fortigate-ipsec-40-mr3
fortigate-ipsec-40-mr3
fortigate-ipsec-40-mr3
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Configuration overview FortiClient dialup-client configurations<br />
The FortiClient application sends its encrypted packets to the VPN remote gateway,<br />
which is usually the public interface of the FortiGate unit. It also uses this interface to<br />
download VPN settings from the FortiGate unit. See “Automatic configuration of<br />
FortiClient dialup clients” on page 116.<br />
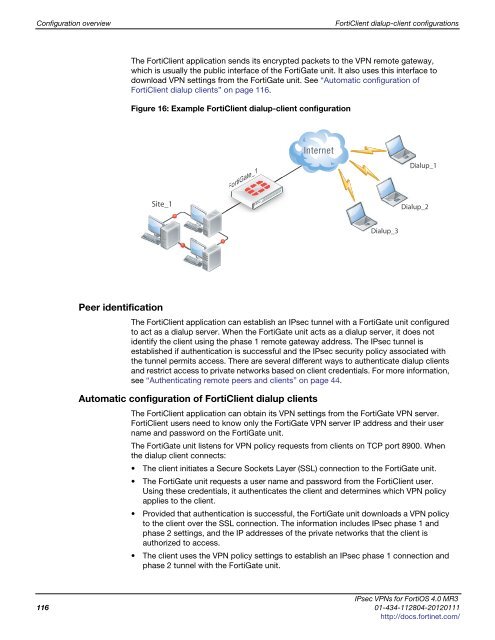
Figure 16: Example FortiClient dialup-client configuration<br />
Site_1<br />
FortiGate_1<br />
FortiGate_<br />
Peer identification<br />
The FortiClient application can establish an IPsec tunnel with a FortiGate unit configured<br />
to act as a dialup server. When the FortiGate unit acts as a dialup server, it does not<br />
identify the client using the phase 1 remote gateway address. The IPsec tunnel is<br />
established if authentication is successful and the IPsec security policy associated with<br />
the tunnel permits access. There are several different ways to authenticate dialup clients<br />
and restrict access to private networks based on client credentials. For more information,<br />
see “Authenticating remote peers and clients” on page 44.<br />
Automatic configuration of FortiClient dialup clients<br />
Dialup_3<br />
Dialup_1<br />
Dialup_2<br />
The FortiClient application can obtain its VPN settings from the FortiGate VPN server.<br />
FortiClient users need to know only the FortiGate VPN server IP address and their user<br />
name and password on the FortiGate unit.<br />
The FortiGate unit listens for VPN policy requests from clients on TCP port 8900. When<br />
the dialup client connects:<br />
The client initiates a Secure Sockets Layer (SSL) connection to the FortiGate unit.<br />
The FortiGate unit requests a user name and password from the FortiClient user.<br />
Using these credentials, it authenticates the client and determines which VPN policy<br />
applies to the client.<br />
Provided that authentication is successful, the FortiGate unit downloads a VPN policy<br />
to the client over the SSL connection. The information includes IPsec phase 1 and<br />
phase 2 settings, and the IP addresses of the private networks that the client is<br />
authorized to access.<br />
The client uses the VPN policy settings to establish an IPsec phase 1 connection and<br />
phase 2 tunnel with the FortiGate unit.<br />
IPsec VPNs for FortiOS 4.0 MR3<br />
116 01-434-112804-20120111<br />
http://docs.fortinet.com/