6th European Conference - Academic Conferences
6th European Conference - Academic Conferences
6th European Conference - Academic Conferences
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Vincent Garramone and Daniel Likarish<br />
Note: A positive in the Match column indicates that the seeded taxonomy terms were closely or<br />
exactly reflected in the Regis lab topic.<br />
This rudimentary analysis demonstrated that seeding the forensics vocabulary with terms extracted<br />
from a public literature search might be sufficient to allow a moderator to characterize the uploaded<br />
material without intimate knowledge of its contents. See Appendix 2 for a visual representation of this<br />
mapping in table form for the course MSIA 682, Network Forensics. It is clear, however, that the initial<br />
vocabulary could benefit from adjustments. For example, the lab description in row 2 of Table 2<br />
mentions, “packet capture”. While this is not in the initial vocabulary, it is closely related to “Network<br />
Forensics” and “Packet Analysis”. Network Forensics was included in the initial list and Packet<br />
Analysis, while identified in the literature, was not for reasons described above. To address this, it<br />
might be appropriate to replace “Network Forensics” with “Packet Analysis” in the PRISM vocabulary.<br />
Alternatively, defining the relationship of these terms in PRISM (synonyms, subtopics, etc.) might<br />
create a more inclusive and useful search environment.<br />
4.4 Honing the vocabulary<br />
The artifact constructed through literature review is, as mentioned, a starting point in the development<br />
of an optimized digital forensics vocabulary for PRISM. It remains to be seen if these terms resonate<br />
with other users of the web portal or if different descriptors will be favored. Moreover, terminology<br />
changes over time, and PRISM’s vocabularies should be able to accommodate those changes. The<br />
authors plan to utilize new content and analytics data to identify discrepancies between the<br />
vocabulary defined above, and actual topics and terms utilized by PRISM users. PRISM records all<br />
searches performed on the site and generates reports listing common phrases. Searches are also<br />
tracked by Google Analytics, which provides a more in-depth view of searches executed on the site,<br />
as well as visitor behavior before and after the search. After a particular search is executed, Google<br />
services can be used to determine user’s preferred or selected materials. This capability can provide<br />
insight into how accurate and relevant the taxonomies are at any given time. As long as usage of the<br />
site continues, these tools will help PRISM moderators to maintain relevant IA vocabularies from<br />
which content can be described.<br />
5. Conclusions<br />
IA is a rapidly changing field, and maintaining relevance is a difficult task. We are attempting to keep<br />
PRISM responsive to changes in the IA landscape. PRISM developers will continue to make<br />
adjustments based on the needs of the user community by allowing current literature and actual<br />
usage statistics to guide the development of organizational taxonomies. Explicitly attaching these<br />
relevant descriptors to site content allows administrators to produce intuitive, guided search<br />
functionalities, making it easier for users to locate the materials they need. Results using our own<br />
materials as a test case suggest that taxonomies constructed in this way could be effective for other<br />
users. A more rigorous evaluation will only be possible if site utilization increases and is sustained<br />
over a significant period of time. To this end, PRISM moderators recognize, and are prepared to<br />
absorb, the increased work required to properly organize content on the site as taxonomic complexity<br />
increases. This will hopefully make using the site more attractive to content developers and, in turn, to<br />
those seeking educational resources.<br />
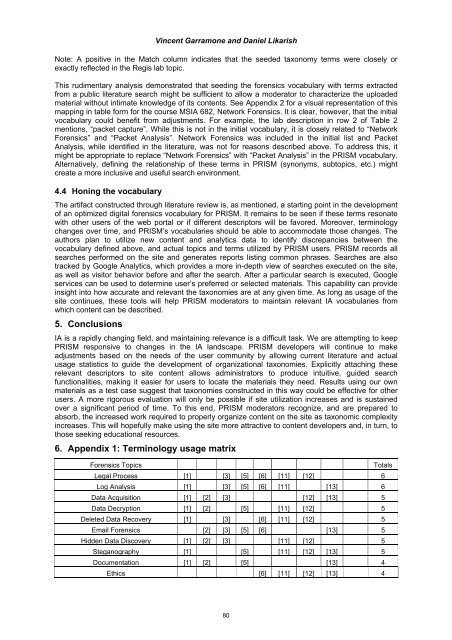
6. Appendix 1: Terminology usage matrix<br />
Forensics Topics Totals<br />
Legal Process [1] [3] [5] [6] [11] [12] 6<br />
Log Analysis [1] [3] [5] [6] [11] [13] 6<br />
Data Acquisition [1] [2] [3] [12] [13] 5<br />
Data Decryption [1] [2] [5] [11] [12] 5<br />
Deleted Data Recovery [1] [3] [6] [11] [12] 5<br />
Email Forensics [2] [3] [5] [6] [13] 5<br />
Hidden Data Discovery [1] [2] [3] [11] [12] 5<br />
Steganography [1] [5] [11] [12] [13] 5<br />
Documentation [1] [2] [5] [13] 4<br />
Ethics [6] [11] [12] [13] 4<br />
80