Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
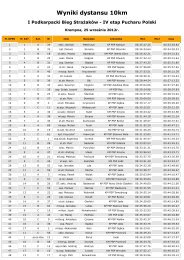
CRITICAL INFRASTRUCTURE PROTECTION IN THE BALTIC SEA REGION<br />
I. Infrastructure security layer constitut<strong>in</strong>g network transmission facilities and<br />
devices that are fundamental build<strong>in</strong>g blocks of the network (e.g., servers,<br />
routers, base stations, l<strong>in</strong>ks between base stations and switch<strong>in</strong>g centre).<br />
II. Services security layer address<strong>in</strong>g security of services provided by the<br />
network (e.g., Internet access services, voice calls, VPN, SDS/SMS<br />
messag<strong>in</strong>g).<br />
III. Applications security layer address<strong>in</strong>g security of network-based<br />
applications accessed by network users (e.g., email, web brows<strong>in</strong>g, <strong>fi</strong>le<br />
transfer, onl<strong>in</strong>e tra<strong>in</strong><strong>in</strong>g, electronic/mobile-commerce).<br />
3. Security planes: are categories of network-related activities protected by<br />
security dimensions. The three activity planes <strong>in</strong> the security architecture are:<br />
I. The management security plane concerned with protection of OAM&P<br />
functions of network elements, services and application. Includes the fault,<br />
capacity, adm<strong>in</strong>istration, provision<strong>in</strong>g, and security (FCAPS) functions.<br />
II. The control security plane concerned with the protection of activities that<br />
enable ef<strong>fi</strong>cient delivery of <strong>in</strong>formation, services and applications across<br />
the networks. Includes mach<strong>in</strong>e-to-mach<strong>in</strong>e communication of control or<br />
signall<strong>in</strong>g <strong>in</strong>formation for con<strong>fi</strong>gur<strong>in</strong>g devices to route traf<strong>fi</strong>c across<br />
network.<br />
III. The end-user security plane addresses security <strong>in</strong> the user’s process of<br />
access<strong>in</strong>g and utiliz<strong>in</strong>g services provided by network. This also <strong>in</strong>cludes<br />
actual end-user payload or data flows (e.g., images, data <strong>fi</strong>les, stream<strong>in</strong>g<br />
video).<br />
Each of the aforementioned security planes along with the three security layers<br />
must be secured to provide an effective end-to-end security posture.<br />
Utilization of the ITU-T X.805 Security Architecture<br />
The ITU-T X.805 security architecture components described previously enable<br />
the identi<strong>fi</strong>cation of security issues that need to be addressed <strong>in</strong> counter<strong>in</strong>g threats<br />
adopted from ITU-T X.800, namely: destruction, corruption, removal, disclosure<br />
and <strong>in</strong>terruption. Table 7 shows the security dimensions and the correspond<strong>in</strong>g<br />
security threats that are addressed by each dimension. For <strong>in</strong>stance, the<br />
authentication security dimension counters the threat of removal or disclosure of<br />
<strong>in</strong>formation.<br />
The ITU-T X.805 security architecture enables modular, systematic and<br />
organized assessment and plann<strong>in</strong>g of network security. Figure 17 illustrates <strong>in</strong><br />
tabulated form how the <strong>in</strong>tersection of three security layers and three security<br />
planes provide n<strong>in</strong>e unique perspectives or modules for consideration of the eight<br />
security dimensions. Notably, the security dimensions of different modules would<br />
have a different set of objectives and hence different set of security measures. This<br />
tabular form provides a convenient way of describ<strong>in</strong>g the security dimension<br />
objectives for each module.<br />
The objective of each one of the aforementioned modules is summarized<br />
briefly <strong>in</strong> Table 8.<br />
112 NORDREGIO REPORT 2007:5