
3161 [16] or ETSI TS 101 861 [17].<br />
Przypominamy o prenumeracie miesięcznika <strong>Elektronika</strong> na 2010 r.<br />
34 ELEKTRONIKA 11/<strong>2009</strong>