Design and Verification of Adaptive Cache Coherence Protocols ...
Design and Verification of Adaptive Cache Coherence Protocols ...
Design and Verification of Adaptive Cache Coherence Protocols ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
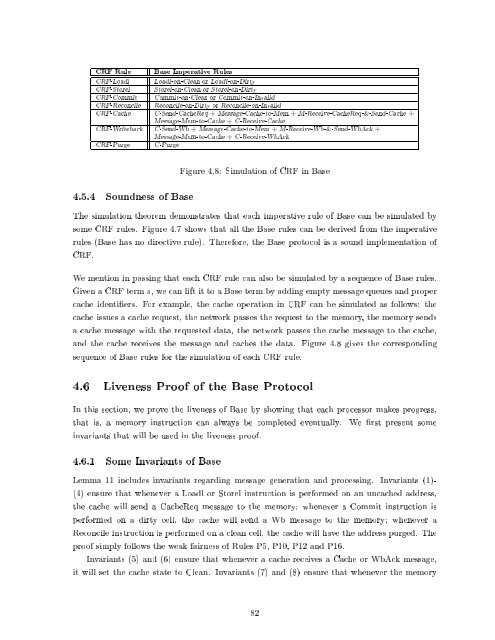
CRF Rule Base Imperative Rules<br />
CRF-Loadl Loadl-on-Clean or Loadl-on-Dirty<br />
CRF-Storel Storel-on-Clean or Storel-on-Dirty<br />
CRF-Commit Commit-on-Clean or Commit-on-Invalid<br />
CRF-Reconcile Reconcile-on-Dirty or Reconcile-on-Invalid<br />
CRF-<strong>Cache</strong> C-Send-<strong>Cache</strong>Req + Message-<strong>Cache</strong>-to-Mem + M-Receive-<strong>Cache</strong>Req-&-Send-<strong>Cache</strong> +<br />
Message-Mem-to-<strong>Cache</strong> + C-Receive-<strong>Cache</strong><br />
CRF-Writeback C-Send-Wb + Message-<strong>Cache</strong>-to-Mem + M-Receive-Wb-&-Send-WbAck +<br />
Message-Mem-to-<strong>Cache</strong> + C-Receive-WbAck<br />
CRF-Purge C-Purge<br />
4.5.4 Soundness <strong>of</strong> Base<br />
Figure 4.8: Simulation <strong>of</strong> CRF in Base<br />
The simulation theorem demonstrates that each imperative rule <strong>of</strong> Base can be simulated by<br />
some CRF rules. Figure 4.7 shows that all the Base rules can be derived from the imperative<br />
rules (Base has no directive rule). Therefore, the Base protocol is a sound implementation <strong>of</strong><br />
CRF.<br />
We mention in passing that each CRF rule can also be simulated by a sequence <strong>of</strong> Base rules.<br />
Given a CRF term s, we can lift it to a Base term by adding empty message queues <strong>and</strong> proper<br />
cache identi ers. For example, the cache operation in CRF can be simulated as follows: the<br />
cache issues a cache request, the network passes the request to the memory, the memory sends<br />
a cache message with the requested data, the network passes the cache message to the cache,<br />
<strong>and</strong> the cache receives the message <strong>and</strong> caches the data. Figure 4.8 gives the corresponding<br />
sequence <strong>of</strong> Base rules for the simulation <strong>of</strong> each CRF rule.<br />
4.6 Liveness Pro<strong>of</strong> <strong>of</strong> the Base Protocol<br />
In this section, we prove the liveness <strong>of</strong> Base by showing that each processor makes progress,<br />
that is, a memory instruction can always be completed eventually. We rst present some<br />
invariants that will be used in the liveness pro<strong>of</strong>.<br />
4.6.1 Some Invariants <strong>of</strong> Base<br />
Lemma 11 includes invariants regarding message generation <strong>and</strong> processing. Invariants (1)-<br />
(4) ensure that whenever a Loadl or Storel instruction is performed on an uncached address,<br />
the cache will send a <strong>Cache</strong>Req message to the memory whenever a Commit instruction is<br />
performed on a dirty cell, the cache will send a Wb message to the memory whenever a<br />
Reconcile instruction is performed on a clean cell, the cache will have the address purged. The<br />
pro<strong>of</strong> simply follows the weak fairness <strong>of</strong> Rules P5, P10, P12 <strong>and</strong> P16.<br />
Invariants (5) <strong>and</strong> (6) ensure that whenever a cache receives a <strong>Cache</strong> or WbAck message,<br />
it will set the cache state to Clean. Invariants (7) <strong>and</strong> (8) ensure that whenever the memory<br />
82