Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
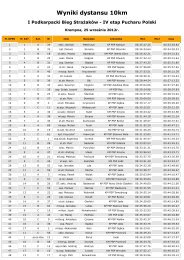
CHAPTER III: INFORMATION AND COMMUNICATION TECHNOLOGY<br />
operations or to only a few hours dur<strong>in</strong>g some days of the week. A typical<br />
illustration of access accorded to different groups is depicted <strong>in</strong> Figure 6.<br />
Figure III—6 Example of type of authorized access accorded to different groups.<br />
I. Deliberate Threat Actors<br />
The threat actors with deliberate <strong>in</strong>tent have <strong>in</strong> great part put <strong>in</strong>to focus the need<br />
for CIIP. These actors are pro<strong>fi</strong>led briefly <strong>in</strong> Table 3. The threat posed by hackers<br />
has long been recognized with<strong>in</strong> the IT security community, with anti-hack<strong>in</strong>g<br />
security measures be<strong>in</strong>g the norm and legal procedures regularly <strong>in</strong>stituted aga<strong>in</strong>st<br />
those responsible. Cont<strong>in</strong>ued <strong>in</strong>creases <strong>in</strong> electronic/mobile-commerce activities 53<br />
create added <strong>in</strong>centive for crim<strong>in</strong>al activity (cyber-crime) 54 and fuell<strong>in</strong>g unfair<br />
practices between rival companies via the <strong>in</strong>formation <strong>in</strong>frastructure. 55 Hostile<br />
governments are also recogniz<strong>in</strong>g the <strong>in</strong>creased potential of underm<strong>in</strong><strong>in</strong>g<br />
adversaries by launch<strong>in</strong>g attacks that disable their CII (Overill 2001).<br />
Of the threat actors mentioned <strong>in</strong> Table 3, the threat posed by terrorists is<br />
currently the most widely publicized. Thus far, terrorist attacks have targeted more<br />
visible or tangible critical <strong>in</strong>frastructure, such as railways, airports, water<br />
53 For example: eMarketer (eMarketer 2007) predicts electronic commerce retail sales <strong>in</strong> Europe<br />
will reach USD 400 billion by 2011; F<strong>in</strong>extra (F<strong>in</strong>extra 2007) predicts global mobile commerce<br />
market (exclud<strong>in</strong>g mobile enterta<strong>in</strong>ment) to grow to USD 40 billion by 2009.<br />
54 Cyber-crime refers to traditional crime activities facilitated by the use of ICTs. The proliferation<br />
of cyber-crime has prompted the Council of Europe to draw up a “Convention on Cybercrime<br />
(CETS No.: 185),” a <strong>fi</strong>rst <strong>in</strong>ternational treaty (with 43 signatories) on crimes committed via the<br />
Internet and other computer networks.<br />
55 For example, a Massachusetts bus<strong>in</strong>essman is known to have authorized crippl<strong>in</strong>g DDoS attacks<br />
aga<strong>in</strong>st three compet<strong>in</strong>g companies (Poulsen 2004).<br />
NORDREGIO REPORT 2007:5 93