I527-290 ESRIF Final Report (WEB).indd - European Commission
I527-290 ESRIF Final Report (WEB).indd - European Commission
I527-290 ESRIF Final Report (WEB).indd - European Commission
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
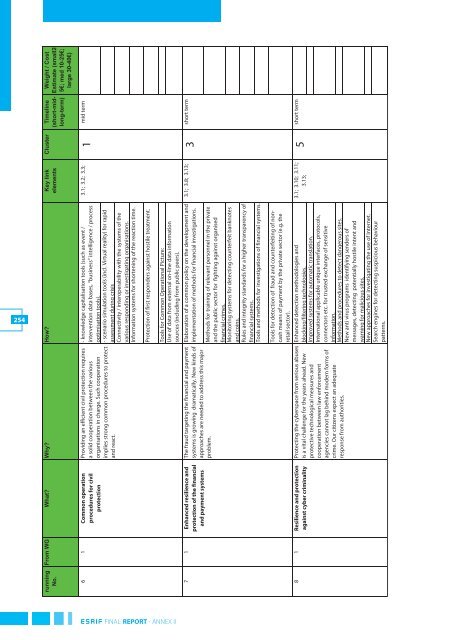
254<br />
Weight / Cost<br />
Estimate (small2-<br />
5€; med 10-25€;<br />
large 30-40€)<br />
Cluster Timeline<br />
(short-midlong-term)<br />
From WG What? Why? How? Key link<br />
elements<br />
running<br />
No.<br />
3.1; 3.2; 3.3; mid term<br />
1<br />
- knowledge capitalisation tools (such as event /<br />
intervention data bases, “business” intelligence / process<br />
optimisation tools).<br />
- scenario simulation tools (incl. Virtual reality) for rapid<br />
assessment during crisis<br />
Connectivity / interoperability with the systems of the<br />
various responding or investigating organisations.<br />
Information systems for shortening of the reaction time.<br />
Providing an efficient civil protection requires<br />
a solid cooperation between the various<br />
organisations in charge. Such cooperation<br />
implies strong common procedures to protect<br />
and react.<br />
6 1 Common operation<br />
procedures for civil<br />
protection<br />
Protection of first responders against hostile treatment.<br />
short term<br />
3.1; 3.8; 3.13;<br />
Tools for Common Operational Picture:<br />
Use of data from external on-line data information<br />
sources (including from public peers).<br />
Elaboration of a common policy on the development and<br />
implementation of methods for financial investigations.<br />
<strong>ESRIF</strong> FINAL REPORT - ANNEX II<br />
3<br />
The fraud targeting the financial and payment<br />
systems is growing dramatically. New kinds of<br />
approaches are needed to address this major<br />
problem.<br />
7 1 Enhanced resilience and<br />
protection of the financial<br />
and payment systems<br />
Methods for training of relevant personnel in the private<br />
and the public sector for fighting against organised<br />
financial crimes.<br />
Monitoring systems for detecting counterfeit banknotes<br />
and coins.<br />
Rules and integrity standards for a higher transparency of<br />
financial systems.<br />
Tools and methods for investigations of financial systems.<br />
short term<br />
5<br />
3.1; 3.10; 3.11;<br />
3.13;<br />
Tools for detection of fraud and counterfeiting of noncash<br />
means of payment by the private sector (e.g. the<br />
retail sector).<br />
Protecting the cyberspace from serious abuses Enhanced detection methodologies and<br />
is a vital challenge for the years ahead. New blocking/filtering technologies.<br />
protective technological measures and Improved systems for automatic translation.<br />
cooperation between law enforcement International applicable unique interfaces, protocols,<br />
agencies cannot lag behind modern forms of connectors etc. for trusted exchange of sensitive<br />
crime. Our citizens expect an adequate information.<br />
response from authorities.<br />
Methods and procedures to detect dangerous sites.<br />
New anti virus programs identifying senders of<br />
messages, detecting potentially hostile intent and<br />
warning for malicious sites.<br />
New approaches for investigating the use of Internet.<br />
Search engines for detecting suspicious behaviour<br />
patterns.<br />
8 1 Resilience and protection<br />
against cyber criminality