Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
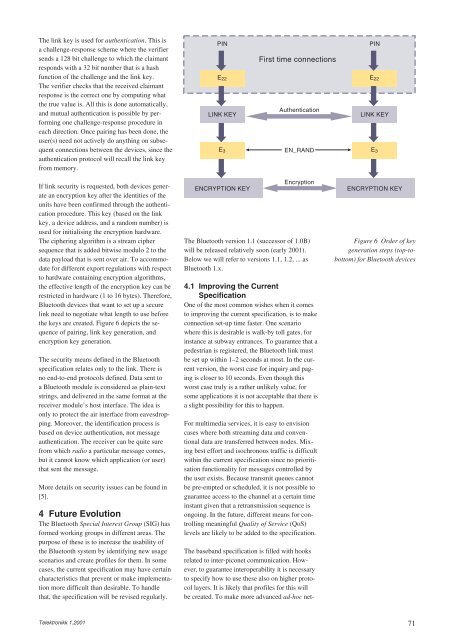
The link key is used for authentication. This is<br />
a challenge-response scheme where the verifier<br />
sends a 128 bit challenge to which the claimant<br />
responds with a 32 bit number that is a hash<br />
function of the challenge and the link key.<br />
The verifier checks that the received claimant<br />
response is the correct one by computing what<br />
the true value is. All this is done automatically,<br />
and mutual authentication is possible by performing<br />
one challenge-response procedure in<br />
each direction. Once pairing has been done, the<br />
user(s) need not actively do anything on subsequent<br />
connections between the devices, since the<br />
authentication protocol will recall the link key<br />
from memory.<br />
If link security is requested, both devices generate<br />
an encryption key after the identities of the<br />
units have been confirmed through the authentication<br />
procedure. This key (based on the link<br />
key, a device address, and a random number) is<br />
used for initialising the encryption hardware.<br />
The ciphering algorithm is a stream cipher<br />
sequence that is added bitwise modulo 2 to the<br />
data payload that is sent over air. To accommodate<br />
for different export regulations with respect<br />
to hardware containing encryption algorithms,<br />
the effective length of the encryption key can be<br />
restricted in hardware (1 to 16 bytes). Therefore,<br />
Bluetooth devices that want to set up a secure<br />
link need to negotiate what length to use before<br />
the keys are created. Figure 6 depicts the sequence<br />
of pairing, link key generation, and<br />
encryption key generation.<br />
The security means defined in the Bluetooth<br />
specification relates only to the link. There is<br />
no end-to-end protocols defined. Data sent to<br />
a Bluetooth module is considered as plain-text<br />
strings, and delivered in the same format at the<br />
receiver module’s host interface. The idea is<br />
only to protect the air interface from eavesdropping.<br />
Moreover, the identification process is<br />
based on device authentication, not message<br />
authentication. The receiver can be quite sure<br />
from which radio a particular message comes,<br />
but it cannot know which application (or user)<br />
that sent the message.<br />
More details on security issues can be found in<br />
[5].<br />
4 <strong>Future</strong> Evolution<br />
The Bluetooth Special Interest Group (SIG) has<br />
formed working groups in different areas. The<br />
purpose of these is to increase the usability of<br />
the Bluetooth system by identifying new usage<br />
scenarios and create profiles for them. In some<br />
cases, the current specification may have certain<br />
characteristics that prevent or make implementation<br />
more difficult than desirable. To handle<br />
that, the specification will be revised regularly.<br />
Telektronikk 1.2001<br />
PIN<br />
E22<br />
LINK KEY<br />
E3<br />
ENCRYPTION KEY<br />
First time connections<br />
Authentication<br />
EN_RAND<br />
Encryption<br />
The Bluetooth version 1.1 (successor of 1.0B)<br />
will be released relatively soon (early 2001).<br />
Below we will refer to versions 1.1, 1.2, ... as<br />
Bluetooth 1.x.<br />
4.1 Improving the Current<br />
Specification<br />
One of the most common wishes when it comes<br />
to improving the current specification, is to make<br />
connection set-up time faster. One scenario<br />
where this is desirable is walk-by toll gates, for<br />
instance at subway entrances. To guarantee that a<br />
pedestrian is registered, the Bluetooth link must<br />
be set up within 1–2 seconds at most. In the current<br />
version, the worst case for inquiry and paging<br />
is closer to 10 seconds. Even though this<br />
worst case truly is a rather unlikely value, for<br />
some applications it is not acceptable that there is<br />
a slight possibility for this to happen.<br />
For multimedia services, it is easy to envision<br />
cases where both streaming data and conventional<br />
data are transferred between nodes. Mixing<br />
best effort and isochronous traffic is difficult<br />
within the current specification since no prioritisation<br />
functionality for messages controlled by<br />
the user exists. Because transmit queues cannot<br />
be pre-empted or scheduled, it is not possible to<br />
guarantee access to the channel at a certain time<br />
instant given that a retransmission sequence is<br />
ongoing. In the future, different means for controlling<br />
meaningful Quality of Service (QoS)<br />
levels are likely to be added to the specification.<br />
The baseband specification is filled with hooks<br />
related to inter-piconet communication. However,<br />
to guarantee interoperability it is necessary<br />
to specify how to use these also on higher protocol<br />
layers. It is likely that profiles for this will<br />
be created. To make more advanced ad-hoc net-<br />
PIN<br />
E22<br />
LINK KEY<br />
E3<br />
ENCRYPTION KEY<br />
Figure 6 Order of key<br />
generation steps (top-tobottom)<br />
for Bluetooth devices<br />
71