Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
CRITICAL INFRASTRUCTURE PROTECTION IN THE BALTIC SEA REGION<br />
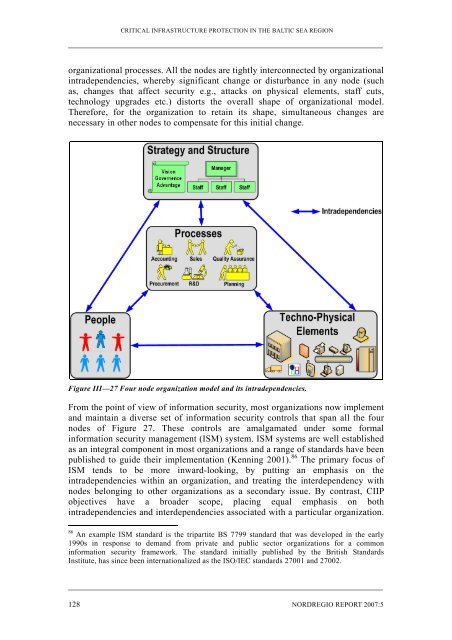
organizational processes. All the nodes are tightly <strong>in</strong>terconnected by organizational<br />
<strong>in</strong>tradependencies, whereby signi<strong>fi</strong>cant change or disturbance <strong>in</strong> any node (such<br />
as, changes that affect security e.g., attacks on physical elements, staff cuts,<br />
technology upgrades etc.) distorts the overall shape of organizational model.<br />
Therefore, for the organization to reta<strong>in</strong> its shape, simultaneous changes are<br />
necessary <strong>in</strong> other nodes to compensate for this <strong>in</strong>itial change.<br />
Figure III—27 Four node organization model and its <strong>in</strong>tradependencies.<br />
From the po<strong>in</strong>t of view of <strong>in</strong>formation security, most organizations now implement<br />
and ma<strong>in</strong>ta<strong>in</strong> a diverse set of <strong>in</strong>formation security controls that span all the four<br />
nodes of Figure 27. These controls are amalgamated under some formal<br />
<strong>in</strong>formation security management (ISM) system. ISM systems are well established<br />
as an <strong>in</strong>tegral component <strong>in</strong> most organizations and a range of standards have been<br />
published to guide their implementation (Kenn<strong>in</strong>g 2001). 86 The primary focus of<br />
ISM tends to be more <strong>in</strong>ward-look<strong>in</strong>g, by putt<strong>in</strong>g an emphasis on the<br />
<strong>in</strong>tradependencies with<strong>in</strong> an organization, and treat<strong>in</strong>g the <strong>in</strong>terdependency with<br />
nodes belong<strong>in</strong>g to other organizations as a secondary issue. By contrast, CIIP<br />
objectives have a broader scope, plac<strong>in</strong>g equal emphasis on both<br />
<strong>in</strong>tradependencies and <strong>in</strong>terdependencies associated with a particular organization.<br />
86 An example ISM standard is the tripartite BS 7799 standard that was developed <strong>in</strong> the early<br />
1990s <strong>in</strong> response to demand from private and public sector organizations for a common<br />
<strong>in</strong>formation security framework. The standard <strong>in</strong>itially published by the British Standards<br />
Institute, has s<strong>in</strong>ce been <strong>in</strong>ternationalized as the ISO/IEC standards 27001 and 27002.<br />
128 NORDREGIO REPORT 2007:5