fortigate-ipsec-40-mr3
fortigate-ipsec-40-mr3
fortigate-ipsec-40-mr3
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
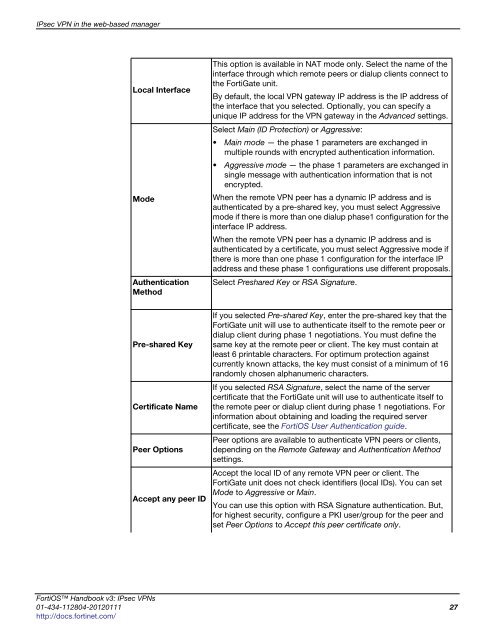
IPsec VPN in the web-based manager<br />
Local Interface<br />
Mode<br />
Authentication<br />
Method<br />
Pre-shared Key<br />
Certificate Name<br />
Peer Options<br />
Accept any peer ID<br />
This option is available in NAT mode only. Select the name of the<br />
interface through which remote peers or dialup clients connect to<br />
the FortiGate unit.<br />
By default, the local VPN gateway IP address is the IP address of<br />
the interface that you selected. Optionally, you can specify a<br />
unique IP address for the VPN gateway in the Advanced settings.<br />
Select Main (ID Protection) or Aggressive:<br />
Main mode — the phase 1 parameters are exchanged in<br />
multiple rounds with encrypted authentication information.<br />
Aggressive mode — the phase 1 parameters are exchanged in<br />
single message with authentication information that is not<br />
encrypted.<br />
When the remote VPN peer has a dynamic IP address and is<br />
authenticated by a pre-shared key, you must select Aggressive<br />
mode if there is more than one dialup phase1 configuration for the<br />
interface IP address.<br />
When the remote VPN peer has a dynamic IP address and is<br />
authenticated by a certificate, you must select Aggressive mode if<br />
there is more than one phase 1 configuration for the interface IP<br />
address and these phase 1 configurations use different proposals.<br />
Select Preshared Key or RSA Signature.<br />
If you selected Pre-shared Key, enter the pre-shared key that the<br />
FortiGate unit will use to authenticate itself to the remote peer or<br />
dialup client during phase 1 negotiations. You must define the<br />
same key at the remote peer or client. The key must contain at<br />
least 6 printable characters. For optimum protection against<br />
currently known attacks, the key must consist of a minimum of 16<br />
randomly chosen alphanumeric characters.<br />
If you selected RSA Signature, select the name of the server<br />
certificate that the FortiGate unit will use to authenticate itself to<br />
the remote peer or dialup client during phase 1 negotiations. For<br />
information about obtaining and loading the required server<br />
certificate, see the FortiOS User Authentication guide.<br />
Peer options are available to authenticate VPN peers or clients,<br />
depending on the Remote Gateway and Authentication Method<br />
settings.<br />
Accept the local ID of any remote VPN peer or client. The<br />
FortiGate unit does not check identifiers (local IDs). You can set<br />
Mode to Aggressive or Main.<br />
You can use this option with RSA Signature authentication. But,<br />
for highest security, configure a PKI user/group for the peer and<br />
set Peer Options to Accept this peer certificate only.<br />
FortiOS Handbook v3: IPsec VPNs<br />
01-434-112804-20120111 27<br />
http://docs.fortinet.com/