Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
CHAPTER III: INFORMATION AND COMMUNICATION TECHNOLOGY<br />
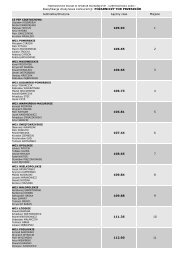
Table III—12 TETRA network security measures addressed <strong>in</strong> Modules 7-9 of the ITU-T X.805<br />
security architecture.<br />
Module<br />
Module 7:<br />
Application layer,<br />
management plane<br />
Module 8:<br />
Application layer,<br />
control plane<br />
Module 9:<br />
Application layer,<br />
end-user plane<br />
Security Measures<br />
• Rights to adm<strong>in</strong>ister and manage applications restricted to<br />
authorized personnel, application providers and term<strong>in</strong>als.<br />
• Protect <strong>fi</strong>les used <strong>in</strong> the execution and creation of applications<br />
(e.g., executable <strong>fi</strong>les).<br />
• Protect identity of users, user groups and term<strong>in</strong>als (e.g., TEI,<br />
ITSI, GTSI etc.) utiliz<strong>in</strong>g an application.<br />
• Ma<strong>in</strong>ta<strong>in</strong> a database of applications accessed and utilized by<br />
users, user groups and term<strong>in</strong>als.<br />
• Encryption of application control <strong>in</strong>formation transported with<strong>in</strong><br />
the network.<br />
• Ensure application control <strong>in</strong>formation orig<strong>in</strong>ates from<br />
authorized source.<br />
• Protect identity of users, user groups and term<strong>in</strong>als (e.g., TEI,<br />
ITSI, GTSI etc.) utiliz<strong>in</strong>g an application.<br />
• Encryption of user traf<strong>fi</strong>c (e.g., patient’s ECG trace) be<strong>in</strong>g<br />
transported over the air <strong>in</strong>terface and/or end-to-end.<br />
• Protection of application <strong>fi</strong>les/data us<strong>in</strong>g conventional methods<br />
(e.g., email and attachments us<strong>in</strong>g PGP, S/MIME etc.).<br />
• Restrict access and use of applications (e.g. us<strong>in</strong>g passwords) to<br />
authorized users, user groups and term<strong>in</strong>als.<br />
Example TETRA traf<strong>fi</strong>c analysis<br />
One of the key measures <strong>in</strong> ensur<strong>in</strong>g service availability for critical missions <strong>in</strong><br />
TETRA networks is to consider some of the likely scenarios right from the<br />
plann<strong>in</strong>g stage. As an example, we present some simpli<strong>fi</strong>ed traf<strong>fi</strong>c analysis that<br />
could enable networks planners to make key decisions on how to manage limited<br />
resources (channels) under various operat<strong>in</strong>g conditions.<br />
The call setup time (or delay) is one of the important TETRA performance<br />
parameters, particularly <strong>in</strong> moments dur<strong>in</strong>g or immediately after a crisis, where the<br />
requirement for split-second decisions and responses is high (Rantanen 2003). In<br />
cases of extreme load because of many simultaneous callers the call setup time<br />
tends to <strong>in</strong>crease because of the higher contention for resources. At that po<strong>in</strong>t<br />
dispatchers will start prioritiz<strong>in</strong>g calls by queu<strong>in</strong>g, block<strong>in</strong>g or dropp<strong>in</strong>g low<br />
priority calls and giv<strong>in</strong>g preference to high priority calls.<br />
Consider a service area that has the follow<strong>in</strong>g TETRA user groups:<br />
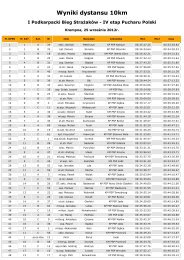
• Police: twenty traf<strong>fi</strong>c police of<strong>fi</strong>cers work<strong>in</strong>g <strong>in</strong> pairs and <strong>fi</strong>ve groups of<br />
security police each with of <strong>fi</strong>ve members.<br />
• Fire Brigade: four units each consist<strong>in</strong>g of <strong>fi</strong>ve <strong>fi</strong>re <strong>fi</strong>ghters.<br />
• Ambulance: six ambulance units of each with a crew of three (1 driver<br />
and 2 paramedics).<br />
NORDREGIO REPORT 2007:5 121