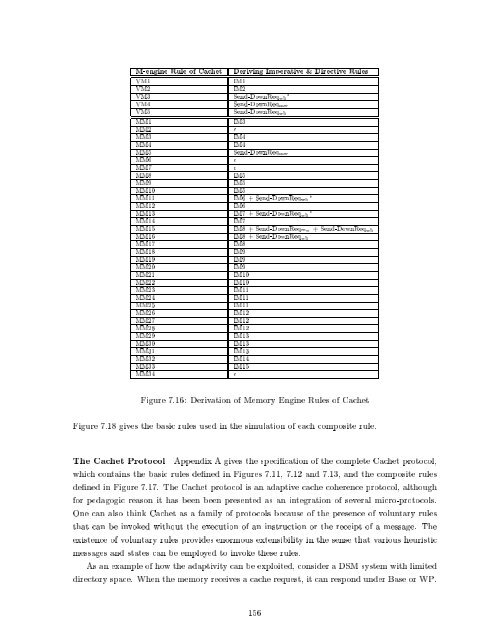
M-engine Rule <strong>of</strong> <strong>Cache</strong>t Deriving Imperative & Directive Rules VM1 IM1 VM2 IM2 VM3 Send-DownReqwb VM4 Send-DownReqmw VM5 Send-DownReqwb MM1 IM3 MM2 MM3 IM4 MM4 IM4 MM5 Send-DownReqmw MM6 MM7 MM8 IM5 MM9 IM5 MM10 IM5 MM11 IM6 + Send-DownReqwb MM12 IM6 MM13 IM7 + Send-DownReqwb MM14 IM7 MM15 IM8 + Send-DownReqmw + Send-DownReqwb MM16 IM8 + Send-DownReqwb MM17 IM8 MM18 IM9 MM19 IM9 MM20 IM9 MM21 IM10 MM22 IM10 MM23 IM11 MM24 IM11 MM25 IM11 MM26 IM12 MM27 IM12 MM28 IM12 MM29 IM13 MM30 IM13 MM31 IM13 MM32 IM14 MM33 IM15 MM34 Figure 7.16: Derivation <strong>of</strong> Memory Engine Rules <strong>of</strong> <strong>Cache</strong>t Figure 7.18 gives the basic rules used in the simulation <strong>of</strong> each composite rule. The <strong>Cache</strong>t Protocol Appendix A gives the speci cation <strong>of</strong> the complete <strong>Cache</strong>t protocol, which contains the basic rules de ned in Figures 7.11, 7.12 <strong>and</strong> 7.13, <strong>and</strong> the composite rules de ned in Figure 7.17. The <strong>Cache</strong>t protocol is an adaptive cache coherence protocol, although for pedagogic reason it has been been presented as an integration <strong>of</strong> several micro-protocols. One can also think <strong>Cache</strong>t as a family <strong>of</strong> protocols because <strong>of</strong> the presence <strong>of</strong> voluntary rules that can be invoked without the execution <strong>of</strong> an instruction or the receipt <strong>of</strong> a message. The existence <strong>of</strong> voluntary rules provides enormous extensibility in the sense that various heuristic messages <strong>and</strong> states can be employed to invoke these rules. As an example <strong>of</strong> how the adaptivity can be exploited, consider a DSM system with limited directory space. When the memory receives a cache request, it can respond under Base or WP. 156
Composite M<strong>and</strong>atory Processor Rules Instruction Cstate Action Next Cstate Commit(a) Cell(a,v,Dirtyw) stall, hWbw,a,vi!H Cell(a,v,WbPending) CP1 Composite Voluntary C-engine Rules Cstate Action Next Cstate Cell(a,v,Dirtyw) hWbw,a,vi!H Cell(a,v,WbPending) CVC1 Cell(a,v,Cleanm) hDownmb,ai!H Cell(a,v,Cleanb) CVC2 Cell(a,v,Dirtym) hDownVmb,a,vi!H Cell(a,v,Cleanb) CVC3 Composite M<strong>and</strong>atory C-engine Rules h<strong>Cache</strong>m,a,vi Cell(a,-,Cleanb) Cell(a,v,Cleanm) CMC1 Cell(a,v1,Dirtyb) Cell(a,v1,Dirtym) CMC2 Cell(a,v1,WbPending) Cell(a,v1,WbPending) CMC3 Cell(a,-,<strong>Cache</strong>Pending) Cell(a,v,Cleanm) CMC4 a =2 cache Cell(a,v,Cleanm) CMC5 hWbAckm,ai Cell(a,v,WbPending) Cell(a,v,Cleanm) CMC6 hDownReqmb,ai Cell(a,v,Cleanb) Cell(a,v,Cleanb) CMC7 Cell(a,v,Dirtyb) Cell(a,v,Dirtyb) CMC8 Cell(a,v,Cleanw) hDownwb,ai!H Cell(a,v,Cleanb) CMC9 Cell(a,v,Dirtyw) hDownwb,ai!H Cell(a,v,Dirtyb) CMC10 Cell(a,v,Cleanm) hDownmb,ai!H Cell(a,v,Cleanb) CMC11 Cell(a,v,Dirtym) hDownVmb,a,vi!H Cell(a,v,Cleanb) CMC12 Cell(a,v,WbPending) Cell(a,v,WbPending) CMC13 Cell(a,-,<strong>Cache</strong>Pending) Cell(a,-,<strong>Cache</strong>Pending) CMC14 a =2 cache a =2 cache CMC15 Composite Voluntary M-engine Rules Mstate Action Next Mstate Cell(a,v,Cw[ ]) h<strong>Cache</strong>m,a,vi!id Cell(a,v,Cm[id ]) CVM1 Cell(a,v,Cm[id ]) hDownReqmb,ai!id Cell(a,v,Tm[id , ]) CVM2 Composite M<strong>and</strong>atory M-engine Rules hWbw,a,vi Cell(a,v1,Cw[id jdir]) hDownReqwb,ai!dir Cell(a,v1,Tw[dir,(id ,v)]) CMM1 Cell(a,v1,Tw[id jdir,sm]) Cell(a,v1,Tw[dir,(id ,v)jsm]) CMM2 Cell(a,v1,Cm[id ]) Cell(a,v1,Tw[ ,(id ,v)]) CMM3 Cell(a,v1,T 0 m[id ]) Cell(a,v1,Tw[ ,(id ,v)]) CMM4 Cell(a,v1,Tm[id ,sm]) Cell(a,v1,Tw[ ,(id ,v)jsm]) CMM5 hDownmb,ai Cell(a,v,Cm[id ]) Cell(a,v,Cw[ ]) CMM6 Cell(a,v,T 0 m[id ]) Cell(a,v,Cw[ ]) CMM7 Cell(a,v,Tm[id ,sm]) Cell(a,v,Tw[ ,sm]) CMM8 hDownVmb,a,vi Cell(a,-,Cm[id ]) Cell(a,v,Cw[ ]) CMM9 Cell(a,-,T 0 m[id ]) Cell(a,v,Cw[ ]) CMM10 Cell(a,-,Tm[id ,sm]) Cell(a,v,Tw[ ,sm]) CMM11 Cell(a,-,Tw[ ,(id ,v)]) hWbAckm,ai!id Cell(a,v,Cm[id ]) CMM12 Figure 7.17: Composite Rules <strong>of</strong> <strong>Cache</strong>t 157
- Page 1:
CSAIL Computer Science and Artifici
- Page 5:
Design and Veri cation of Adaptive
- Page 8 and 9:
I am truly grateful to my parents f
- Page 10 and 11:
4 The Base Cache Coherence Protocol
- Page 13 and 14:
List of Figures 1.1 Impact of Archi
- Page 15 and 16:
Chapter 1 Introduction Shared memor
- Page 17 and 18:
transparent and exposed only for lo
- Page 19 and 20:
Example 1: Can both registers r1 an
- Page 21 and 22:
and release locks, which guard ever
- Page 23 and 24:
that are interconnected with an o -
- Page 25 and 26:
although various techniques have be
- Page 27 and 28:
y showing that each processor can a
- Page 29 and 30:
s1 if p (s1) ! s2 where s1 and s2 a
- Page 31 and 32:
Program counter (pc) +1 Instruction
- Page 33 and 34:
Branch target buffer (btb) Program
- Page 35 and 36:
instruction is waiting to be dispat
- Page 37 and 38:
Current State: Proc(ia, rf , rob, b
- Page 39 and 40:
Rule Name mem pmb mpb Next mem Next
- Page 41 and 42:
Specification Implementation t 1 B
- Page 43 and 44:
Intuitively, \2P " means that \P is
- Page 45 and 46:
(a) (b) PC 1005 PC 2000 Instruction
- Page 47 and 48:
ewritten to s2 according to rule R.
- Page 49 and 50:
It can be shown that the relaxed di
- Page 51 and 52:
Chapter 3 The Commit-Reconcile & Fe
- Page 53 and 54:
Producer Storel(a,v) Commit(a) Cons
- Page 55 and 56:
Commit/Reconcile Purge Loadl/Commit
- Page 57 and 58:
instructions, because of the lack o
- Page 59 and 60:
CRF-Relaxed-Commit Rule Site(sache,
- Page 61 and 62:
3.4 Universality of the CRF Model M
- Page 63 and 64:
Translation from CRF to PSO: The Fe
- Page 65 and 66:
proc proc proc pmb mpb pmb mpb pmb
- Page 67 and 68:
Chapter 4 The Base Cache Coherence
- Page 69 and 70:
can be classi ed into two non-overl
- Page 71 and 72:
arbitrarily in an outgoing queue (t
- Page 73 and 74:
4.3 The Imperative Rules of the Bas
- Page 75 and 76:
Imperative Processor Rules Instruct
- Page 77 and 78:
Figure 4.5 de nes the rules of the
- Page 79 and 80:
4.5.2 Mapping from Base to CRF We d
- Page 81 and 82:
Base Imperative Rule CRF Rule IP1 (
- Page 83 and 84:
Base Rule Base Imperative Rule P1 I
- Page 85 and 86:
eceives a CacheReq message, it will
- Page 87 and 88:
e completed if it has an in nite nu
- Page 89 and 90:
SYS Sys(MSITE, SITEs) System MSITE
- Page 91 and 92:
Commit/Reconcile C-Receive-WbAck Ru
- Page 93 and 94:
message can be resumed eventually.
- Page 95 and 96:
If the memory state shows that the
- Page 97 and 98:
5.3.3 FIFO Message Passing The live
- Page 99 and 100:
Figure 5.7 gives the M-engine rules
- Page 101 and 102:
Backward-Message-Cache-to-Mem-for-W
- Page 103 and 104:
5.4.3 Simulation of WP in CRF Theor
- Page 105 and 106:
WP Imperative Rule CRF Rules IP1 (L
- Page 107 and 108: WP Rule WP Imperative & Directive R
- Page 109 and 110: (4) Msg(H,id ,Cache,a,-)" 2 Cin id(
- Page 111 and 112: This completes the proof according
- Page 113 and 114: emains as CachePending, there mustb
- Page 115 and 116: M-engine Rules Msg from id Mstate A
- Page 117 and 118: Chapter 6 The Migratory Cache Coher
- Page 119 and 120: Commit/Reconcile Send Purge Loadl/C
- Page 121 and 122: Mandatory Processor Rules Instructi
- Page 123 and 124: while the memory sends a FlushReq m
- Page 125 and 126: Lemma 38 D is strongly terminating
- Page 127 and 128: Migratory Imperative Rule CRF Rules
- Page 129 and 130: Cell(a,v,C[id ]) 2 Mem(s) _ Cell(a,
- Page 131 and 132: According to Theorem-C and Lemma 45
- Page 133 and 134: CacheReq message. In the latter cas
- Page 135 and 136: Chapter 7 Cachet: A Seamless Integr
- Page 137 and 138: 7.1.1 Putting Things Together It is
- Page 139 and 140: Writeback Operations In Cachet, a w
- Page 141 and 142: Composite Message Equivalent Sequen
- Page 143 and 144: Imperative Processor Rules Instruct
- Page 145 and 146: Invalid Commit/Reconcile Receive Ca
- Page 147 and 148: Composite Imperative C-engine Rules
- Page 149 and 150: 7.4 The Cachet Cache Coherence Prot
- Page 151 and 152: Voluntary C-engine Rules Cstate Act
- Page 153 and 154: The memory processes an incoming Ca
- Page 155 and 156: The inaccuracy of memory states can
- Page 157: C-engine Rule of Cachet Deriving Im
- Page 161 and 162: memory regions simultaneously. In a
- Page 163 and 164: Chapter 8 Conclusions This thesis h
- Page 165 and 166: and heuristic policies. Mandatory r
- Page 167 and 168: technique can be used to allow a ca
- Page 169 and 170: Voluntary C-engine Rules Cstate Act
- Page 171 and 172: FIFO Message Passing msg1 msg2 msg2
- Page 173 and 174: [13] J. K. Archibald. The Cache Coh
- Page 175 and 176: [41] A. Erlichson, N. Nuckolls, G.
- Page 177 and 178: [71] J. Kuskin, D. Ofelt, M. Heinri
- Page 179 and 180: [101] F. Pong and M. Dubois. A New