Syngress - Eleventh Hour Network+ Exam N10-004 Study Guide (11 ...
Syngress - Eleventh Hour Network+ Exam N10-004 Study Guide (11 ...
Syngress - Eleventh Hour Network+ Exam N10-004 Study Guide (11 ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Network Ports, Services, and Threats 129<br />
Datalink<br />
Header<br />
IP Header<br />
IPsec<br />
ESP<br />
Header<br />
UDP<br />
Header<br />
L2TP<br />
Header<br />
PPP<br />
Header<br />
Encrypted portion<br />
PPP Payload<br />
(IP<br />
datagram)<br />
IPsec<br />
ESP<br />
Trailer<br />
IPsec<br />
ESP Auth<br />
Trailer<br />
Datalink<br />
Trailer<br />
Authenticated portion<br />
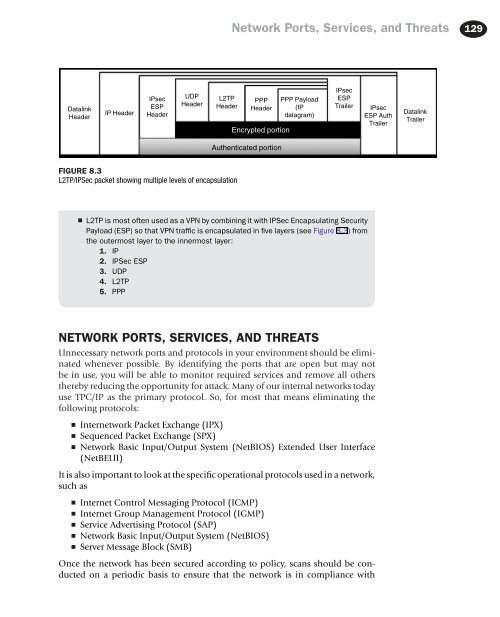
FIGURE 8.3<br />
L2TP/IPSec packet showing multiple levels of encapsulation<br />
■ L2TP is most often used as a VPN by combining it with IPSec Encapsulating Security<br />
Payload (ESP) so that VPN traffic is encapsulated in five layers (see Figure 8.3) from<br />
the outermost layer to the innermost layer:<br />
1. IP<br />
2. IPSec ESP<br />
3. UDP<br />
4. L2TP<br />
5. PPP<br />
NETWORK PORTS, SERVICES, AND THREATS<br />
Unnecessary network ports and protocols in your environment should be eliminated<br />
whenever possible. By identifying the ports that are open but may not<br />
be in use, you will be able to monitor required services and remove all others<br />
thereby reducing the opportunity for attack. Many of our internal networks today<br />
use TPC/IP as the primary protocol. So, for most that means eliminating the<br />
following protocols:<br />
■ Internetwork Packet Exchange (IPX)<br />
■ Sequenced Packet Exchange (SPX)<br />
■ Network Basic Input/Output System (NetBIOS) Extended User Interface<br />
(NetBEUI)<br />
It is also important to look at the specific operational protocols used in a network,<br />
such as<br />
■<br />
■<br />
■<br />
■<br />
■<br />
Internet Control Messaging Protocol (ICMP)<br />
Internet Group Management Protocol (IGMP)<br />
Service Advertising Protocol (SAP)<br />
Network Basic Input/Output System (NetBIOS)<br />
Server Message Block (SMB)<br />
Once the network has been secured according to policy, scans should be conducted<br />
on a periodic basis to ensure that the network is in compliance with