Download - Academy Publisher
Download - Academy Publisher
Download - Academy Publisher
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Enterprise Portal security provides a graphics-based<br />
administrative interface, relies on standards-based<br />
security mechanisms, and provides interoperability with<br />
existing Internet and enterprise security infrastructures<br />
such as secure socket layers (SSLs) and public-key<br />
infrastructures (PKIs) [2].<br />
B. Enterprise Portal security architecture<br />
Enterprise Portal security services include these<br />
elements:<br />
• A security servlet on the Web server<br />
• Enterprise Portal Application Server components<br />
• The connection manager<br />
• The object manager<br />
• The SBO<br />
• The Access Control Database (the security<br />
repository)<br />
The Portal Security Officer manages Enterprise Portal<br />
security using the Enterprise Portal Security Manager, a<br />
graphics-based administration tool. The security<br />
architecture provides a uniform structure for user<br />
authentication and authorization for the entire Enterprise<br />
Portal—including both Sybase and non-Sybase<br />
applications and components.<br />
VII. LOGCISQL-BASED ARCHIVE AND SEARCH SYSTEM<br />
LogicSQL [8] is independently developed based on the<br />
Linux high-level security database system [3]. Ministry<br />
of Science and Technology "863" Database Group of the<br />
major projects comments LogicSQL database "It is the<br />
only hope that China’s database products will be able to<br />
contend with America’s mainstream database products in<br />
the next few years."<br />
The core functions of the system as follows: Archiving<br />
that replaces the traditional backup functions is<br />
completed in the system; Information on the enterprise<br />
server and personal computers are protected and managed;<br />
The latest search technology is used to realize the rapid<br />
and accurate searching for the backup information,<br />
including keyword, semantics, the integrated use of<br />
intelligent search technology; Search results are<br />
consistent with the security level of users.<br />
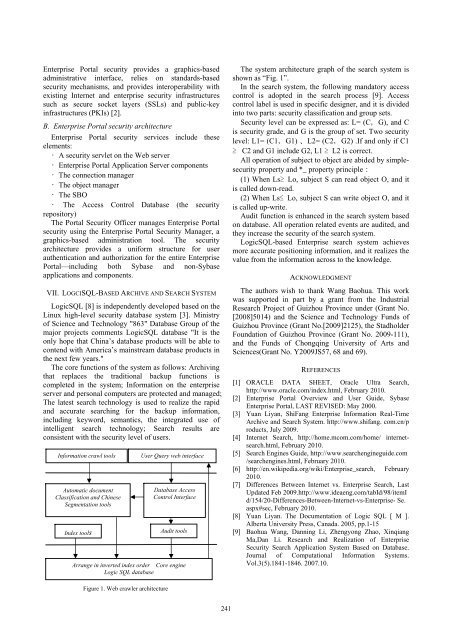
Information crawl tools<br />
Automatic document<br />
Classification and Chinese<br />
Segmentation tools<br />
Index tools<br />
User Query web interface<br />
Database Access<br />
Control Interface<br />
Audit tools<br />
Arrange in inverted index order Core engine<br />
Logic SQL database<br />
The system architecture graph of the search system is<br />
shown as “Fig. 1”.<br />
In the search system, the following mandatory access<br />
control is adopted in the search process [9]. Access<br />
control label is used in specific designer, and it is divided<br />
into two parts: security classification and group sets.<br />
Security level can be expressed as: L= (C,G), and C<br />
is security grade, and G is the group of set. Two security<br />
level: L1= (C1,G1) 、L2= (C2,G2) .If and only if C1<br />
≥ C2 and G1 include G2, L1 ≥ L2 is correct.<br />
All operation of subject to object are abided by simplesecurity<br />
property and *_ property principle:<br />
(1) When Ls≥ Lo, subject S can read object O, and it<br />
is called down-read.<br />
(2) When Ls≤ Lo, subject S can write object O, and it<br />
is called up-write.<br />
Audit function is enhanced in the search system based<br />
on database. All operation related events are audited, and<br />
they increase the security of the search system.<br />
LogicSQL-based Enterprise search system achieves<br />
more accurate positioning information, and it realizes the<br />
value from the information across to the knowledge.<br />
ACKNOWLEDGMENT<br />
The authors wish to thank Wang Baohua. This work<br />
was supported in part by a grant from the Industrial<br />
Research Project of Guizhou Province under (Grant No.<br />
[2008]5014) and the Science and Technology Funds of<br />
Guizhou Province (Grant No.[2009]2125), the Stadholder<br />
Foundation of Guizhou Province (Grant No. 2009-111),<br />
and the Funds of Chongqing University of Arts and<br />
Sciences(Grant No. Y2009JS57, 68 and 69).<br />
REFERENCES<br />
[1] ORACLE DATA SHEET, Oracle Ultra Search,<br />
http://www.oracle.com/index.html, February 2010.<br />
[2] Enterprise Portal Overview and User Guide, Sybase<br />
Enterprise Portal, LAST REVISED: May 2000.<br />
[3] Yuan Liyan, ShiFang Enterprise Information Real-Time<br />
Archive and Search System. http://www.shifang. com.cn/p<br />
roducts, July 2009.<br />
[4] Internet Search, http://home.mcom.com/home/ internetsearch.html,<br />
February 2010.<br />
[5] Search Engines Guide, http://www.searchengineguide.com<br />
/searchengines.html, February 2010.<br />
[6] http://en.wikipedia.org/wiki/Enterprise_search, February<br />
2010.<br />
[7] Differences Between Internet vs. Enterprise Search, Last<br />
Updated Feb 2009.http://www.ideaeng.com/tabId/98/itemI<br />
d/154/20-Differences-Between-Internet-vs-Enterprise- Se.<br />
aspx#sec, February 2010.<br />
[8] Yuan Liyan. The Documentation of Logic SQL [ M ].<br />
Alberta University Press, Canada. 2005, pp.1-15<br />
[9] Baohua Wang, Danning Li, Zhengyong Zhao, Xinqiang<br />
Ma,Dan Li. Research and Realization of Enterprise<br />
Security Search Application System Based on Database.<br />
Journal of Computational Information Systems.<br />
Vol.3(5).1841-1846. 2007.10.<br />
Figure 1. Web crawler architecture<br />
241