Design and Verification of Adaptive Cache Coherence Protocols ...
Design and Verification of Adaptive Cache Coherence Protocols ...
Design and Verification of Adaptive Cache Coherence Protocols ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>and</strong> heuristic policies. M<strong>and</strong>atory rules are weakly or strongly fair to ensure the liveness <strong>of</strong><br />
the system, while voluntary rules have no such requirement <strong>and</strong> are used to specify adaptive<br />
actions without giving particular enabling conditions. Therefore, we can also think <strong>of</strong> <strong>Cache</strong>t as<br />
a family <strong>of</strong> cache coherence protocols in that a heuristic policy for selecting adaptive operations<br />
de nes a complete protocol tailored for some particular access patterns. Di erent heuristic<br />
policies can exhibit di erent performance, but can never a ect the soundness <strong>and</strong> liveness <strong>of</strong><br />
the protocol.<br />
We have proposed the two-stage Imperative-&-Directive methodology that separates the sound-<br />
ness <strong>and</strong> liveness concerns throughout protocol design <strong>and</strong> veri cation. The rst stage involves<br />
only imperative rules that specify coherence actions that determine the soundness <strong>of</strong> the sys-<br />
tem. The second stage involves directive rules <strong>and</strong> the integration <strong>of</strong> imperative <strong>and</strong> directive<br />
rules to ensure both the soundness <strong>and</strong> liveness simultaneously. The Imperative-&-Directive<br />
methodology can dramatically simplify the design <strong>and</strong> veri cation <strong>of</strong> sophisticated cache coher-<br />
ence protocols, because only imperative rules need to be considered while verifying soundness<br />
properties. This novel methodology was rst applied to the design <strong>of</strong> a cache coherence protocol<br />
for a DSM system with multi-level caches [110].<br />
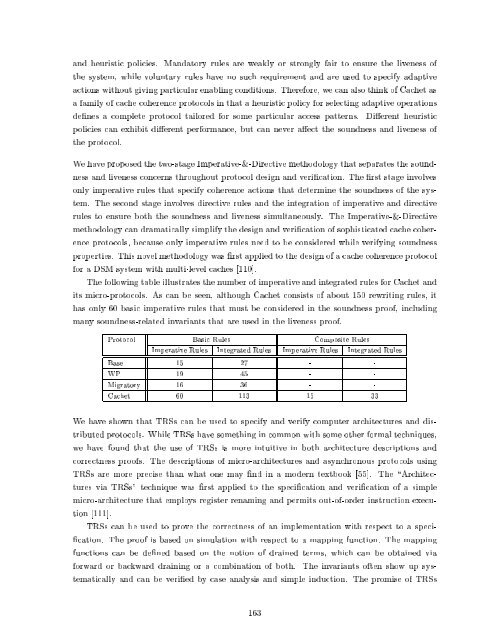
The following table illustrates the number <strong>of</strong> imperative <strong>and</strong> integrated rules for <strong>Cache</strong>t <strong>and</strong><br />
its micro-protocols. As can be seen, although <strong>Cache</strong>t consists <strong>of</strong> about 150 rewriting rules, it<br />
has only 60 basic imperative rules that must be considered in the soundness pro<strong>of</strong>, including<br />
many soundness-related invariants that are used in the liveness pro<strong>of</strong>.<br />
Protocol Basic Rules Composite Rules<br />
Imperative Rules Integrated Rules Imperative Rules Integrated Rules<br />
Base 15 27 - -<br />
WP 19 45 - -<br />
Migratory 16 36 - -<br />
<strong>Cache</strong>t 60 113 15 33<br />
We have shown that TRSs can be used to specify <strong>and</strong> verify computer architectures <strong>and</strong> dis-<br />
tributed protocols. While TRSs have something in common with some other formal techniques,<br />
we have found that the use <strong>of</strong> TRSs is more intuitive in both architecture descriptions <strong>and</strong><br />
correctness pro<strong>of</strong>s. The descriptions <strong>of</strong> micro-architectures <strong>and</strong> asynchronous protocols using<br />
TRSs are more precise than what one may nd in a modern textbook [55]. The \Architec-<br />
tures via TRSs" technique was rst applied to the speci cation <strong>and</strong> veri cation <strong>of</strong> a simple<br />
micro-architecture that employs register renaming <strong>and</strong> permits out-<strong>of</strong>-order instruction execu-<br />
tion [111].<br />
TRSs can be used to prove the correctness <strong>of</strong> an implementation with respect to a speci-<br />
cation. The pro<strong>of</strong> is based on simulation with respect to a mapping function. The mapping<br />
functions can be de ned based on the notion <strong>of</strong> drained terms, which can be obtained via<br />
forward or backward draining or a combination <strong>of</strong> both. The invariants <strong>of</strong>ten show up sys-<br />
tematically <strong>and</strong> can be veri ed by case analysis <strong>and</strong> simple induction. The promise <strong>of</strong> TRSs<br />
163