Design and Verification of Adaptive Cache Coherence Protocols ...
Design and Verification of Adaptive Cache Coherence Protocols ...
Design and Verification of Adaptive Cache Coherence Protocols ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
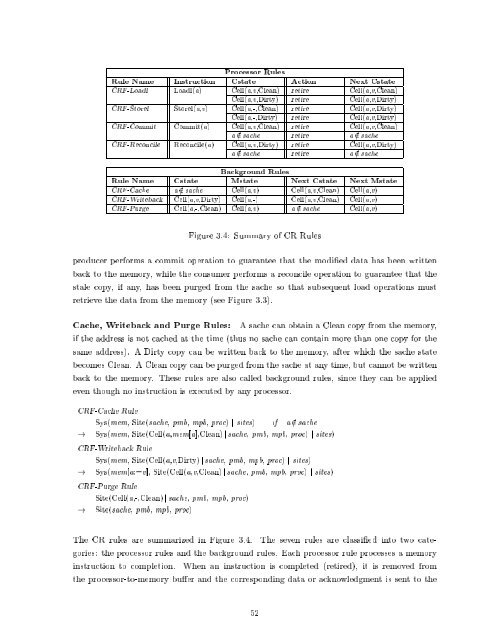
Processor Rules<br />
Rule Name Instruction Cstate Action Next Cstate<br />
CRF-Loadl Loadl(a) Cell(a,v,Clean) retire Cell(a,v,Clean)<br />
Cell(a,v,Dirty) retire Cell(a,v,Dirty)<br />
CRF-Storel Storel(a,v) Cell(a,-,Clean) retire Cell(a,v,Dirty)<br />
Cell(a,-,Dirty) retire Cell(a,v,Dirty)<br />
CRF-Commit Commit(a) Cell(a,v,Clean) retire Cell(a,v,Clean)<br />
a =2 sache retire a =2 sache<br />
CRF-Reconcile Reconcile(a) Cell(a,v,Dirty) retire Cell(a,v,Dirty)<br />
a =2 sache retire a =2 sache<br />
Background Rules<br />
Rule Name Cstate Mstate Next Cstate Next Mstate<br />
CRF-<strong>Cache</strong> a =2 sache Cell(a,v) Cell(a,v,Clean) Cell(a,v)<br />
CRF-Writeback Cell(a,v,Dirty) Cell(a,-) Cell(a,v,Clean) Cell(a,v)<br />
CRF-Purge Cell(a,-,Clean) Cell(a,v) a =2 sache Cell(a,v)<br />
Figure 3.4: Summary <strong>of</strong> CR Rules<br />
producer performs a commit operation to guarantee that the modi ed data has been written<br />
back to the memory, while the consumer performs a reconcile operation to guarantee that the<br />
stale copy, if any, has been purged from the sache so that subsequent load operations must<br />
retrieve the data from the memory (see Figure 3.3).<br />
<strong>Cache</strong>, Writeback <strong>and</strong> Purge Rules: Asache can obtain a Clean copy from the memory,<br />
if the address is not cached at the time (thus no sache can contain more than one copy for the<br />
same address). A Dirty copy can be written back to the memory, after which thesache state<br />
becomes Clean. A Clean copy can be purged from the sache at any time, but cannot be written<br />
back to the memory. These rules are also called background rules, since they can be applied<br />
even though no instruction is executed by any processor.<br />
CRF-<strong>Cache</strong> Rule<br />
Sys(mem, Site(sache, pmb, mpb, proc) j sites) if a =2 sache<br />
! Sys(mem, Site(Cell(a,mem[a],Clean) j sache, pmb, mpb, proc) j sites)<br />
CRF-Writeback Rule<br />
Sys(mem, Site(Cell(a,v,Dirty) j sache, pmb, mpb, proc) j sites)<br />
! Sys(mem[a:=v], Site(Cell(a,v,Clean) j sache, pmb, mpb, proc) j sites)<br />
CRF-Purge Rule<br />
Site(Cell(a,-,Clean) j sache, pmb, mpb, proc)<br />
! Site(sache, pmb, mpb, proc)<br />
The CR rules are summarized in Figure 3.4. The seven rules are classi ed into two cate-<br />
gories: the processor rules <strong>and</strong> the background rules. Each processor rule processes a memory<br />
instruction to completion. When an instruction is completed (retired), it is removed from<br />
the processor-to-memory bu er <strong>and</strong> the corresponding data or acknowledgment is sent to the<br />
52