Intrusion Defense Firewall 1.2 User's Guide - Trend Micro? Online ...
Intrusion Defense Firewall 1.2 User's Guide - Trend Micro? Online ...
Intrusion Defense Firewall 1.2 User's Guide - Trend Micro? Online ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
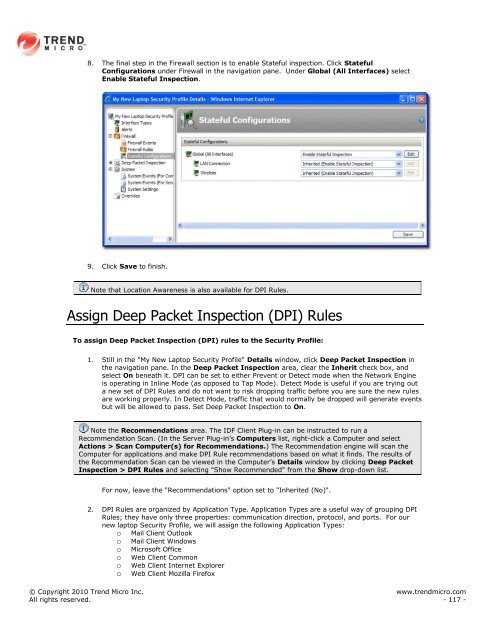
8. The final step in the <strong>Firewall</strong> section is to enable Stateful inspection. Click Stateful<br />
Configurations under <strong>Firewall</strong> in the navigation pane. Under Global (All Interfaces) select<br />
Enable Stateful Inspection.<br />
9. Click Save to finish.<br />
Note that Location Awareness is also available for DPI Rules.<br />
Assign Deep Packet Inspection (DPI) Rules<br />
To assign Deep Packet Inspection (DPI) rules to the Security Profile:<br />
1. Still in the "My New Laptop Security Profile" Details window, click Deep Packet Inspection in<br />
the navigation pane. In the Deep Packet Inspection area, clear the Inherit check box, and<br />
select On beneath it. DPI can be set to either Prevent or Detect mode when the Network Engine<br />
is operating in Inline Mode (as opposed to Tap Mode). Detect Mode is useful if you are trying out<br />
a new set of DPI Rules and do not want to risk dropping traffic before you are sure the new rules<br />
are working properly. In Detect Mode, traffic that would normally be dropped will generate events<br />
but will be allowed to pass. Set Deep Packet Inspection to On.<br />
Note the Recommendations area. The IDF Client Plug-in can be instructed to run a<br />
Recommendation Scan. (In the Server Plug-in‟s Computers list, right-click a Computer and select<br />
Actions > Scan Computer(s) for Recommendations.) The Recommendation engine will scan the<br />
Computer for applications and make DPI Rule recommendations based on what it finds. The results of<br />
the Recommendation Scan can be viewed in the Computer‟s Details window by clicking Deep Packet<br />
Inspection > DPI Rules and selecting "Show Recommended" from the Show drop-down list.<br />
For now, leave the "Recommendations" option set to "Inherited (No)".<br />
2. DPI Rules are organized by Application Type. Application Types are a useful way of grouping DPI<br />
Rules; they have only three properties: communication direction, protocol, and ports. For our<br />
new laptop Security Profile, we will assign the following Application Types:<br />
o Mail Client Outlook<br />
o Mail Client Windows<br />
o <strong>Micro</strong>soft Office<br />
o Web Client Common<br />
o Web Client Internet Explorer<br />
o Web Client Mozilla Firefox<br />
© Copyright 2010 <strong>Trend</strong> <strong>Micro</strong> Inc. www.trendmicro.com<br />
All rights reserved. - 117 -