Intrusion Defense Firewall 1.2 User's Guide - Trend Micro? Online ...
Intrusion Defense Firewall 1.2 User's Guide - Trend Micro? Online ...
Intrusion Defense Firewall 1.2 User's Guide - Trend Micro? Online ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
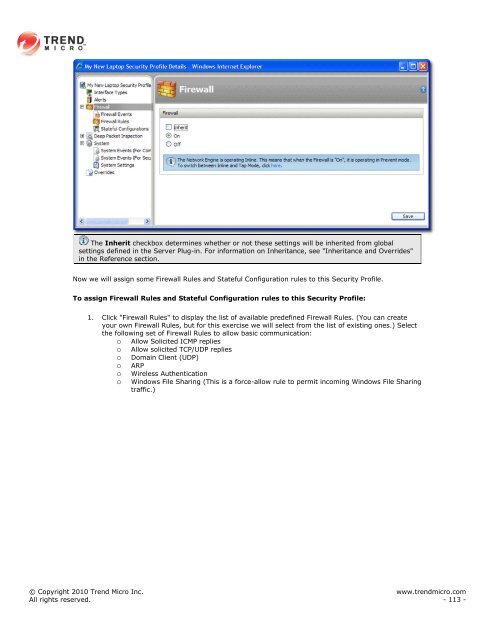
The Inherit checkbox determines whether or not these settings will be inherited from global<br />
settings defined in the Server Plug-in. For information on Inheritance, see "Inheritance and Overrides"<br />
in the Reference section.<br />
Now we will assign some <strong>Firewall</strong> Rules and Stateful Configuration rules to this Security Profile.<br />
To assign <strong>Firewall</strong> Rules and Stateful Configuration rules to this Security Profile:<br />
1. Click "<strong>Firewall</strong> Rules" to display the list of available predefined <strong>Firewall</strong> Rules. (You can create<br />
your own <strong>Firewall</strong> Rules, but for this exercise we will select from the list of existing ones.) Select<br />
the following set of <strong>Firewall</strong> Rules to allow basic communication:<br />
o Allow Solicited ICMP replies<br />
o Allow solicited TCP/UDP replies<br />
o Domain Client (UDP)<br />
o ARP<br />
o Wireless Authentication<br />
o Windows File Sharing (This is a force-allow rule to permit incoming Windows File Sharing<br />
traffic.)<br />
© Copyright 2010 <strong>Trend</strong> <strong>Micro</strong> Inc. www.trendmicro.com<br />
All rights reserved. - 113 -