6th European Conference - Academic Conferences
6th European Conference - Academic Conferences
6th European Conference - Academic Conferences
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Vincent Garramone and Daniel Likarish<br />
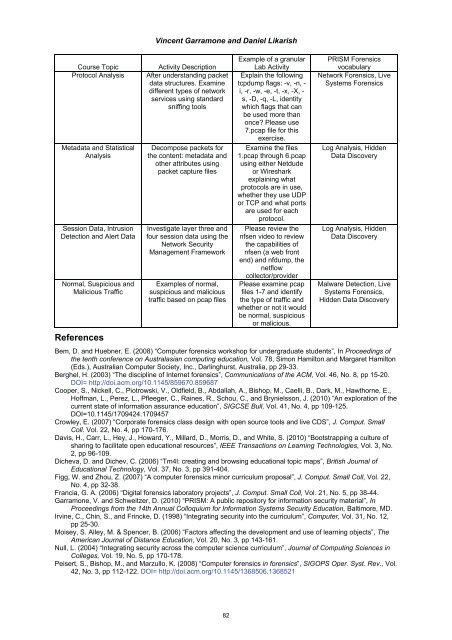
Course Topic Activity Description<br />
Protocol Analysis After understanding packet<br />
data structures. Examine<br />
different types of network<br />
services using standard<br />
sniffing tools<br />
Metadata and Statistical<br />
Analysis<br />
Session Data, Intrusion<br />
Detection and Alert Data<br />
Normal, Suspicious and<br />
Malicious Traffic<br />
References<br />
Decompose packets for<br />
the content: metadata and<br />
other attributes using<br />
packet capture files<br />
Investigate layer three and<br />
four session data using the<br />
Network Security<br />
Management Framework<br />
Examples of normal,<br />
suspicious and malicious<br />
traffic based on pcap files<br />
Example of a granular<br />
Lab Activity<br />
Explain the following<br />
tcpdump flags: -v, -n, -<br />
i, -r, -w, -e, -t, -x, -X, -<br />
s, -D, -q, -L, identity<br />
which flags that can<br />
be used more than<br />
once? Please use<br />
7.pcap file for this<br />
exercise.<br />
Examine the files<br />
1.pcap through 6.pcap<br />
using either Netdude<br />
or Wireshark<br />
explaining what<br />
protocols are in use,<br />
whether they use UDP<br />
or TCP and what ports<br />
are used for each<br />
protocol.<br />
Please review the<br />
nfsen video to review<br />
the capabilities of<br />
nfsen (a web front<br />
end) and nfdump, the<br />
netflow<br />
collector/provider<br />
Please examine pcap<br />
files 1-7 and identify<br />
the type of traffic and<br />
whether or not it would<br />
be normal, suspicious<br />
or malicious.<br />
PRISM Forensics<br />
vocabulary<br />
Network Forensics, Live<br />
Systems Forensics<br />
Log Analysis, Hidden<br />
Data Discovery<br />
Log Analysis, Hidden<br />
Data Discovery<br />
Malware Detection, Live<br />
Systems Forensics,<br />
Hidden Data Discovery<br />
Bem, D. and Huebner, E. (2008) “Computer forensics workshop for undergraduate students”, In Proceedings of<br />
the tenth conference on Australasian computing education, Vol. 78, Simon Hamilton and Margaret Hamilton<br />
(Eds.), Australian Computer Society, Inc., Darlinghurst, Australia, pp 29-33.<br />
Berghel, H. (2003) “The discipline of Internet forensics”, Communications of the ACM, Vol. 46, No. 8, pp 15-20.<br />
DOI= http://doi.acm.org/10.1145/859670.859687<br />
Cooper, S., Nickell, C., Piotrowski, V., Oldfield, B., Abdallah, A., Bishop, M., Caelli, B., Dark, M., Hawthorne, E.,<br />
Hoffman, L., Perez, L., Pfleeger, C., Raines, R., Schou, C., and Brynielsson, J. (2010) “An exploration of the<br />
current state of information assurance education”, SIGCSE Bull, Vol. 41, No. 4, pp 109-125.<br />
DOI=10.1145/1709424.1709457<br />
Crowley, E. (2007) “Corporate forensics class design with open source tools and live CDS”, J. Comput. Small<br />
Coll. Vol. 22, No. 4, pp 170-176.<br />
Davis, H., Carr, L., Hey, J., Howard, Y., Millard, D., Morris, D., and White, S. (2010) “Bootstrapping a culture of<br />
sharing to facilitate open educational resources”, IEEE Transactions on Learning Technologies, Vol. 3, No.<br />
2, pp 96-109.<br />
Dicheva, D. and Dichev, C. (2006) “Tm4l: creating and browsing educational topic maps”, British Journal of<br />
Educational Technology, Vol. 37, No. 3, pp 391-404.<br />
Figg, W. and Zhou, Z. (2007) “A computer forensics minor curriculum proposal”, J. Comput. Small Coll, Vol. 22,<br />
No. 4, pp 32-38.<br />
Francia, G. A. (2006) “Digital forensics laboratory projects”, J. Comput. Small Coll, Vol. 21, No. 5, pp 38-44.<br />
Garramone, V. and Schweitzer, D. (2010) “PRISM: A public repository for information security material”, In<br />
Proceedings from the 14th Annual Colloquium for Information Systems Security Education, Baltimore, MD.<br />
Irvine, C., Chin, S., and Frincke, D. (1998) “Integrating security into the curriculum”, Computer, Vol. 31, No. 12,<br />
pp 25-30.<br />
Moisey, S. Alley, M. & Spencer, B. (2006) “Factors affecting the development and use of learning objects”, The<br />
American Journal of Distance Education, Vol. 20, No. 3, pp 143-161.<br />
Null, L. (2004) “Integrating security across the computer science curriculum”, Journal of Computing Sciences in<br />
Colleges, Vol. 19, No. 5, pp 170-178.<br />
Peisert, S., Bishop, M., and Marzullo, K. (2008) “Computer forensics in forensics”, SIGOPS Oper. Syst. Rev., Vol.<br />
42, No. 3, pp 112-122. DOI= http://doi.acm.org/10.1145/1368506.1368521<br />
82