Download - Academy Publisher
Download - Academy Publisher
Download - Academy Publisher
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
A. Data Preparing<br />
To generate our test data, snort [16] was chosen as our<br />
IDS, which is a popular open-source Network Intrusion<br />
Detection System (NIDS). The data was accumulated<br />
from our campus network for one month by activating<br />
default rule sets of the Snort. Interestingly, more than 200<br />
signatures had triggered alarms, We choose 5 minutes as<br />
the sampling interval to generate the alarm flows.<br />
B. Parameter Selection<br />
Before the decomposition, we should select the values<br />
of just two parameters, namely, the lag window length M<br />
and the number l of leading components contained in the<br />
subset I 1 = {i 1 , . . . , i l }. The SVD performed on matrices<br />
obtained with a window length M is equivalent to that<br />
performed on matrices obtained with the complementary<br />
window K = N – M + 1. This means increasing the<br />
window length would reproduce results already tested<br />
with shorter window lengths, and too large window<br />
length may introduce some disturbance. Where, l is such<br />
that the first l components provide a good description of<br />
the normal part of the signal and the lower M-l<br />
components correspond to abnormal part. If l is too small<br />
(under-fitting), we miss a part of the normal signal.<br />
Alternatively, if l is too large (over-fitting), then we<br />
approximate a part of abnormal signal with the normal<br />
part. Both of these cases will make it difficult for us to<br />
detect the deviations from the normal profile.<br />
L3retriever Ping. wo different widow lengths M 1 = 60<br />
and M 2 = 100 are used for comparing and anglicizing the<br />
results.<br />
As it can be seen from both cases, only the first few<br />
eigenvalues are responsible for the main part of the flow<br />
information. This means we can reconstruct the major<br />
behavior of the alarm flow by using the first few leading<br />
components. In fact, the first 3 eigenvalues account for<br />
more than 90 percent of the whole energy, therefore we<br />
prefer to choose M = 60 and l = 3 to continue the<br />
following experiments and analysis.<br />
C. Case Study<br />
We use two case to make the threat evaluation, one is a<br />
alarm flow created by the signature BARE BYTE<br />
UNICODE ENCODING (http_inspect), the other is the<br />
alarm flow created by the signature ICMP L3retriever<br />
Ping. Both cases use one day’s data to perform SSAbased<br />
decomposition and signal reconstructing. The<br />
1<br />
reconstructed signal X I<br />
() t is plotted in Fig.2 (a), Fig.3<br />
(a) along with the original signal, and the residual series<br />
2<br />
X I<br />
() t can be easily obtained from the equation (4)<br />
by I 2<br />
I<br />
1<br />
X () t = X () t − X () t , which is plotted in Fig.2 (b),<br />
Fig.3 (b).<br />
Fig.2 Case 1 for http_inspect flow: (a) Original alarm flow series<br />
(dotted line) and SSA-reconstructed series (continuous line)<br />
corresponding to normal flow behavior. (b) Residual series defined as<br />
the difference between the original and reconstructed series.<br />
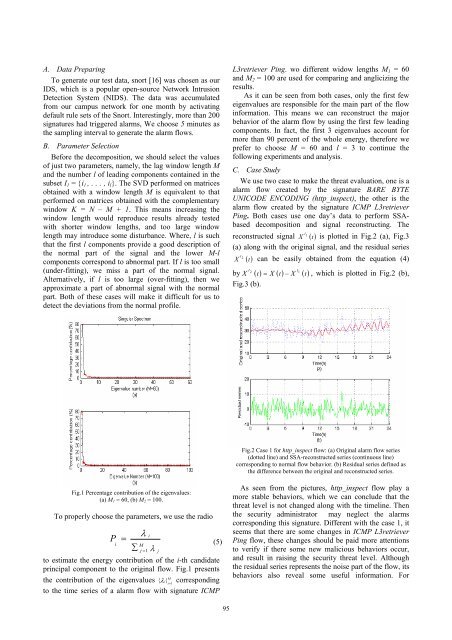
Fig.1 Percentage contribution of the eigenvalues:<br />
(a) M 1 = 60, (b) M 2 = 100.<br />
To properly choose the parameters, we use the radio<br />
P<br />
i<br />
λ<br />
i<br />
= (5)<br />
M<br />
∑<br />
j = 1 λ j<br />
to estimate the energy contribution of the i-th candidate<br />
principal component to the original flow. Fig.1 presents<br />
M<br />
the contribution of the eigenvalues { λ i} i = 1<br />
corresponding<br />
to the time series of a alarm flow with signature ICMP<br />
As seen from the pictures, http_inspect flow play a<br />
more stable behaviors, which we can conclude that the<br />
threat level is not changed along with the timeline. Then<br />
the security administrator may neglect the alarms<br />
corresponding this signature. Different with the case 1, it<br />
seems that there are some changes in ICMP L3retriever<br />
Ping flow, these changes should be paid more attentions<br />
to verify if there some new malicious behaviors occur,<br />
and result in raising the security threat level. Although<br />
the residual series represents the noise part of the flow, its<br />
behaviors also reveal some useful information. For<br />
95