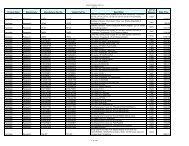
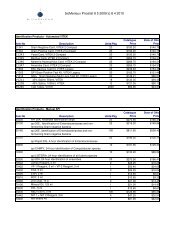
REQUEST FOR PROPOSALS RFP NUMBER: 0A1031 DATE ISSUED
REQUEST FOR PROPOSALS RFP NUMBER: 0A1031 DATE ISSUED
REQUEST FOR PROPOSALS RFP NUMBER: 0A1031 DATE ISSUED
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
SUPPLEMENT TWO<br />
MANDATORY REQUIREMENT<br />
IT ESSENTIAL TECHNICAL ARCHITECTURE <strong>FOR</strong><br />
INFRASTRUCTURE COMPATIBILITY<br />
ODPS IT Infrastructure (01/07)<br />
All new technologies must follow current methodologies of industry best practices as described by Microsoft.<br />
Background:<br />
ODPS IT provides the networking, hardware and software for the ODPS, ATPS, Deputy, Highway Patrol,<br />
Investigative Unit, Reinstatement Centers and other ODPS business units. ODPS currently provides Network<br />
connectivity for hundreds of external sites, for various Divisions within ODPS. This connectivity terminates at two<br />
(2) Data Centers.<br />
Networking Topology:<br />
All sites use 10/100/1000baseT Ethernet for all user & server segments. All satellite offices are connected via a<br />
T1 bandwidth frame relay connections. The satellite offices utilize Ethernet for their user segments. ODPS<br />
utilizes TCP/IP as its standard networking protocol.<br />
User LAN:<br />
ODPS currently uses Windows XP Pro, and Windows 2000 clients and Windows 2000 Server, Windows 2003 and<br />
Novell Netware Operating systems and Active Directory or eDirectory for authentication. eDirectory and Novell<br />
Netware are for file and print and are expected to be replaced shortly by Windows file and print services.<br />
Enterprise Application Infrastructure:<br />
ODPS currently uses Microsoft Windows 2000/2003 Servers as its application server platform. ODPS also<br />
utilizes Unisys Mainframe 7800 Series technology and high end Server technology in the form of Unisys<br />
ES7000’s.<br />
For Internet applications, ODPS requires an n-tier Architecture containing a web farm for the presentation tier, a<br />
hardware load balanced application / business tier and a clustered database tier. Applications are to be stateless<br />
and object oriented. Applications will be developed using Visual Studio 2005 Suite Professional or Team Suite<br />
with code being written in Visual Basic unless otherwise stated. All database interaction will be via stored<br />
procedure.<br />
Application Security:<br />
Security should be determined on a case by case basis, based on the # of users, sensitivity of the data, and how<br />
data is accessed. Some organizations access data on behalf of their employees. Active Directory, table based<br />
security (username and password) and collecting items such as Driver's License Number, Date of Birth and last<br />
four digits of the person's social security number to validate against the operator license database are the normal<br />
authentication mechanisms.<br />
Database:<br />
ODPS utilizes Microsoft SQL Server database primarily. Any new applications need to utilize Microsoft SQL<br />
Server. Oracle databases are present. DB2 is also present. Oracle and DB2 are not a strategic direction for<br />
ODPS.<br />
Database is accessed through MDAC, ODBC, OLEDB, WCF connections and WEB services.<br />
Enterprise Storage:<br />
ODPS utilizes EMC SAN and NAS storage within both Data Centers and copies certain data between the centers<br />
for backup and redundancy. ODPS utilizes EMC DMX for high end transactional storage, EMC Celerra for NAS<br />
storage, EMC Clarion for mid-range economical storage and EMC Centera for Token based storage. Each<br />
server application is reviewed to decide which storage is best suited for the application. Then backup and<br />
recovery needs are reviewed to decide the best method for redundancy and timeliness of recovery.<br />
Security:<br />
Generally speaking, ODPS does not allow direct connections from outside sources to internal systems. All<br />
externally and most internally available applications are designed in a multi-tier security model utilizing full client<br />
disconnects. No http proxy based applications are allowed. ODPS restricts the IP application ports that are<br />
allowed to traverse networks. ODPS does not allow dynamic port allocation applications. ODPS considers any<br />
machine that is directly accessed by an outside entity as a perimeter device and restricts accordingly.<br />
Remote Access:<br />
ODPS does not allow direct connections to any machine located on the ODPS network by Vendors or