Customs Declaration Processing System Detailed User and ...
Customs Declaration Processing System Detailed User and ...
Customs Declaration Processing System Detailed User and ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
DETAILED USER & TECHNICAL REQUIREMENTS FOR CDPS<br />
AND USE-CASE MODELS<br />
Ref: PHASE V<br />
Number<br />
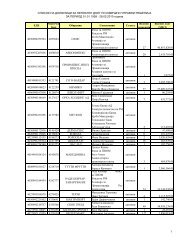
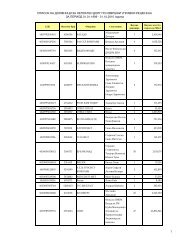
SR-0080<br />
SR-0090<br />
SR-0100<br />
SR-0105<br />
SR-0110<br />
SR-0120<br />
SR-0130<br />
SR-0200<br />
SR-0210<br />
SR-0220<br />
SR-0230<br />
SR-0240<br />
SR-0270<br />
SR-0280<br />
SR-0300<br />
SR-0310<br />
SR-0320<br />
SR-0330<br />
SR-0340<br />
SR-0350<br />
Description<br />
It must be possible for MCA to define <strong>User</strong> Access Policies according to<br />
functional rules.<br />
All security relevant events must be audited.<br />
The time st<strong>and</strong>ard used for auditing is Greenwich Mean Time.<br />
CDPS must address the requirements to maintain an audit trail of all changes to<br />
data based on user requests. Proper logs should be maintained in a secure<br />
manner for audit of transactions recorded, changes made to data <strong>and</strong> queries<br />
initiated against end-user request with timestamps to enable examination of the<br />
audit trail at a later date. In addition, CDPS must provide the functionality for<br />
secure management <strong>and</strong> access to log files maintained on-line <strong>and</strong> off-line.<br />
Workstations must be capable of being uniquely identified.<br />
A listing (report) must be maintained including all MCA Workstation IP<br />
addresses, their software revision <strong>and</strong> the group they belong to.<br />
A listing (report) should be maintained including all system users, their access<br />
profile, Workstation <strong>and</strong> Workstation group.<br />
A firewall should be put in place between the MCA <strong>and</strong> the public network (e.g.<br />
between the DTI Trader connections <strong>and</strong> the MCA Server).<br />
<strong>User</strong> identification, user authentication, Workstation identification <strong>and</strong> access<br />
control procedures should be implemented between the MCA server <strong>and</strong> the<br />
Workstation components.<br />
The NCA server should terminate the connection of a Workstation after a period<br />
of inactivity defined in a configuration parameter.<br />
It is recommended that only one login shall be necessary for a <strong>User</strong> to access the<br />
different CDPS applications when pertaining to the same access rights.<br />
IT <strong>User</strong>s must be identified (as a minimum) using user names <strong>and</strong> authenticated<br />
using passwords.<br />
The MCA Domain Administrator should be able to configure the events which<br />
need to be audited in the MCA server.<br />
Duplicate CDPS messages, including acknowledgements, should be logged,<br />
brought to the attention of the <strong>System</strong> Administrator <strong>and</strong> discarded.<br />
The files downloaded from Internet must be virus checked.<br />
CDPS must address the requirement for providing multiple levels of access to<br />
system functionality based on roles assigned to both the MCA IT staff <strong>and</strong> endusers<br />
at any point in time. In addition, CDPS must support the functionality to<br />
grant <strong>and</strong> revoke both permissions <strong>and</strong> authorizations to end-users in a secure<br />
traceable environment.<br />
CDPS must address the need for securing <strong>and</strong> safeguarding of data through<br />
logging of ALL modifications to sensitive data<br />
CDPS must provide the functionality for role-based security <strong>and</strong> access to data<br />
<strong>and</strong> system functionality as well as guard against unauthorized use, copying <strong>and</strong><br />
transmission of data maintained in the database.<br />
Role-based security must be an integral part of CDPS <strong>and</strong> must include an<br />
administration component for updating <strong>and</strong> controlling access to individual subsystems<br />
<strong>and</strong> potentially to data within the database.<br />
By addressing the above requirements, CDPS must reduce to the absolute<br />
minimum the need by MCA IT staff to directly access the database tables using<br />
database utilities.<br />
Page 142/276