Syngress - Eleventh Hour Network+ Exam N10-004 Study Guide (11 ...
Syngress - Eleventh Hour Network+ Exam N10-004 Study Guide (11 ...
Syngress - Eleventh Hour Network+ Exam N10-004 Study Guide (11 ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
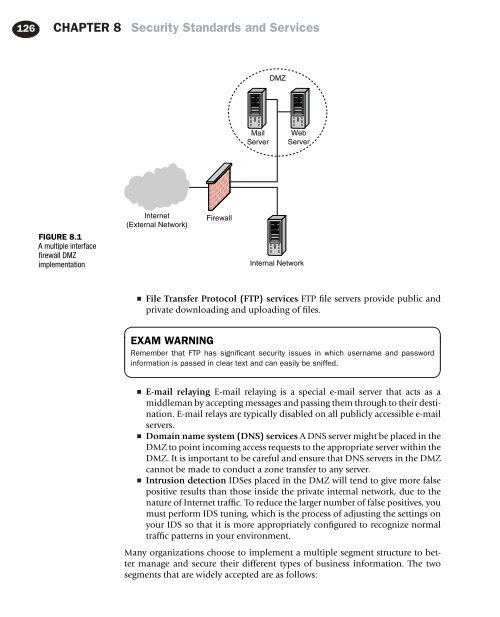
126 CHAPTER 8 Security Standards and Services<br />
DMZ<br />
Mail<br />
Server<br />
Web<br />
Server<br />
FIGURE 8.1<br />
A multiple interface<br />
firewall DMZ<br />
implementation<br />
Internet<br />
(External Network)<br />
Firewall<br />
Internal Network<br />
■<br />
File Transfer Protocol (FTP) services FTP file servers provide public and<br />
private downloading and uploading of files.<br />
EXAM WARNING<br />
Remember that FTP has significant security issues in which username and password<br />
information is passed in clear text and can easily be sniffed.<br />
■<br />
■<br />
■<br />
E-mail relaying E-mail relaying is a special e-mail server that acts as a<br />
middleman by accepting messages and passing them through to their destination.<br />
E-mail relays are typically disabled on all publicly accessible e-mail<br />
servers.<br />
Domain name system (DNS) services A DNS server might be placed in the<br />
DMZ to point incoming access requests to the appropriate server within the<br />
DMZ. It is important to be careful and ensure that DNS servers in the DMZ<br />
cannot be made to conduct a zone transfer to any server.<br />
Intrusion detection IDSes placed in the DMZ will tend to give more false<br />
positive results than those inside the private internal network, due to the<br />
nature of Internet traffic. To reduce the larger number of false positives, you<br />
must perform IDS tuning, which is the process of adjusting the settings on<br />
your IDS so that it is more appropriately configured to recognize normal<br />
traffic patterns in your environment.<br />
Many organizations choose to implement a multiple segment structure to better<br />
manage and secure their different types of business information. The two<br />
segments that are widely accepted are as follows: