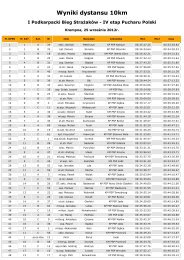
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
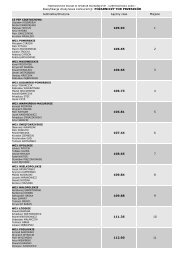
CHAPTER III: INFORMATION AND COMMUNICATION TECHNOLOGY<br />
harmful or undesired purpose (Shirey 2000). This is further illustrated <strong>in</strong> the<br />
concept of map Figure 7.<br />
Figure III—7 Concept mapp<strong>in</strong>g of malicious logic <strong>in</strong> <strong>in</strong>formation and communication systems.<br />
Malicious software or malware has long presented a signi<strong>fi</strong>cant security threat that<br />
has become more pronounced with the ubiquitous connectivity enabled by the<br />
Internet. 59 As an <strong>in</strong>dication of exist<strong>in</strong>g threats, <strong>in</strong> a recent ‘honey pot’ experiment a<br />
computer runn<strong>in</strong>g W<strong>in</strong>dows XP (Service Pack 1) with no anti-software software<br />
was connected to the Internet and ended be<strong>in</strong>g successfully <strong>in</strong>fected by worms<br />
with<strong>in</strong> 18 m<strong>in</strong>utes, and <strong>in</strong> one week was scanned over 46,000 times by remote<br />
computers look<strong>in</strong>g for vulnerabilities (Wehner 2006). Attacks on CII us<strong>in</strong>g<br />
malicious logic is quickly becom<strong>in</strong>g the preferred modus operandi for various<br />
deliberate threat actors, s<strong>in</strong>ce such an attack has a very low cost of entry, is<br />
effective <strong>in</strong> the disruption it causes, and carries a low risk of be<strong>in</strong>g apprehended.<br />
The proliferation of undesired data (spam) <strong>in</strong> <strong>in</strong>formation and communication<br />
systems also constitutes a threat, <strong>in</strong> the way that the delivery, <strong>fi</strong>lter<strong>in</strong>g and<br />
subsequent deletion of this unsolicited data consumes valuable bandwidth, storage<br />
and human resources. Some security analysts now believe that the volume of e-<br />
mail spam is <strong>in</strong>creas<strong>in</strong>g at levels that are threaten<strong>in</strong>g the viability of global e-<br />
mail<strong>in</strong>g system (Gillis 2007) 60 .<br />
59 For example, the <strong>in</strong>famous ILOVEYOU worm managed to <strong>in</strong>fect 10% of all computers<br />
connected to the Internet <strong>in</strong> just one day of May 2000, lead<strong>in</strong>g to damages <strong>in</strong> the range of €4 to €7<br />
billion.<br />
60 A study by Gillis (2007) estimates that e-mail spam volume doubled <strong>in</strong> the period between<br />
October 2005 - October 2006, vastly outnumber<strong>in</strong>g legitimate e-mail messages. <strong>Critical</strong>ly a third<br />
NORDREGIO REPORT 2007:5 97