1 Montgomery Modular Multiplication in Hard- ware
1 Montgomery Modular Multiplication in Hard- ware
1 Montgomery Modular Multiplication in Hard- ware
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
FEI KEMT<br />
Y , with �y0 = 0 and X is concatenated with two zero bits at MSB positions. This<br />
change simplifies the computation of qi compared to Algorithm 1 – 3. The value of<br />
qi needed for computation of Si+1 is given directly as a LSB of Si from the previous<br />
iteration (see step 4 of the Algorithm 1 – 4). In this way the latency caused by an<br />
addition of operands xiY is removed and logic implementation can be simplified,<br />
too.<br />
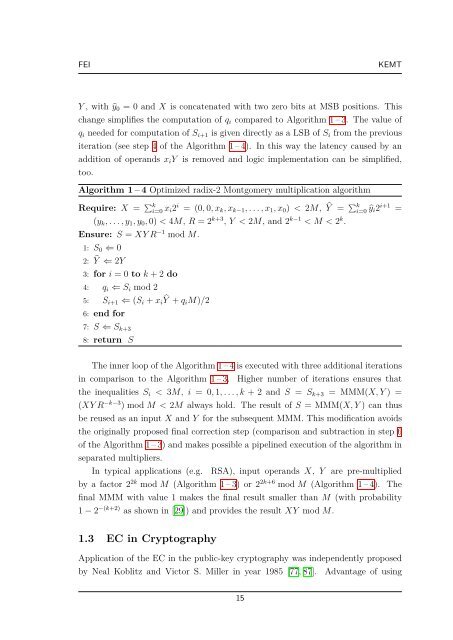
Algorithm 1 – 4 Optimized radix-2 <strong>Montgomery</strong> multiplication algorithm<br />
Require: X = � k i=0 xi2 i = (0, 0, xk, xk−1, . . . , x1, x0) < 2M, � Y = � k i=0 �yi2 i+1 =<br />
(yk, . . . , y1, y0, 0) < 4M, R = 2 k+3 , Y < 2M, and 2 k−1 < M < 2 k .<br />
Ensure: S = XY R −1 mod M.<br />
1: S0 ⇐ 0<br />
2: � Y ⇐ 2Y<br />
3: for i = 0 to k + 2 do<br />
4: qi ⇐ Si mod 2<br />
5: Si+1 ⇐ (Si + xi � Y + qiM)/2<br />
6: end for<br />
7: S ⇐ Sk+3<br />
8: return S<br />
The <strong>in</strong>ner loop of the Algorithm 1 – 4 is executed with three additional iterations<br />
<strong>in</strong> comparison to the Algorithm 1 – 3. Higher number of iterations ensures that<br />
the <strong>in</strong>equalities Si < 3M, i = 0, 1, . . . , k + 2 and S = Sk+3 = MMM(X, Y ) =<br />
(XY R −k−3 ) mod M < 2M always hold. The result of S = MMM(X, Y ) can thus<br />
be reused as an <strong>in</strong>put X and Y for the subsequent MMM. This modification avoids<br />
the orig<strong>in</strong>ally proposed f<strong>in</strong>al correction step (comparison and subtraction <strong>in</strong> step 6<br />
of the Algorithm 1 – 3) and makes possible a pipel<strong>in</strong>ed execution of the algorithm <strong>in</strong><br />
separated multipliers.<br />
In typical applications (e.g. RSA), <strong>in</strong>put operands X, Y are pre-multiplied<br />
by a factor 2 2k mod M (Algorithm 1 – 3) or 2 2k+6 mod M (Algorithm 1 – 4). The<br />
f<strong>in</strong>al MMM with value 1 makes the f<strong>in</strong>al result smaller than M (with probability<br />
1 − 2 −(k+2) as shown <strong>in</strong> [29]) and provides the result XY mod M.<br />
1.3 EC <strong>in</strong> Cryptography<br />
Application of the EC <strong>in</strong> the public-key cryptography was <strong>in</strong>dependently proposed<br />
by Neal Koblitz and Victor S. Miller <strong>in</strong> year 1985 [77, 87]. Advantage of us<strong>in</strong>g<br />
15