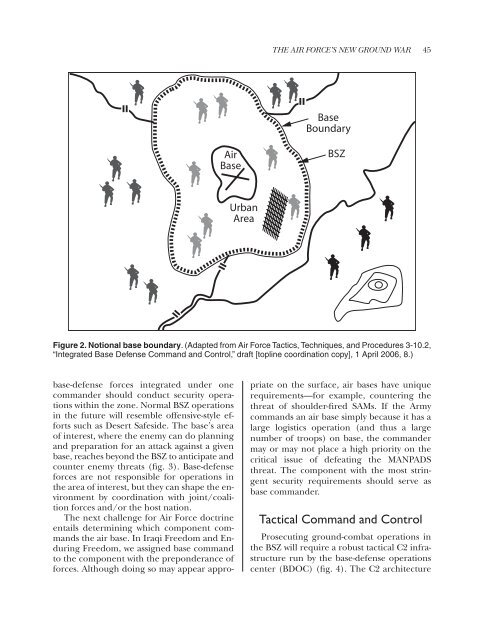
44 AIR & SPACE POWER JOURNAL FALL <strong>2006</strong>The Base Security ZoneWhereas legacy base-defense doctrine wasdesigned for Cold War–era linear battlefields,emerging joint doctrine treats expeditionarybases more like joint operating areas (fig. 1).The final draft of Joint Publication 3-10, “JointSecurity Operations in Theater,” adapts thebest practices of defending bases to the nonlinearbattlefields of today. The core of thisdoctrine seeks to ensure that the designatedbase commander can dominate the area aroundthe base from which the enemy can launchstandoff and penetrating attacks. Importantly,the new publication establishes a BSZ as ajoint operating area around critical fixed installations(such as air bases) and describesterrain that the base commander should influenceas the battlespace from which the enemycan attack the base. The fact that this terrainincludes the area traditionally known as theman-portable air defense system (MANPADS)footprint (the area the enemy could use to attackaircraft approaching/departing the basewith shoulder-launched SAMs) is of criticalimportance to the <strong>Air</strong> <strong>Force</strong>. This requirementof influencing terrain outside the fencecreated a new battlefield-control measurecalled the “base boundary” (fig. 2), defined inthe joint publication asa line that delineates the surface area of a basefor the purpose of facilitating coordination anddeconfliction of operations between adjacentunits, formations, or areas. The base boundaryis not necessarily the base perimeter; rather itshould be established based upon the factors ofmission, enemy, terrain and weather, troops andother support available, time available (METT-T),specifically balancing the need of the base defenseforces to control key terrain with theirability to accomplish the mission. 10Because the terrain included in the baseboundary is subject to constraints of the landcomponent or host nation, the <strong>Air</strong> <strong>Force</strong> willuse the BSZ to internally address the total areaoutside the base perimeter that might threatenthe base with standoff attacks. The optimaljoint situation would have the BSZ and baseboundary encompassing the same terrain.Analysis of the base’s mission as well as theenemy, terrain, time, troops available, and civilianconsiderations will determine the BSZ,which surrounds the base. Historical knowledgeof the enemy’s use of standoff weaponslike rockets and mortars in Vietnam, togetherwith recent experience in Iraq and Afghanistan,shows that the BSZ must extend a minimumof five kilometers from base resources(e.g., aircraft operating surfaces, maintenancefacilities, and billeting locations). DedicatedFigure 1. Emerging joint nonlinear battlefield. (Adapted from briefing, Command and Control GeneralOfficer Steering Group, subject: Headquarters USAF/XOS-F Integrated Base Defense Command andControl, 3 November 2004.)
THE AIR FORCE’S NEW GROUND WAR 45BaseBoundary<strong>Air</strong>BaseBSZUrbanAreaFigure 2. Notional base boundary. (Adapted from <strong>Air</strong> <strong>Force</strong> Tactics, Techniques, and Procedures 3-10.2,“Integrated Base Defense Command and Control,” draft [topline coordination copy], 1 April <strong>2006</strong>, 8.)base-defense forces integrated under onecommander should conduct security operationswithin the zone. Normal BSZ operationsin the future will resemble offensive-style effortssuch as Desert Safeside. The base’s areaof interest, where the enemy can do planningand preparation for an attack against a givenbase, reaches beyond the BSZ to anticipate andcounter enemy threats (fig. 3). Base-defenseforces are not responsible for operations inthe area of interest, but they can shape the environmentby coordination with joint/coalitionforces and/or the host nation.The next challenge for <strong>Air</strong> <strong>Force</strong> doctrineentails determining which component commandsthe air base. In Iraqi Freedom and EnduringFreedom, we assigned base commandto the component with the preponderance offorces. Although doing so may appear appropriateon the surface, air bases have uniquerequirements—for example, countering thethreat of shoulder-fired SAMs. If the Armycommands an air base simply because it has alarge logistics operation (and thus a largenumber of troops) on base, the commandermay or may not place a high priority on thecritical issue of defeating the MANPADSthreat. The component with the most stringentsecurity requirements should serve asbase commander.Tactical Command and ControlProsecuting ground-combat operations inthe BSZ will require a robust tactical C2 infrastructurerun by the base-defense operationscenter (BDOC) (fig. 4). The C2 architecture
- Page 2 and 3: Chief of Staff, US Air ForceGen T.
- Page 4 and 5: PIREPsJoint Airspace Management and
- Page 6 and 7: APJInterdependenceKey to Our Common
- Page 8 and 9: 6 AIR & SPACE POWER JOURNAL FALL 20
- Page 10 and 11: APJLT COL PAUL D. B ERG , USAF, CHI
- Page 12 and 13: 10 AIR & SPACE POWER JOURNAL FALL 2
- Page 14 and 15: ASPJLT COL PAUL D. B ERG , USAF, CH
- Page 16 and 17: True to form, the Air Force has res
- Page 18 and 19: Red Flag Still Matters—After AllT
- Page 20 and 21: Integration of Space-BasedCombat Sy
- Page 22 and 23: est alternative. In other cases, un
- Page 25 and 26: power projection, but advances in a
- Page 27 and 28: 3. Report of the Commission to Asse
- Page 29 and 30: PIREP 27ized, programmed, funded, a
- Page 31 and 32: PIREP 29creation of ACMs. One antic
- Page 33 and 34: PIREP 31Link 16 and Joint Airspace
- Page 35 and 36: PIREP 33Missile Defense Systems, th
- Page 37 and 38: CADRE’s Professional EducationOpp
- Page 39 and 40: ASPJQuick-LookThe Air Force Needs N
- Page 41 and 42: QUICK-LOOK 39system should become a
- Page 43 and 44: APJThe Air Force’s New Ground War
- Page 45: THE AIR FORCE’S NEW GROUND WAR 43
- Page 49 and 50: THE AIR FORCE’S NEW GROUND WAR 47
- Page 51 and 52: THE AIR FORCE’S NEW GROUND WAR 49
- Page 53 and 54: THE AIR FORCE’S NEW GROUND WAR 51
- Page 55 and 56: New USAF Doctrine PublicationAir Fo
- Page 57 and 58: Counterinsurgency AirpowerAir-Groun
- Page 59 and 60: COUNTERINSURGENCY AIRPOWER 57ticula
- Page 61 and 62: COUNTERINSURGENCY AIRPOWER 59and Ai
- Page 63 and 64: COUNTERINSURGENCY AIRPOWER 61The af
- Page 65 and 66: COUNTERINSURGENCY AIRPOWER 63squadr
- Page 67 and 68: ASPJQuick-LookA New Operational Ass
- Page 69 and 70: QUICK-LOOK 67den on the OAT. First,
- Page 71 and 72: Filling the Stealth Gap and Enhanci
- Page 73 and 74: FILLING THE STEALTH GAP 71Each of t
- Page 75 and 76: FILLING THE STEALTH GAP 73the US wa
- Page 77 and 78: FILLING THE STEALTH GAP 75mit the F
- Page 79 and 80: Space PowerAn Ill-Suited SpaceStrat
- Page 81 and 82: SPACE POWER 79by using a more encom
- Page 83 and 84: SPACE POWER 81role of offensive and
- Page 85 and 86: SPACE POWER 83achieve supremacy in
- Page 87 and 88: Military TransformationEnds,Ways, a
- Page 89 and 90: MILITARY TRANSFORMATION 87to organi
- Page 91 and 92: MILITARY TRANSFORMATION 89course, w
- Page 93 and 94: MILITARY TRANSFORMATION 91mind-set
- Page 95 and 96: MILITARY TRANSFORMATION 93sponding
- Page 97 and 98:
NOTAM 95The document’s authors ha
- Page 99 and 100:
MOLECULAR NANOTECHNOLOGY AND NATION
- Page 101 and 102:
MOLECULAR NANOTECHNOLOGY AND NATION
- Page 103 and 104:
MOLECULAR NANOTECHNOLOGY AND NATION
- Page 105 and 106:
MOLECULAR NANOTECHNOLOGY AND NATION
- Page 107 and 108:
MOLECULAR NANOTECHNOLOGY AND NATION
- Page 109 and 110:
ASPJQuick-LookThe Nature of Close A
- Page 111 and 112:
QUICK-LOOK 109CAS missions. The pub
- Page 113 and 114:
Clausewitz and the Falkland Islands
- Page 115 and 116:
CLAUSEWITZ AND THE FALKLAND ISLANDS
- Page 117 and 118:
CLAUSEWITZ AND THE FALKLAND ISLANDS
- Page 119 and 120:
CLAUSEWITZ AND THE FALKLAND ISLANDS
- Page 121 and 122:
CLAUSEWITZ AND THE FALKLAND ISLANDS
- Page 123 and 124:
BOOK REVIEWS 121whose contributions
- Page 125 and 126:
BOOK REVIEWS 123Franco: Soldier, Co
- Page 127 and 128:
APJAir and Space Power Journal, the
- Page 129 and 130:
CONTRIBUTORS 127Col Howard D. “Da
- Page 131:
EDITORIAL ADVISORY BOARDGen John A.