Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
110<br />
Box 1 – The Open Service Architecture (OSA)<br />
3GPP has standardized an Open Service Architecture. This<br />
architecture defines an open API for design, implementation,<br />
control and execution and application provided by network<br />
operators and third party providers.<br />
Applications can be network/server centric or terminal centric.<br />
Terminal centric applications reside in the Mobile Station. Network/server<br />
centric applications are running outside the core<br />
network and make use of service capability features offered<br />
through the OSA API. (Note that applications may belong to the<br />
network operator domain although running outside the core network.<br />
Being outside the core network means that the applications<br />
are executed in Application Servers that are physically<br />
separated from the core network entities.)<br />
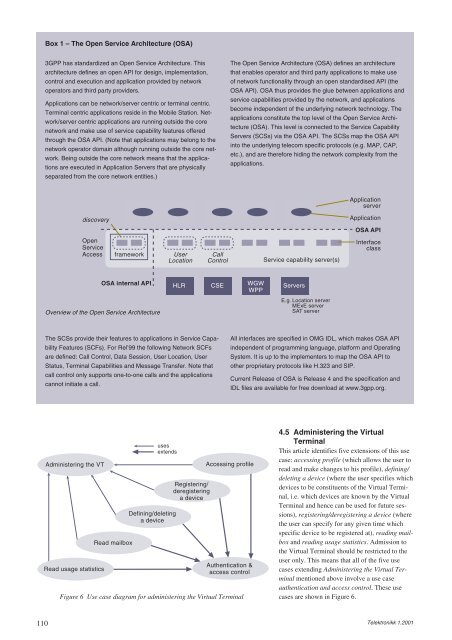
discovery<br />
Open<br />
Service<br />
Access<br />
framework User<br />
Location<br />
Overview of the Open Service Architecture<br />
Call<br />
Control<br />
OSA internal API HLR CSE WGW<br />
WPP<br />
The SCSs provide their features to applications in Service Capability<br />
Features (SCFs). For Rel’99 the following Network SCFs<br />
are defined: Call Control, Data Session, User Location, User<br />
Status, Terminal Capabilities and Message Transfer. Note that<br />
call control only supports one-to-one calls and the applications<br />
cannot initiate a call.<br />
Administering the VT<br />
Read usage statistics<br />
Read mailbox<br />
uses<br />
extends<br />
Defining/deleting<br />
a device<br />
Registering/<br />
deregistering<br />
a device<br />
Figure 6 Use case diagram for administering the Virtual Terminal<br />
The Open Service Architecture (OSA) defines an architecture<br />
that enables operator and third party applications to make use<br />
of network functionality through an open standardised API (the<br />
OSA API). OSA thus provides the glue between applications and<br />
service capabilities provided by the network, and applications<br />
become independent of the underlying network technology. The<br />
applications constitute the top level of the Open Service Architecture<br />
(OSA). This level is connected to the Service Capability<br />
Servers (SCSs) via the OSA API. The SCSs map the OSA API<br />
into the underlying telecom specific protocols (e.g. MAP, CAP,<br />
etc.), and are therefore hiding the network complexity from the<br />
applications.<br />
Service capability server(s)<br />
Servers<br />
E.g. Location server<br />
MExE server<br />
SAT server<br />
Application<br />
server<br />
Application<br />
OSA API<br />
Interface<br />
class<br />
All interfaces are specified in OMG IDL, which makes OSA API<br />
independent of programming language, platform and Operating<br />
System. It is up to the implementers to map the OSA API to<br />
other proprietary protocols like H.323 and SIP.<br />
Current Release of OSA is Release 4 and the specification and<br />
IDL files are available for free download at www.3gpp.org.<br />
Accessing profile<br />
Authentication &<br />
access control<br />
4.5 Administering the Virtual<br />
Terminal<br />
This article identifies five extensions of this use<br />
case: accessing profile (which allows the user to<br />
read and make changes to his profile), defining/<br />
deleting a device (where the user specifies which<br />
devices to be constituents of the Virtual Terminal,<br />
i.e. which devices are known by the Virtual<br />
Terminal and hence can be used for future sessions),<br />
registering/deregistering a device (where<br />
the user can specify for any given time which<br />
specific device to be registered at), reading mailbox<br />
and reading usage statistics. Admission to<br />
the Virtual Terminal should be restricted to the<br />
user only. This means that all of the five use<br />
cases extending Administering the Virtual Terminal<br />
mentioned above involve a use case<br />
authentication and access control. These use<br />
cases are shown in Figure 6.<br />
Telektronikk 1.2001