Local Area Networks (LANs) in Aircraft - FTP Directory Listing - FAA
Local Area Networks (LANs) in Aircraft - FTP Directory Listing - FAA
Local Area Networks (LANs) in Aircraft - FTP Directory Listing - FAA
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
4. NETWORK RISKS.<br />
This section specifically discusses network security issues that are directly relevant to airborne<br />
safety and security with<strong>in</strong> networked environments. Two papers authored by Daniel Mehan [18<br />
and 19], the former <strong>FAA</strong> Chief Information Officer (CIO), provide an important context for the<br />
material discussed <strong>in</strong> this section. These papers describe the cumulative processes needed to<br />
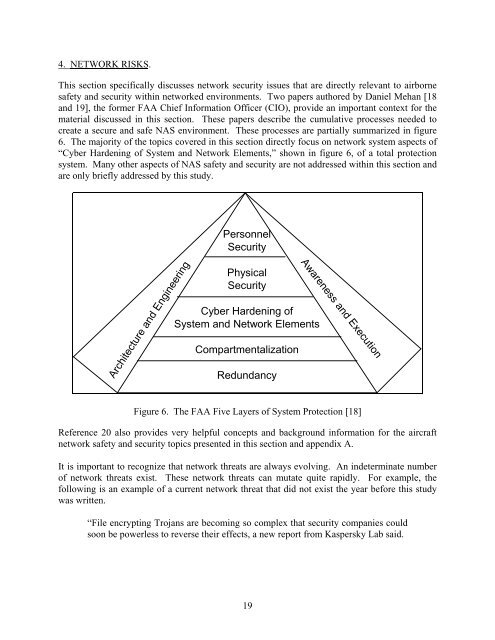
create a secure and safe NAS environment. These processes are partially summarized <strong>in</strong> figure<br />
6. The majority of the topics covered <strong>in</strong> this section directly focus on network system aspects of<br />
“Cyber Harden<strong>in</strong>g of System and Network Elements,” shown <strong>in</strong> figure 6, of a total protection<br />
system. Many other aspects of NAS safety and security are not addressed with<strong>in</strong> this section and<br />
are only briefly addressed by this study.<br />
Architecture and Eng<strong>in</strong>eer<strong>in</strong>g<br />
Personnel<br />
Security<br />
Physical<br />
Security<br />
Cyber Harden<strong>in</strong>g of<br />
System and Network Elements<br />
Compartmentalization<br />
Redundancy<br />
Awareness and Execution<br />
Figure 6. The <strong>FAA</strong> Five Layers of System Protection [18]<br />
Reference 20 also provides very helpful concepts and background <strong>in</strong>formation for the aircraft<br />
network safety and security topics presented <strong>in</strong> this section and appendix A.<br />
It is important to recognize that network threats are always evolv<strong>in</strong>g. An <strong>in</strong>determ<strong>in</strong>ate number<br />
of network threats exist. These network threats can mutate quite rapidly. For example, the<br />
follow<strong>in</strong>g is an example of a current network threat that did not exist the year before this study<br />
was written.<br />
“File encrypt<strong>in</strong>g Trojans are becom<strong>in</strong>g so complex that security companies could<br />
soon be powerless to reverse their effects, a new report from Kaspersky Lab said.<br />
19