Prospective crime mapping in operational context Final report
Prospective crime mapping in operational context Final report
Prospective crime mapping in operational context Final report
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
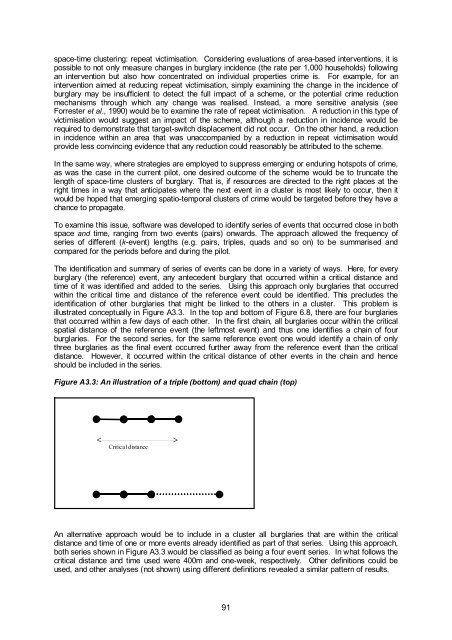
space-time cluster<strong>in</strong>g: repeat victimisation. Consider<strong>in</strong>g evaluations of area-based <strong>in</strong>terventions, it ispossible to not only measure changes <strong>in</strong> burglary <strong>in</strong>cidence (the rate per 1,000 households) follow<strong>in</strong>gan <strong>in</strong>tervention but also how concentrated on <strong>in</strong>dividual properties <strong>crime</strong> is. For example, for an<strong>in</strong>tervention aimed at reduc<strong>in</strong>g repeat victimisation, simply exam<strong>in</strong><strong>in</strong>g the change <strong>in</strong> the <strong>in</strong>cidence ofburglary may be <strong>in</strong>sufficient to detect the full impact of a scheme, or the potential <strong>crime</strong> reductionmechanisms through which any change was realised. Instead, a more sensitive analysis (seeForrester et al., 1990) would be to exam<strong>in</strong>e the rate of repeat victimisation. A reduction <strong>in</strong> this type ofvictimisation would suggest an impact of the scheme, although a reduction <strong>in</strong> <strong>in</strong>cidence would berequired to demonstrate that target-switch displacement did not occur. On the other hand, a reduction<strong>in</strong> <strong>in</strong>cidence with<strong>in</strong> an area that was unaccompanied by a reduction <strong>in</strong> repeat victimisation wouldprovide less conv<strong>in</strong>c<strong>in</strong>g evidence that any reduction could reasonably be attributed to the scheme.In the same way, where strategies are employed to suppress emerg<strong>in</strong>g or endur<strong>in</strong>g hotspots of <strong>crime</strong>,as was the case <strong>in</strong> the current pilot, one desired outcome of the scheme would be to truncate thelength of space-time clusters of burglary. That is, if resources are directed to the right places at theright times <strong>in</strong> a way that anticipates where the next event <strong>in</strong> a cluster is most likely to occur, then itwould be hoped that emerg<strong>in</strong>g spatio-temporal clusters of <strong>crime</strong> would be targeted before they have achance to propagate.To exam<strong>in</strong>e this issue, software was developed to identify series of events that occurred close <strong>in</strong> bothspace and time, rang<strong>in</strong>g from two events (pairs) onwards. The approach allowed the frequency ofseries of different (k-event) lengths (e.g. pairs, triples, quads and so on) to be summarised andcompared for the periods before and dur<strong>in</strong>g the pilot.The identification and summary of series of events can be done <strong>in</strong> a variety of ways. Here, for everyburglary (the reference) event, any antecedent burglary that occurred with<strong>in</strong> a critical distance andtime of it was identified and added to the series. Us<strong>in</strong>g this approach only burglaries that occurredwith<strong>in</strong> the critical time and distance of the reference event could be identified. This precludes theidentification of other burglaries that might be l<strong>in</strong>ked to the others <strong>in</strong> a cluster. This problem isillustrated conceptually <strong>in</strong> Figure A3.3. In the top and bottom of Figure 6.8, there are four burglariesthat occurred with<strong>in</strong> a few days of each other. In the first cha<strong>in</strong>, all burglaries occur with<strong>in</strong> the criticalspatial distance of the reference event (the leftmost event) and thus one identifies a cha<strong>in</strong> of fourburglaries. For the second series, for the same reference event one would identify a cha<strong>in</strong> of onlythree burglaries as the f<strong>in</strong>al event occurred further away from the reference event than the criticaldistance. However, it occurred with<strong>in</strong> the critical distance of other events <strong>in</strong> the cha<strong>in</strong> and henceshould be <strong>in</strong>cluded <strong>in</strong> the series.Figure A3.3: An illustration of a triple (bottom) and quad cha<strong>in</strong> (top)Critical distanceAn alternative approach would be to <strong>in</strong>clude <strong>in</strong> a cluster all burglaries that are with<strong>in</strong> the criticaldistance and time of one or more events already identified as part of that series. Us<strong>in</strong>g this approach,both series shown <strong>in</strong> Figure A3.3 would be classified as be<strong>in</strong>g a four event series. In what follows thecritical distance and time used were 400m and one-week, respectively. Other def<strong>in</strong>itions could beused, and other analyses (not shown) us<strong>in</strong>g different def<strong>in</strong>itions revealed a similar pattern of results.91