fortigate-ipsec-40-mr3
fortigate-ipsec-40-mr3
fortigate-ipsec-40-mr3
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
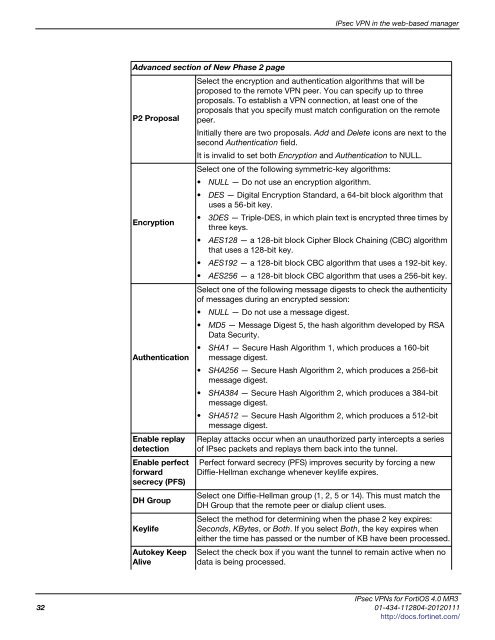
Advanced section of New Phase 2 page<br />
P2 Proposal<br />
Encryption<br />
Authentication<br />
Enable replay<br />
detection<br />
Enable perfect<br />
forward<br />
secrecy (PFS)<br />
DH Group<br />
Keylife<br />
Autokey Keep<br />
Alive<br />
IPsec VPN in the web-based manager<br />
Select the encryption and authentication algorithms that will be<br />
proposed to the remote VPN peer. You can specify up to three<br />
proposals. To establish a VPN connection, at least one of the<br />
proposals that you specify must match configuration on the remote<br />
peer.<br />
Initially there are two proposals. Add and Delete icons are next to the<br />
second Authentication field.<br />
It is invalid to set both Encryption and Authentication to NULL.<br />
Select one of the following symmetric-key algorithms:<br />
NULL — Do not use an encryption algorithm.<br />
DES — Digital Encryption Standard, a 64-bit block algorithm that<br />
uses a 56-bit key.<br />
3DES — Triple-DES, in which plain text is encrypted three times by<br />
three keys.<br />
AES128 — a 128-bit block Cipher Block Chaining (CBC) algorithm<br />
that uses a 128-bit key.<br />
AES192 — a 128-bit block CBC algorithm that uses a 192-bit key.<br />
AES256 — a 128-bit block CBC algorithm that uses a 256-bit key.<br />
Select one of the following message digests to check the authenticity<br />
of messages during an encrypted session:<br />
NULL — Do not use a message digest.<br />
MD5 — Message Digest 5, the hash algorithm developed by RSA<br />
Data Security.<br />
SHA1 — Secure Hash Algorithm 1, which produces a 160-bit<br />
message digest.<br />
SHA256 — Secure Hash Algorithm 2, which produces a 256-bit<br />
message digest.<br />
SHA384 — Secure Hash Algorithm 2, which produces a 384-bit<br />
message digest.<br />
SHA512 — Secure Hash Algorithm 2, which produces a 512-bit<br />
message digest.<br />
Replay attacks occur when an unauthorized party intercepts a series<br />
of IPsec packets and replays them back into the tunnel.<br />
Perfect forward secrecy (PFS) improves security by forcing a new<br />
Diffie-Hellman exchange whenever keylife expires.<br />
Select one Diffie-Hellman group (1, 2, 5 or 14). This must match the<br />
DH Group that the remote peer or dialup client uses.<br />
Select the method for determining when the phase 2 key expires:<br />
Seconds, KBytes, or Both. If you select Both, the key expires when<br />
either the time has passed or the number of KB have been processed.<br />
Select the check box if you want the tunnel to remain active when no<br />
data is being processed.<br />
IPsec VPNs for FortiOS 4.0 MR3<br />
32 01-434-112804-20120111<br />
http://docs.fortinet.com/