Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
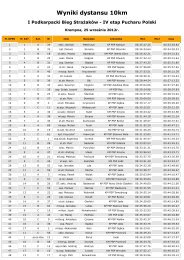
CHAPTER III: INFORMATION AND COMMUNICATION TECHNOLOGY<br />
The Security and Fraud Prevention Group (SFPG) of the TETRA MoU Association<br />
is tasked with updat<strong>in</strong>g the TETRA authentication algorithms (TAA) and TETRA<br />
encryption algorithms (TEA) def<strong>in</strong>ed for TETRA standards. 75 TETRA networks<br />
usually implement air <strong>in</strong>terface encryption (AIE) between MS and SwMI (see<br />
Figure 19). The AIE keys may be derived dynamically for every authentication<br />
procedure, sent to <strong>in</strong>dividual MSs or CUGs us<strong>in</strong>g Over The Air Re-key<strong>in</strong>g<br />
(OTAR), or preloaded (static) <strong>in</strong> the term<strong>in</strong>al or subscriber identity module (SIM).<br />
Furthermore, end-to-end encryption (E2EE) may be used to provide encryption<br />
with<strong>in</strong> the SwMI for more robust security (see Figure 19), for <strong>in</strong>stance, over thirdparty<br />
leased copper l<strong>in</strong>es used on a BS-to-MSC l<strong>in</strong>k. The key management for<br />
E2EE is provided by Over The Air Key<strong>in</strong>g (OTAK) mechanisms.<br />
Figure III—19 Implementation regions for air <strong>in</strong>terface and end-to-end encryption schemes.<br />
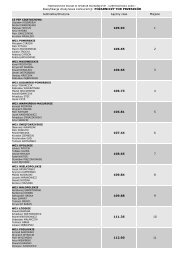
The TETRA standard def<strong>in</strong>es three security classes depend<strong>in</strong>g on the usage of<br />
authentication, encryption and OTAR key management (see Table 9). An MS may<br />
support one, two or all security classes. Mission-critical PSS TETRA networks<br />
such as VIRVE would normally employ the most robust (Class 3) security level.<br />
Table III—9 Security classes def<strong>in</strong>ed by the TETRA standards.<br />
Security<br />
Class<br />
Authentication Encryption OTAR<br />
Class 1 Optional E2EE (optional); AIE (none) None<br />
Class 2<br />
Optional<br />
E2EE (optional); AIE us<strong>in</strong>g static key<br />
encryption (mandatory)<br />
Optional<br />
Class 3<br />
Mandatory<br />
E2EE (optional); AIE us<strong>in</strong>g dynamic key<br />
encryption (mandatory)<br />
Mandatory<br />
The MS provides users with access to the TETRA network. Therefore, the<br />
possibility of threat actors obta<strong>in</strong><strong>in</strong>g unauthorized access via stolen or lost<br />
75 Some of the TEAs used by European agencies face strict export control for usage <strong>in</strong> countries<br />
outside the Wassenaar Arrangement (2007).<br />
NORDREGIO REPORT 2007:5 115