REQUEST FOR PROPOSALS RFP NUMBER: 0A1031 DATE ISSUED
REQUEST FOR PROPOSALS RFP NUMBER: 0A1031 DATE ISSUED
REQUEST FOR PROPOSALS RFP NUMBER: 0A1031 DATE ISSUED
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
attempt to deter compromise. The addition or deletion of security features will cause an<br />
adjustment to be made in the final cost of the card based upon the price listed in Attachment<br />
Nine, Cost Summary.<br />
The produced documents must provide the maximum resistance to compromise attempts via the<br />
following methods:<br />
Type 1: Counterfeit / simulation<br />
An unauthorized copy or reproduction of a genuine card made by whatever means.<br />
Type 2: Alteration<br />
Includes but is not limited to deletion, modification, erasure, masking, or tampering with<br />
biographical data concerning the original or rightful cardholder.<br />
Type 3: Photo / signature substitution<br />
Substitution of an impostor’s photograph and/or signature in place of the photograph and/or<br />
signature of the original or rightful cardholder.<br />
Type 4: Counterfeit from cannibalized cards<br />
Creation of a fraudulent document using card components from legitimate DL/ID cards.<br />
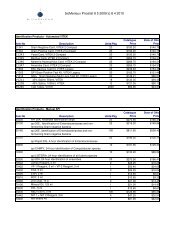
B. DL/ID Cards must include three levels of security features as indicated in the Card Design<br />
Security Features Chart (see Attachment Nine, Cost Summary). Both the DL and ID cards must<br />
be secure documents, verifiable as original through complementary security features included for<br />
three levels of inspection:<br />
Level One – Cursory examination without tools or aids involves easily identifiable visual or tactile<br />
features for rapid inspection at point of usage. Important Note: The Contractor’s<br />
manufacturing/application method for Level One security features may be declared proprietary<br />
information/trade secret, but the finished security feature itself shall not be declared proprietary<br />
information by the Contractor.<br />
Level Two – Examination by trained inspectors with simple equipment (magnifying glass, UV<br />
light, machine reading equipment, etc). Important Note: The Contractor’s<br />
manufacturing/application method for Level Two security features may be declared proprietary<br />
information/trade secret, but the finished security feature itself shall not be declared proprietary<br />
information by the Contractor.<br />
Level Three – Inspection by forensic specialists conducting detailed examination allows for more<br />
in-depth evaluation and may require special equipment to provide true certification.<br />
If Ohio issues REAL ID compliant credentials, the Contractor will be required to include all<br />
security levels, including all threat levels required by the REAL ID final rules as published<br />
January 10, 2008.<br />
C. Card designs must include features from each of the three levels of recognized security features.<br />
The quality and placement of the security features is more important than the number of security<br />
features.<br />
The external surfaces of the card must be printed using recognized industry accepted security<br />
printing methods to resist duplication or facsimile reproduction by commercially available<br />
products.<br />
Page 32 of 115