Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Towards a Baltic Sea Region Strategy in Critical ... - Helsinki.fi
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
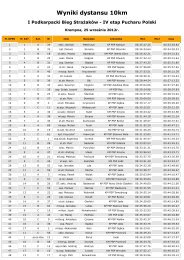
CRITICAL INFRASTRUCTURE PROTECTION IN THE BALTIC SEA REGION<br />
providers. On the other hand, network operators can expect improved operational<br />
flexibility and ef<strong>fi</strong>ciency that <strong>in</strong> turn m<strong>in</strong>imizes operational expenditures, rapid<br />
service launches, <strong>in</strong>creased customer satisfaction and immediate returns on<br />
<strong>in</strong>vestments.<br />
However, the technological advances accompany<strong>in</strong>g these evolutions also<br />
<strong>in</strong>crease the number of ways and <strong>in</strong>stances that an <strong>in</strong>formation <strong>in</strong>frastructure could<br />
be rendered vulnerable. Each one of the added vulnerabilities creates opportunities<br />
for attacks from an <strong>in</strong>f<strong>in</strong>ite number of threats, both known and previously<br />
unknown. For example, the widespread adoption of smartphones and PDAs with<br />
local Bluetooth and Internet connectivity has <strong>in</strong>troduced malwares <strong>in</strong>to the mobile<br />
communications arena, a threat previously synonymous with computer networks<br />
(Hyponnen 2006). 102 The security challenges are considerable as the<br />
<strong>in</strong>terconnectivity and proliferation of devices goes beyond unprecedented levels,<br />
with each device and connection represent<strong>in</strong>g a possible security gap. Awareness<br />
of these security challenges is on the rise and some signi<strong>fi</strong>cant research is already<br />
be<strong>in</strong>g carried out to address them. 103<br />
As CII becomes <strong>in</strong>creas<strong>in</strong>gly complex, failure prevention can never be total.<br />
Therefore, fault tolerance presents arguably the most effective method for<br />
automatic recovery from failures and their potentially highly disruptive outcomes<br />
(Liot<strong>in</strong>e 2003). Fault tolerant systems are typically designed to detect failures<br />
<strong>in</strong>stantly, avoid s<strong>in</strong>gle po<strong>in</strong>t failures, isolate elements with persistent problems and<br />
enable repairs to be carried out even whilst cont<strong>in</strong>u<strong>in</strong>g normal system operations.<br />
It therefore enables network user transactions to cont<strong>in</strong>ue without any noticeable<br />
loss or <strong>in</strong>terruption. These design objectives are met by provid<strong>in</strong>g redundancy,<br />
cont<strong>in</strong>uous status monitor<strong>in</strong>g of network elements and automated recovery<br />
mechanisms. The majority of threat scenarios generated for CIIP studies and<br />
plann<strong>in</strong>g evoke scenes of destroyed or disabled <strong>in</strong>frastructure, thus necessitat<strong>in</strong>g<br />
methods such as fault tolerance to be designed <strong>in</strong>to the <strong>in</strong>frastructure (that is,<br />
critical <strong>in</strong>frastructure protection).<br />
However, the <strong>in</strong>creased decoupl<strong>in</strong>g of services and applications from the<br />
underly<strong>in</strong>g <strong>in</strong>frastructure <strong>in</strong> future networks creates a new <strong>in</strong>ter-<strong>in</strong>frastructure<br />
dimension for fault tolerance design, whereby a service or application could be<br />
cont<strong>in</strong>uously available by migrat<strong>in</strong>g from a damaged <strong>in</strong>frastructure to a work<strong>in</strong>g<br />
one as a way of adapt<strong>in</strong>g to a new user context. An example solution is the<br />
proposed Secured Infrastructure Router (SIR) that has multiple <strong>in</strong>terfaces for<br />
connect<strong>in</strong>g to alternative networks as a form of redundancy aga<strong>in</strong>st failure to any<br />
of the networks (Kari 2007). Such capabilities present a paradigm shift to critical<br />
<strong>in</strong>formation protection with<strong>in</strong> the CIIP concept, as it shifts the emphasis to<br />
availability, con<strong>fi</strong>dentiality and <strong>in</strong>tegrity of user’s <strong>in</strong>formation over a particular<br />
service or application, from traditional <strong>in</strong>frastructure protection. This service or<br />
application level protection mechanisms present signi<strong>fi</strong>cant cost and time<br />
advantages <strong>in</strong> comparison to prevent<strong>in</strong>g attacks by fortify<strong>in</strong>g every node,<br />
102 The number of known mobile malware nonexistent before 2004 has risen sharply to over 200 <strong>in</strong><br />
late 2006. This is small when compared to over 200,000 known computer malware. However, with<br />
the number of mobile devices connected to Internet expected to signi<strong>fi</strong>cantly outstrip the number<br />
of PCs, the threat of mobile malware is likely to be a formidable one.<br />
103 See, for example, Cal<strong>in</strong> et al. (2006).<br />
136 NORDREGIO REPORT 2007:5