RingMaster Management Guide - Juniper Networks
RingMaster Management Guide - Juniper Networks
RingMaster Management Guide - Juniper Networks
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Ignoring Friendly Third-Party Devices<br />
By default, when countermeasures are enabled, MSS considers any third-party transmitter to be a<br />
rogue device and can send countermeasures to prevent clients from using that device. To prevent<br />
MSS from sending countermeasures against a friendly device, add the device to the Ignore list.<br />
Each MX has an Ignore list. You can add an address to the Ignore list of one or multiple MXs.<br />
To add a device to the Ignore list:<br />
1. In the list of rogues on the Alarm screen, select the devices to add to the Ignore list.<br />
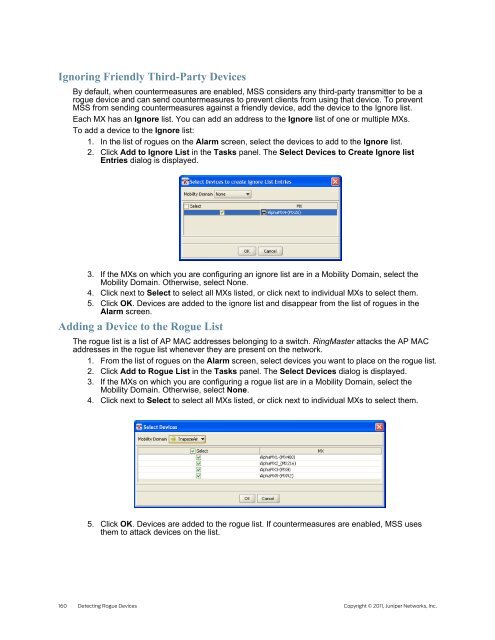
2. Click Add to Ignore List in the Tasks panel. The Select Devices to Create Ignore list<br />
Entries dialog is displayed.<br />
3. If the MXs on which you are configuring an ignore list are in a Mobility Domain, select the<br />
Mobility Domain. Otherwise, select None.<br />
4. Click next to Select to select all MXs listed, or click next to individual MXs to select them.<br />
5. Click OK. Devices are added to the ignore list and disappear from the list of rogues in the<br />
Alarm screen.<br />
Adding a Device to the Rogue List<br />
The rogue list is a list of AP MAC addresses belonging to a switch. <strong>RingMaster</strong> attacks the AP MAC<br />
addresses in the rogue list whenever they are present on the network.<br />
1. From the list of rogues on the Alarm screen, select devices you want to place on the rogue list.<br />
2. Click Add to Rogue List in the Tasks panel. The Select Devices dialog is displayed.<br />
3. If the MXs on which you are configuring a rogue list are in a Mobility Domain, select the<br />
Mobility Domain. Otherwise, select None.<br />
4. Click next to Select to select all MXs listed, or click next to individual MXs to select them.<br />
5. Click OK. Devices are added to the rogue list. If countermeasures are enabled, MSS uses<br />
them to attack devices on the list.<br />
160 Detecting Rogue Devices Copyright © 2011, <strong>Juniper</strong> <strong>Networks</strong>, Inc.