Download - Academy Publisher
Download - Academy Publisher
Download - Academy Publisher
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
ISBN 978-952-5726-09-1 (Print)<br />
Proceedings of the Second International Symposium on Networking and Network Security (ISNNS ’10)<br />
Jinggangshan, P. R. China, 2-4, April. 2010, pp. 190-192<br />
A Study on High-Strength Communication<br />
Scheme Based on Signed Digital Envelope<br />
Wenping Guo, Ying Chen, and Xiaoming Zhao<br />
School of Mathematics and Information Engineering, Taizhou University, Linhai, China<br />
Email: guo_wp@126.com , ychen222@163.com , tzxyzxm@yahoo.com.cn<br />
Abstract—The digital signature and digital envelope, two<br />
specific applications of computer technology, have been<br />
widely used in data communication, but the application of<br />
either one may cause some deficiencies in practice. Based on<br />
the current cryptographic techniques and the study on<br />
digital signature and digital envelope, this paper proposed a<br />
new scheme, signed digital envelope. It can overcome the<br />
shortcomings of the two technologies that bring along, and<br />
the security of data communication is thereby greatly<br />
strengthened.<br />
Index Terms—Digital signature, Digital envelope, Signed<br />
digital envelope<br />
I. INTRODUCTION<br />
With widespread use of the Internet, people are more<br />
aware of the network security. How to efficiently block<br />
intruders’ access to personal computer and their alteration<br />
of unauthorized data is one of the burning problems at<br />
present. In the field of data communication, data security<br />
is mainly concerning three indicators, confidentiality,<br />
integrity and undeniability, but the conventional digital<br />
signature and digital envelope still need some<br />
improvements before achieving the above- mentioned<br />
three indicators. In this paper, we took advantages of<br />
digital signature and digital envelope’s role in data<br />
protection and proposed a high-secure scheme, signed<br />
digital envelope, which ensures data communication<br />
against being intruded.<br />
infeasible to generate a valid signature for a party who<br />
does not possess the private key.<br />
Digital signature is used to ensure that the message in<br />
transit is integrated, and that the source of the message is<br />
authenticated and undeniable. Digital signature uses what<br />
is known as public key algorithm. The use of public key<br />
cryptography for digital signature is similar with public<br />
key encryption. It has two keys, one is signing key which<br />
must be kept private, referred to as private key, the other<br />
is verification key which is open, referred to as public key.<br />
The big computing workload slows down the computing<br />
speed of public key algorithm, so we can use secure oneway<br />
hash function to summarize the message so as to<br />
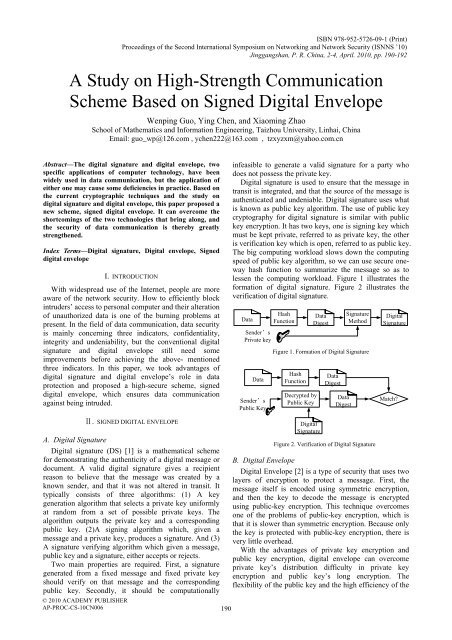
lessen the computing workload. Figure 1 illustrates the<br />
formation of digital signature. Figure 2 illustrates the<br />
verification of digital signature.<br />
Data<br />
Sender’s<br />
Private key<br />
Data<br />
Sender’s<br />
Public Key<br />
Hash<br />
Function<br />
Data<br />
Digest<br />
Signature<br />
Method<br />
Figure 1. Formation of Digital Signature<br />
Hash<br />
Function<br />
Decrypted by<br />
Public Key<br />
Data<br />
Digest<br />
Data<br />
Digest<br />
Digital<br />
Signature<br />
Match<br />
Ⅱ. SIGNED DIGITAL ENVELOPE<br />
A. Digital Signature<br />
Digital signature (DS) [1] is a mathematical scheme<br />
for demonstrating the authenticity of a digital message or<br />
document. A valid digital signature gives a recipient<br />
reason to believe that the message was created by a<br />
known sender, and that it was not altered in transit. It<br />
typically consists of three algorithms: (1) A key<br />
generation algorithm that selects a private key uniformly<br />
at random from a set of possible private keys. The<br />
algorithm outputs the private key and a corresponding<br />
public key. (2)A signing algorithm which, given a<br />
message and a private key, produces a signature. And (3)<br />
A signature verifying algorithm which given a message,<br />
public key and a signature, either accepts or rejects.<br />
Two main properties are required. First, a signature<br />
generated from a fixed message and fixed private key<br />
should verify on that message and the corresponding<br />
public key. Secondly, it should be computationally<br />
© 2010 ACADEMY PUBLISHER<br />
AP-PROC-CS-10CN006<br />
190<br />
Digital<br />
Signature<br />
Figure 2. Verification of Digital Signature<br />
B. Digital Envelope<br />
Digital Envelope [2] is a type of security that uses two<br />
layers of encryption to protect a message. First, the<br />
message itself is encoded using symmetric encryption,<br />
and then the key to decode the message is encrypted<br />
using public-key encryption. This technique overcomes<br />
one of the problems of public-key encryption, which is<br />
that it is slower than symmetric encryption. Because only<br />
the key is protected with public-key encryption, there is<br />
very little overhead.<br />
With the advantages of private key encryption and<br />
public key encryption, digital envelope can overcome<br />
private key’s distribution difficulty in private key<br />
encryption and public key’s long encryption. The<br />
flexibility of the public key and the high efficiency of the