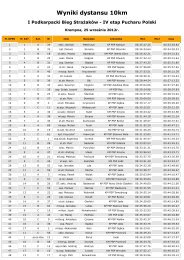
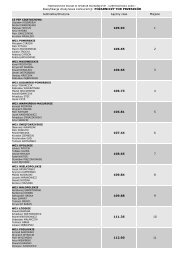
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
CHAPTER III: INFORMATION AND COMMUNICATION TECHNOLOGY<br />
and op<strong>in</strong>ions <strong>in</strong>dicate that the economic dimension may present extremely<br />
formidable but surmountable challenges that require truly committed and decisive<br />
strategic actions.<br />
Social dimension<br />
The relative <strong>in</strong>fluence of the social dimension on the functional state of<br />
<strong>in</strong>formation <strong>in</strong>frastructures is arguably more pronounced compared to other<br />
<strong>in</strong>frastructure types. For <strong>in</strong>stance, <strong>in</strong> utility <strong>in</strong>frastructure the commodity (e.g.,<br />
electricity, water, gas etc.) is mostly delivered on a one-way path from the source<br />
or po<strong>in</strong>t of generation to the end users, thus limit<strong>in</strong>g the way <strong>in</strong> which the end user<br />
could<strong>in</strong>fluence the functional state the <strong>in</strong>frastructure. By comparison, the<br />
<strong>in</strong>formation <strong>in</strong>frastructure affords end users bidirectional connectivity to both<br />
receive and send the primary commodity (payload or <strong>in</strong>formation), the ability to<br />
<strong>in</strong>teract with <strong>in</strong>frastructure elements anywhere around the globe, and the<br />
<strong>in</strong>creas<strong>in</strong>g capability to customize their own services, pro<strong>fi</strong>les and so forth. Signs<br />
abound of <strong>in</strong>creased con<strong>fi</strong>dence with<strong>in</strong> these empowered users, from the<br />
proliferation of feature-rich Smartphones to the thriv<strong>in</strong>g Web 2.0 hosted<br />
applications and communities. 94<br />
However, the mass adoption of ICT devices provides an <strong>in</strong>creas<strong>in</strong>g security<br />
challenge, as each user term<strong>in</strong>al not only presents a sitt<strong>in</strong>g target for threat actors<br />
but may also serve as a launch<strong>in</strong>g po<strong>in</strong>t for attacks on the networks to which they<br />
are connected. For <strong>in</strong>stance, personal computers connected to the Internet could<br />
have their comput<strong>in</strong>g power harnessed to perform some useful computationally<br />
<strong>in</strong>tensive calculations (e.g., for the design of life-sav<strong>in</strong>g drugs) (Buyya et al 2003).<br />
Unfortunately, cyber crim<strong>in</strong>als may use similar pr<strong>in</strong>ciples to form a ‘botnet’<br />
comprised of thousands of compromised computers or zombies that launch e-mail<br />
spam, malware, identity theft attempts and many other nefarious schemes (Goth<br />
2007) 95 . To that end, <strong>in</strong>dividual users should also be considered as one of the key<br />
security factors when address<strong>in</strong>g overall CIIP strategy. As some IT security experts<br />
note, humans tend to be the weakest l<strong>in</strong>k <strong>in</strong> the security cha<strong>in</strong> (Granger 2006).<br />
This calls for an <strong>in</strong>tensi<strong>fi</strong>cation of strategic actions by relevant actors <strong>in</strong> both the<br />
public and private sectors that speci<strong>fi</strong>cally target <strong>in</strong>dividual users of ICTs. These<br />
actions may <strong>in</strong>clude:<br />
• Increas<strong>in</strong>g Security Awareness: Threat actors are always look<strong>in</strong>g to<br />
capitalize on user ignorance, negligence and susceptibility to social<br />
eng<strong>in</strong>eer<strong>in</strong>g attempts. Awareness of the risks <strong>in</strong>volved <strong>in</strong> rout<strong>in</strong>e actions,<br />
such as: surf<strong>in</strong>g the World Wide Web with a browser’s security level set<br />
to ‘Low’; open<strong>in</strong>g emails received from unknown sources; or leav<strong>in</strong>g a<br />
mobile handset default PIN code of 0000 or 1234 unchanged, is a<br />
signi<strong>fi</strong>cant step <strong>in</strong> counter<strong>in</strong>g security threats. A user who is reasonably<br />
94 The latest (August 2007) <strong>fi</strong>gures from the web monitor<strong>in</strong>g company Alexa <strong>in</strong>dicate that the Web<br />
2.0 websites such as YouTube, MySpace, Baidu, Orkut and Facebook feature prom<strong>in</strong>ently <strong>in</strong> the<br />
list of top 10 most popular sites (ALEXA 2007).<br />
95 Goth (2007) quotes an <strong>in</strong>dustry <strong>in</strong>sider stat<strong>in</strong>g “Now I th<strong>in</strong>k of botnets as grid comput<strong>in</strong>g gone<br />
bad — they have <strong>in</strong>f<strong>in</strong>ite free computer power and free bandwidth. There is no way to stop this<br />
problem if you’re try<strong>in</strong>g to do it yourself. Your costs will scale with the amount of attacks you’re<br />
receiv<strong>in</strong>g.”<br />
NORDREGIO REPORT 2007:5 133