fortigate-ipsec-40-mr3
fortigate-ipsec-40-mr3
fortigate-ipsec-40-mr3
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Configuration overview Redundant VPN configurations<br />
The configuration described here assumes that your redundant VPNs are essentially<br />
equal in cost and capability. When the original VPN returns to service, traffic continues to<br />
use the replacement VPN until the replacement VPN fails. If your redundant VPN uses<br />
more expensive facilities, you want to use it only as a backup while the main VPN is<br />
down. For information on how to do this, see “Creating a backup IPsec interface” on<br />
page 173.<br />
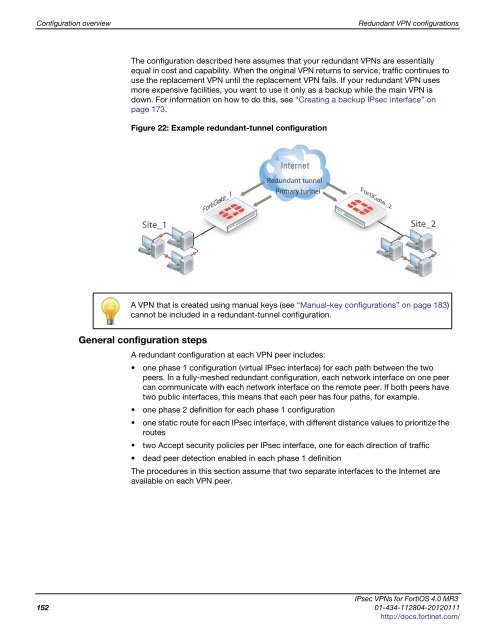
Figure 22: Example redundant-tunnel configuration<br />
Site_1<br />
FortiGate_1<br />
FortiGate_<br />
Redundant tunnel<br />
Primary tunnel<br />
FortiGate_2 rtiGate_2<br />
Site_2<br />
A VPN that is created using manual keys (see “Manual-key configurations” on page 183)<br />
cannot be included in a redundant-tunnel configuration.<br />
General configuration steps<br />
A redundant configuration at each VPN peer includes:<br />
one phase 1 configuration (virtual IPsec interface) for each path between the two<br />
peers. In a fully-meshed redundant configuration, each network interface on one peer<br />
can communicate with each network interface on the remote peer. If both peers have<br />
two public interfaces, this means that each peer has four paths, for example.<br />
one phase 2 definition for each phase 1 configuration<br />
one static route for each IPsec interface, with different distance values to prioritize the<br />
routes<br />
two Accept security policies per IPsec interface, one for each direction of traffic<br />
dead peer detection enabled in each phase 1 definition<br />
The procedures in this section assume that two separate interfaces to the Internet are<br />
available on each VPN peer.<br />
IPsec VPNs for FortiOS 4.0 MR3<br />
152 01-434-112804-20120111<br />
http://docs.fortinet.com/