RingMaster Management Guide - Juniper Networks
RingMaster Management Guide - Juniper Networks
RingMaster Management Guide - Juniper Networks
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
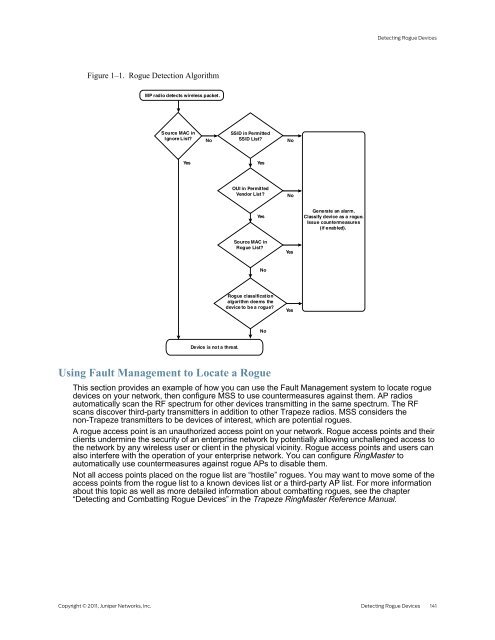
Figure 1–1. Rogue Detection Algorithm<br />
MP radio detects wireless packet.<br />
Source MAC in<br />
Ignore List?<br />
No<br />
SSID in Permitted<br />
SSID List?<br />
No<br />
Yes Yes<br />
Device is not a threat.<br />
OUI in Permitted<br />
Vendor List?<br />
Detecting Rogue Devices<br />
Copyright © 2011, <strong>Juniper</strong> <strong>Networks</strong>, Inc. Detecting Rogue Devices 141<br />
Yes<br />
Source MAC in<br />
Rogue List?<br />
No<br />
Rogue classification<br />
algorithm deems the<br />
device to be a rogue?<br />
Using Fault <strong>Management</strong> to Locate a Rogue<br />
No<br />
No<br />
Yes<br />
Yes<br />
Generate an alarm.<br />
Classify device as a rogue.<br />
Issue countermeasures<br />
(if enabled).<br />
This section provides an example of how you can use the Fault <strong>Management</strong> system to locate rogue<br />
devices on your network, then configure MSS to use countermeasures against them. AP radios<br />
automatically scan the RF spectrum for other devices transmitting in the same spectrum. The RF<br />
scans discover third-party transmitters in addition to other Trapeze radios. MSS considers the<br />
non-Trapeze transmitters to be devices of interest, which are potential rogues.<br />
A rogue access point is an unauthorized access point on your network. Rogue access points and their<br />
clients undermine the security of an enterprise network by potentially allowing unchallenged access to<br />
the network by any wireless user or client in the physical vicinity. Rogue access points and users can<br />
also interfere with the operation of your enterprise network. You can configure <strong>RingMaster</strong> to<br />
automatically use countermeasures against rogue APs to disable them.<br />
Not all access points placed on the rogue list are “hostile” rogues. You may want to move some of the<br />
access points from the rogue list to a known devices list or a third-party AP list. For more information<br />
about this topic as well as more detailed information about combatting rogues, see the chapter<br />
“Detecting and Combatting Rogue Devices” in the Trapeze <strong>RingMaster</strong> Reference Manual.