fortigate-ipsec-40-mr3
fortigate-ipsec-40-mr3
fortigate-ipsec-40-mr3
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Configure the dynamically-addressed VPN peer Dynamic DNS configuration<br />
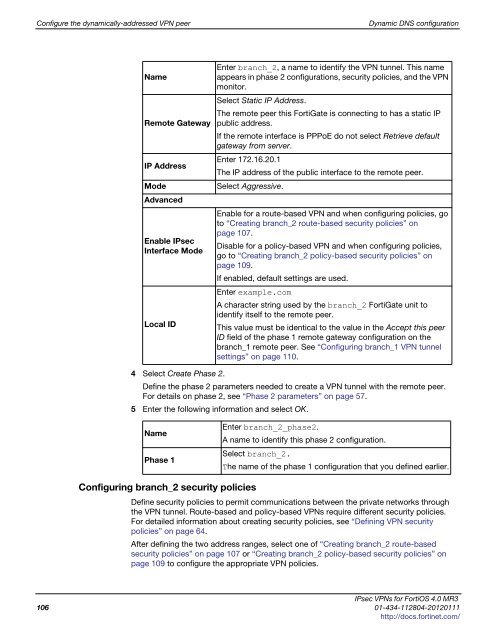
Name<br />
Remote Gateway<br />
4 Select Create Phase 2.<br />
Define the phase 2 parameters needed to create a VPN tunnel with the remote peer.<br />
For details on phase 2, see “Phase 2 parameters” on page 57.<br />
5 Enter the following information and select OK.<br />
Configuring branch_2 security policies<br />
Enter branch_2, a name to identify the VPN tunnel. This name<br />
appears in phase 2 configurations, security policies, and the VPN<br />
monitor.<br />
Select Static IP Address.<br />
The remote peer this FortiGate is connecting to has a static IP<br />
public address.<br />
If the remote interface is PPPoE do not select Retrieve default<br />
gateway from server.<br />
IP Address<br />
Enter 172.16.20.1<br />
The IP address of the public interface to the remote peer.<br />
Mode<br />
Advanced<br />
Select Aggressive.<br />
Enable IPsec<br />
Interface Mode<br />
Local ID<br />
Name<br />
Phase 1<br />
Enable for a route-based VPN and when configuring policies, go<br />
to “Creating branch_2 route-based security policies” on<br />
page 107.<br />
Disable for a policy-based VPN and when configuring policies,<br />
go to “Creating branch_2 policy-based security policies” on<br />
page 109.<br />
If enabled, default settings are used.<br />
Enter example.com<br />
A character string used by the branch_2 FortiGate unit to<br />
identify itself to the remote peer.<br />
This value must be identical to the value in the Accept this peer<br />
ID field of the phase 1 remote gateway configuration on the<br />
branch_1 remote peer. See “Configuring branch_1 VPN tunnel<br />
settings” on page 110.<br />
Enter branch_2_phase2.<br />
A name to identify this phase 2 configuration.<br />
Select branch_2.<br />
The name of the phase 1 configuration that you defined earlier.<br />
Define security policies to permit communications between the private networks through<br />
the VPN tunnel. Route-based and policy-based VPNs require different security policies.<br />
For detailed information about creating security policies, see “Defining VPN security<br />
policies” on page 64.<br />
After defining the two address ranges, select one of “Creating branch_2 route-based<br />
security policies” on page 107 or “Creating branch_2 policy-based security policies” on<br />
page 109 to configure the appropriate VPN policies.<br />
IPsec VPNs for FortiOS 4.0 MR3<br />
106 01-434-112804-20120111<br />
http://docs.fortinet.com/